[ad_1]
The menace actor often known as ChamelGang has been noticed utilizing a beforehand undocumented implant to backdoor Linux techniques, marking a brand new enlargement of the menace actor’s capabilities.
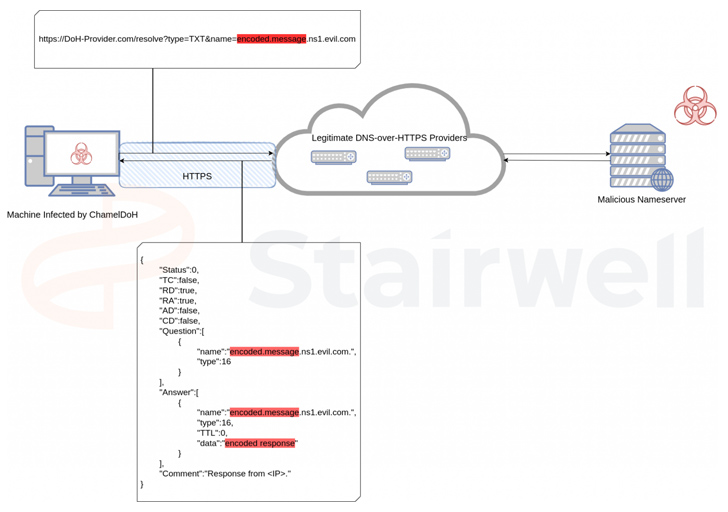
The malware, dubbed ChamelDoH by Stairwell, is a C++-based software for speaking through DNS-over-HTTPS (DoH) tunneling.
ChamelGang was first outed by Russian cybersecurity agency Constructive Applied sciences in September 2021, detailing its assaults on gas, power, and aviation manufacturing industries in Russia, the U.S., India, Nepal, Taiwan, and Japan.
Assault chains mounted by the actor have leveraged vulnerabilities in Microsoft Change servers and Crimson Hat JBoss Enterprise Utility to realize preliminary entry and perform information theft assaults utilizing a passive backdoor referred to as DoorMe.
“It is a native IIS module that’s registered as a filter via which HTTP requests and responses are processed,” Constructive Applied sciences mentioned on the time. “Its precept of operation is uncommon: the backdoor processes solely these requests wherein the proper cookie parameter is ready.”
The Linux backdoor found by Stairwell, for its half, is designed to seize system data and is able to distant entry operations akin to file add, obtain, deletion, and shell command execution.
What makes ChamelDoH distinctive is its novel communication methodology of utilizing DoH, which is used to carry out Area Identify System (DNS) decision through the HTTPS protocol, to ship DNS TXT requests to a rogue nameserver.
“As a result of these DoH suppliers being generally utilized DNS servers [i.e., Cloudflare and Google] for reliable site visitors, they can’t simply be blocked enterprise-wide,” Stairwell researcher Daniel Mayer mentioned.
Using DoH for command-and-control (C2) additionally affords further advantages for the menace actor in that the requests can’t be intercepted by way of an adversary-in-the-middle (AitM) assault owing to the usage of the HTTPS protocol.
🔐 Mastering API Safety: Understanding Your True Assault Floor
Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in the direction of ironclad safety. Be a part of our insightful webinar!
This additionally implies that safety options can’t determine and prohibit malicious DoH requests and sever the communications, thereby turning it to an encrypted channel between a compromised host and the C2 server.
“The results of this tactic is akin to C2 through area fronting, the place site visitors is distributed to a reliable service hosted on a CDN, however redirected to a C2 server through the request’s Host header – each detection and prevention are troublesome,” Mayer defined.
The California-based cybersecurity agency mentioned it detected a complete of 10 ChamelDoH samples on VirusTotal, one in all which was uploaded again on December 14, 2022.
The newest findings present that the “group has additionally devoted appreciable effort and time to researching and growing an equally sturdy toolset for Linux intrusions,” Mayer mentioned.
[ad_2]