
[ad_1]
Enterprise e mail compromises, which supplanted ransomware final yr to turn into the highest financially motivated assault vector-threatening organizations, are more likely to turn into more durable to trace. New investigations by Irregular Safety recommend attackers are utilizing generative AI to create phishing emails, together with vendor impersonation assaults of the sort Irregular flagged earlier this yr by the actor dubbed Firebrick Ostricth.
In response to Irregular, through the use of ChatGPT and different giant language fashions, attackers are capable of craft social engineering missives that aren’t festooned with such crimson flags as formatting points, atypical syntax, incorrect grammar, punctuation, spelling and e mail addresses.
The agency used its personal AI fashions to find out that sure emails despatched to its clients later recognized as phishing assaults had been in all probability AI-generated, in response to Dan Shiebler, head of machine studying at Irregular. “Whereas we’re nonetheless doing a whole evaluation to know the extent of AI-generated e mail assaults, Irregular has seen a particular improve within the variety of assaults with AI indicators as a proportion of all assaults, notably over the previous few weeks,” he stated.
Bounce to:
Utilizing fake Fb violations as lure
A brand new tactic famous by Irregular entails spoofing official Fb notifications informing the goal that they’re “in violation of group requirements” and that their web page has been unpublished. The consumer is then requested to click on on a hyperlink and file an enchantment, which results in a phishing web page to reap consumer credentials, giving attackers entry to the goal’s Fb Web page, or to promote on the darkish internet (Determine A).
Determine A
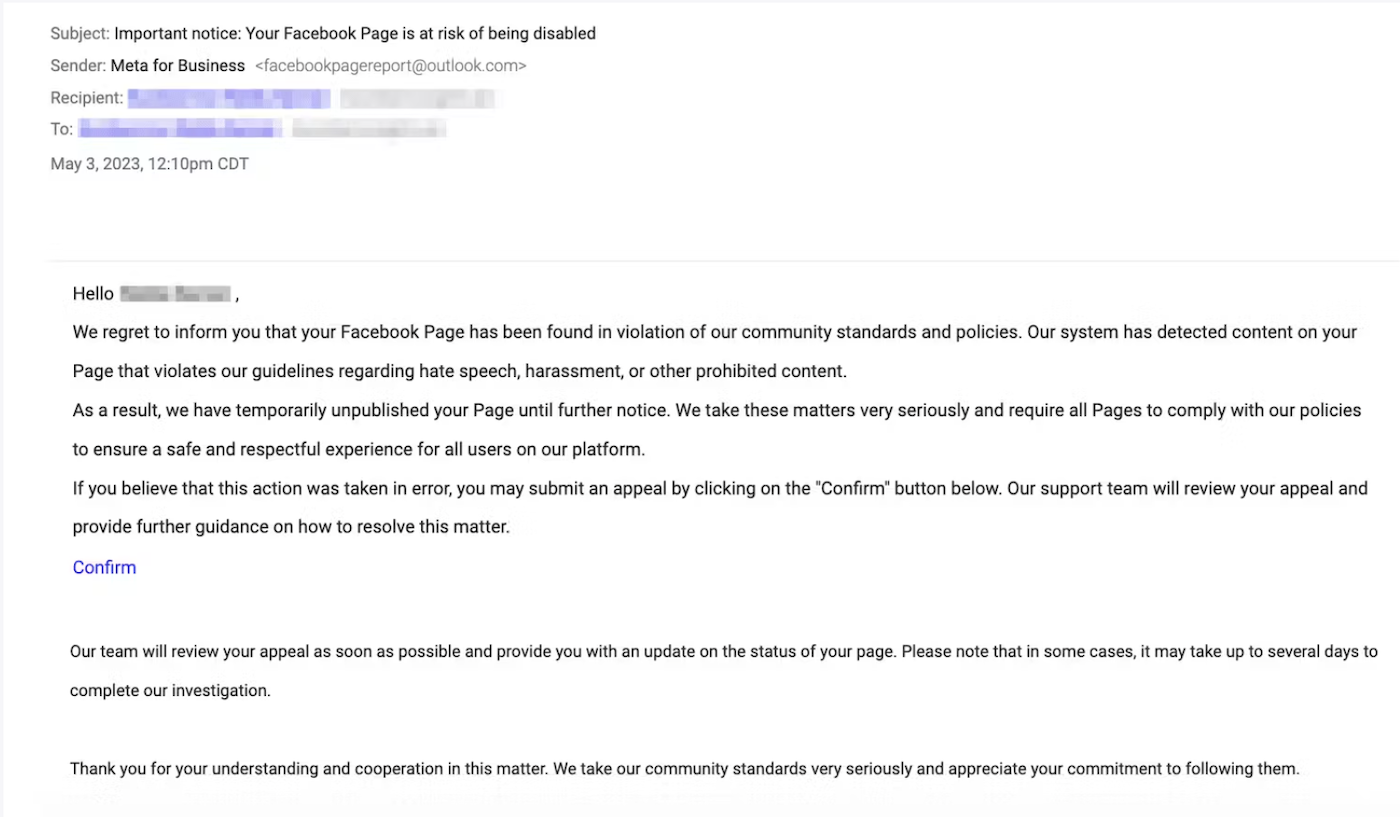
Shiebler stated the truth that the textual content inside the Fb spoofs is almost equivalent to the language anticipated from Meta for Enterprise means that much less refined attackers will be capable of simply keep away from the same old phishing pitfalls.
“The hazard of generative AI in e mail assaults is that it permits risk actors to jot down more and more refined content material, making it extra doubtless that their goal will probably be deceived into clicking a hyperlink or following their directions,” he stated, including that AI can be used to create better personalization.
“Think about if risk actors had been to enter snippets of their sufferer’s e mail historical past or LinkedIn profile content material inside their ChatGPT queries. Emails will start to point out the standard context, language, and tone the sufferer expects, making BEC emails much more misleading,” he stated.
Seems like a phish however could also be a dolphin
In response to Irregular, one other complication in detecting phishing exploits that used AI to craft emails entails false optimistic findings. As a result of many reputable emails are constructed from templates utilizing frequent phrases, they are often flagged by AI due to their similarity to what an AI mannequin would additionally generate, famous Shiebler who stated analyses do give some indication that an e mail might have been created by AI, “And we use that sign (amongst hundreds of others) to find out malicious intent.”
AI-generated vendor compromise, bill fraud
Irregular discovered cases of enterprise e mail compromises constructed by generative AI to impersonate distributors, containing invoices requesting fee to an illegitimate fee portal.
In a single case that Irregular flagged, attackers impersonated an worker’s account on the goal firm and used it to ship a faux e mail to the payroll division to replace the direct deposit info on file.
Shiebler famous that, in contrast to conventional BEC assaults, AI-generated BEC salvos are written professionally. “They’re written with a way of ritual that will be anticipated round a enterprise matter,” he stated. “The impersonated lawyer can be from a real-life regulation agency—a element that offers the e-mail an excellent better sense of legitimacy and makes it extra more likely to deceive its sufferer,” he added.
Takes one to know one: Utilizing AI to catch AI
Shiebler stated that detecting AI authorship entails a mirror operation: operating LLM-generated e mail texts by means of an AI prediction engine to investigate how doubtless it’s that an AI system will choose every phrase in an e mail.
Irregular used open-source giant language fashions to investigate the likelihood that every phrase in an e mail might be predicted given the context to the left of the phrase. “If the phrases within the e mail have persistently excessive chance (that means every time period is very aligned with what an AI mannequin would say, extra so than in human textual content), then we classify the e-mail as presumably written by AI,” he stated. (Determine B).
Determine B
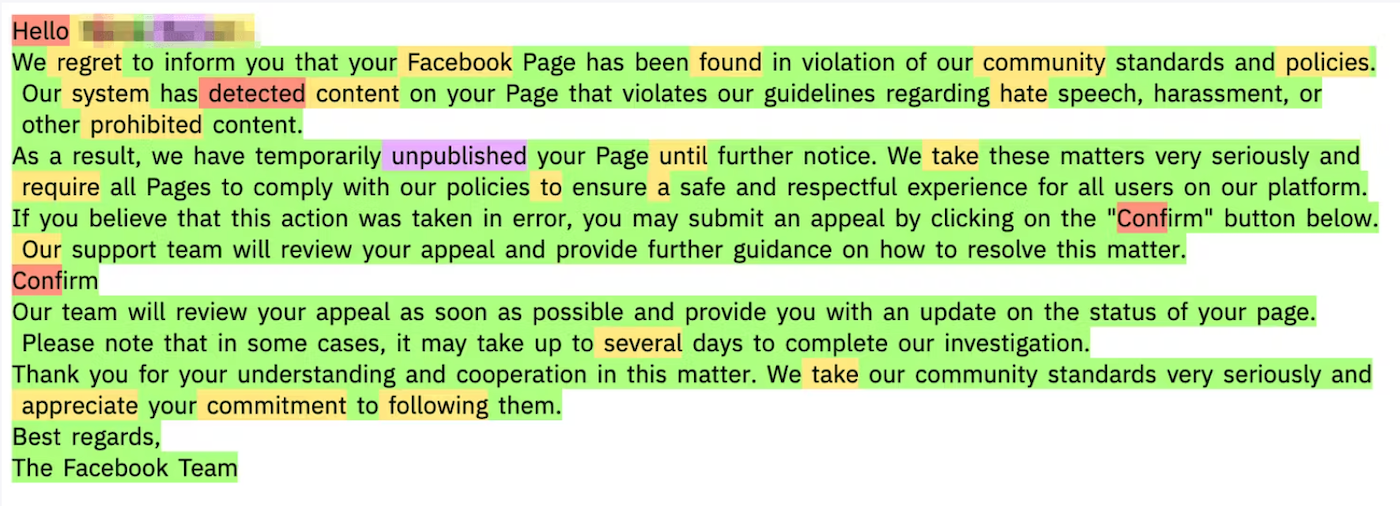
Shiebler warned that as a result of there are lots of reputable use circumstances the place staff use AI to create e mail content material, it isn’t pragmatic to dam all AI-generated emails on suspicion of malice. “As such, the truth that an e mail has AI indicators have to be used alongside many different alerts to point malicious intent,” he stated, including that the agency does additional validation through such AI detection instruments as OpenAI Detector and GPTZero.
“Respectable emails can look AI-generated, corresponding to templatized messages and machine translations, making catching reputable AI-generated emails tough. When our system decides whether or not to dam an e mail, it incorporates a lot info past whether or not AI might have generated the e-mail utilizing identification, habits, and associated indicators.”
Tips on how to fight AI phishing assaults
Irregular’s report instructed organizations implement AI-based options that may detect extremely refined AI-generated assaults which are almost inconceivable to tell apart from reputable emails. They have to additionally see when an AI-generated e mail is reputable versus when it has malicious intent.
“Consider it pretty much as good AI to combat dangerous AI,” stated the report. The agency stated that one of the best AI-driven instruments are capable of baseline regular habits throughout the e-mail atmosphere — together with typical user-specific communication patterns, types, and relationships versus simply in search of typical (and protean) compromise indicators. Due to that, they will detect the anomalies that will point out a possible assault, regardless of if the anomalies had been created by a human or AI.
“Organizations must also observe good cybersecurity hygiene, together with implementing steady safety consciousness coaching to make sure staff are vigilant about BEC dangers,” stated Sheibler. “Moreover, implementing ways like password administration and multi-factor authentication will make sure the group can restrict additional injury if any assault succeeds.”
[ad_2]