
[ad_1]

Cybersecurity budgets are up after enduring price range cuts and financial uncertainties, Forrester’s latest report reveals. Nonetheless, corporations are struggling to fight cybersecurity threats and maintain their corporations secure.
Scale’s Cybersecurity Views 2023 report reveals that the majority companies (71%) are experiencing three or extra safety incidents, a 51% enhance in comparison with 2022. Safety groups battle with expertise gaps, are overwhelmed by alerts, and might’t discover the best instruments, regardless of safety budgets growing by 20% on common in giant enterprises and 5% in mid-sized enterprises.
The issue appears to be inadequate funding, however for Ira Winkler, chief info safety officer at CYE Safety, it boils all the way down to how cybersecurity budgets are decided and assigned. CYE is a SaaS platform and presents skilled consulting for safety leaders to maximise cybersecurity methods and investments.
On July 20, I attended the Northeast Digital Cybersecurity Summit to achieve insights into new strategies that can be utilized to efficiently change the way in which cybersecurity budgets are allotted.
Bounce to:
Shifting outdated mindsets to business-driven fashions
On the summit, Winkler defined that the cybersecurity trade has shifted from defending software program and {hardware} underneath an info assets administration strategy to defending the data that strikes by way of techniques with the emergence of chief info safety officers. Nevertheless, corporations nonetheless allocate cybersecurity budgets with an outdated mindset.
Cybersecurity economics, cybersecurity valuations and risk-approach fashions are rising fields that may quantify dangers, countermeasures and return on funding to maximise system safety and decrease losses. Nevertheless, they’re poorly understood and never utilized.
- Cybersecurity economics is the research of the financial prices and advantages of cybersecurity. It goals to know how organizations could make optimum funding choices in cybersecurity given the dangers they face.
- Cybersecurity valuations are the strategies used to estimate the worth of cybersecurity belongings, which could embody knowledge, techniques and networks.
- Threat-approach fashions are used to guage a risk’s dangers and their penalties. Various factors are thought of in danger modeling, together with the chance of a cyberattack, the potential affect of a cyberattack and the price of mitigating the dangers.
“What does a ransomware incident price?” Winkler requested attendees. “Most individuals don’t actually know. And extra importantly, in cybersecurity, we don’t know the way a lot a non-incident prices us. We don’t monitor how effectively we cease issues in any respect, for essentially the most half. And that’s a elementary lack of enterprise self-discipline and enterprise thought processes.”
Winkler defined that this lack of a enterprise strategy is exclusive to cybersecurity departments. Different areas, equivalent to finance and accounting, provide chains and operations and manufacturing, don’t allocate budgets arbitrarily. For instance, trendy factories often have a full understanding of what a selected downtime prices and what the worth is when the manufacturing facility is up and working.
In a data-driven period, cybersecurity groups should have perception into outages, incidents and another issue that impacts efficiency and the corporate’s backside line. With this info, executives could make data-driven choices on budgets based mostly on financial affect, dangers and losses versus ROI and positive aspects.
Getting buy-in from executives and boards
It’s no secret that one of many greatest challenges CISOs and different safety leaders face is getting buy-in from boards and executives. Moreover, safety groups face elevated stress from boards as their roles and obligations broaden.
Within the newest ClubCISO Report 2023, 62% of CISOs surveyed listed management endorsement as essentially the most essential think about fostering a greater safety tradition. Regardless of elevated alignment between safety groups, executives and boards, 20% of these surveyed nonetheless say that the dearth of buy-in and assist impacts their corporations’ safety.
“Sadly, in cybersecurity, we now have individuals who don’t know the best way to talk about budgets with administration,” Winkler mentioned.
In response to Winkler, so long as safety leaders don’t take extra scientific and enterprise approaches to budgeting, they’ll all the time obtain random allocations and get undesirable outcomes. When pitching executives for buy-in, safety leaders should be effectively knowledgeable on acceptable danger ranges, how efficient their countermeasures are and what the highest vulnerabilities price them.
Winkler mentioned that solely budgets that decrease dangers and potential losses needs to be offered to administration. When a board or an govt suggests slicing a price range, the safety workforce should know the way a lot that reduce will price the corporate. This methodology presents higher info to executives, permitting them to make higher choices, and helps get buy-in. It additionally relieves safety leaders of obligations as they inform firm administration concerning the dangers earlier than they occur.
“Understanding the best way to current cybersecurity applications in enterprise phrases is the best method to get the price range you want,” Winkler instructed the viewers of safety specialists.
Privateness breaches; compliance points; U.S., EU and worldwide legal guidelines; insurance coverage prices; fines; and outages pushed by pure disasters must also be included into safety applications, in response to Winkler.
ROI-driven cybersecurity budgets
Cyber-risk quantification isn’t a brand new idea, however risk-approach fashions are nonetheless of their infancy. Whereas organizations like Gartner report on its elevated adoption and high distributors like Bitsight, SecurityScorecard, Corax, UpGuard and Squalify supply it, implementing all of it might be overwhelming.
Winkler assured that risk-approach fashions shouldn’t be overcomplicated. “That is the one diagram I’ve in my firm,” Winkler mentioned (Determine A).
Determine A
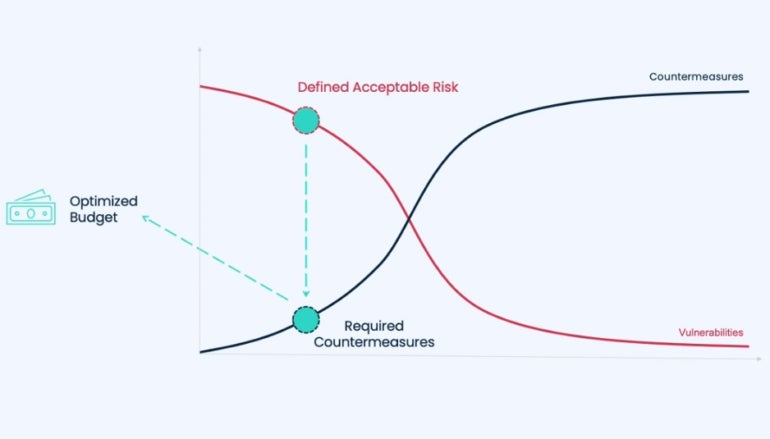
The red line within the graph represents an organization’s vulnerabilities, and the whole lot underneath the red line represents potential losses. When an organization begins risk-modeling with out countermeasures, vulnerabilities and potential losses are at their most; as countermeasures are applied and elevated, potential losses start to go down. Nevertheless, Winkler defined that there’s a catch.
When managing dangers, most individuals assume an organization ought to add as many countermeasures as potential to succeed in a minimal worth of vulnerabilities and scale back potential losses to zero. Nevertheless, that isn’t the case as a result of the price of implementing the required countermeasures to carry vulnerabilities to a minimal is often exponentially greater than the price of vulnerabilities.
An organization doesn’t wish to see the price of its countermeasures greater than the price of its losses and in addition not equal to them. Reaching the best stability might be difficult.
“What you wish to do is determine what I name the danger optimization level,” Winkler defined. “And that’s the place primarily you determine the potential loss you’re prepared to simply accept after which what countermeasures are theoretically going to get you there.” The idea is very like long-term investments.
The problem for safety groups and executives alike is to simply accept that it doesn’t matter what they do, they’ll all the time face potential losses and dangers. Moreover, a company-wide tradition that has been assigning cybersecurity budgets for many years by merely including a 5% to twenty% enhance to the price range of the earlier 12 months should be modified.
Allocating “an arbitrary price range offers you arbitrary outcomes,” Winkler mentioned. He urged safety specialists on the occasion to map risk sources, belongings, vulnerabilities and potential losses to know their publicity. The cybersecurity skilled additionally offered a danger equation to elucidate how corporations can quantify elements, highlighting the disruptive energy of AI and machine studying to drive these mathematical calculations (Determine B).
Determine B

Closing ideas: Setting priorities
Setting priorities and implementing the very best worth of countermeasures that generate the very best ROI whereas analyzing the associated fee and likelihood of vulnerabilities could look like a rigged sport of numbers the place incidents and losses are certain to occur. Nevertheless, accepting minimal losses and incidents far outweighs different alternate options.
Conventional strategies used to allocate cybersecurity budgets have grow to be outdated, and the results related to some of these approaches are effectively documented in risk studies that present the yearly rising prices of threats.
Extra funding and extra instruments don’t essentially translate into extra safety. Safety assets should be correctly allotted, and the prices of every countermeasure resolution should be balanced towards the price of assaults.
Whereas different elements have to be thought of, equivalent to corporations’ moral obligations to guard every buyer, companion and system, a data-driven enterprise strategy to cybersecurity budgets can undoubtedly change the cybersecurity trade.
[ad_2]