
[ad_1]

PaperCut just lately mounted a essential safety vulnerability in its NG/MF print administration software program that enables unauthenticated attackers to realize distant code execution on unpatched Home windows servers.
Tracked as CVE-2023-39143, the flaw outcomes from a sequence of two path traversal weaknesses found by Horizon3 safety researchers that allow risk actors to learn, delete, and add arbitrary information on compromised programs following low-complexity assaults that do not require consumer interplay.
Whereas it solely impacts servers in non-default configurations the place the exterior system integration setting is toggled, Horizon3 stated in a report printed on Friday that the majority Home windows PaperCut servers have it enabled.
“This setting is on by default with sure installations of PaperCut, such because the PaperCut NG Industrial model or PaperCut MF,” Horizon3 stated.
“Primarily based on pattern information we’ve collected at Horizon3 from real-world environments, we estimate that the overwhelming majority of PaperCut installations are operating on Home windows with the exterior system integration setting turned on.”
You should use the next command to test if a server is susceptible to CVE-2023-39143 assaults and is operating on Home windows (a 200 response signifies the server wants patching):
curl -w "%{http_code}" -k --path-as-is "https://<IP>:<port>/custom-report-example/......deploymentsharpiconshome-app.png"
Admins who can’t instantly set up safety updates (as Horizon3 advises) can add solely the IP addresses that want entry to an allowlist utilizing these directions.
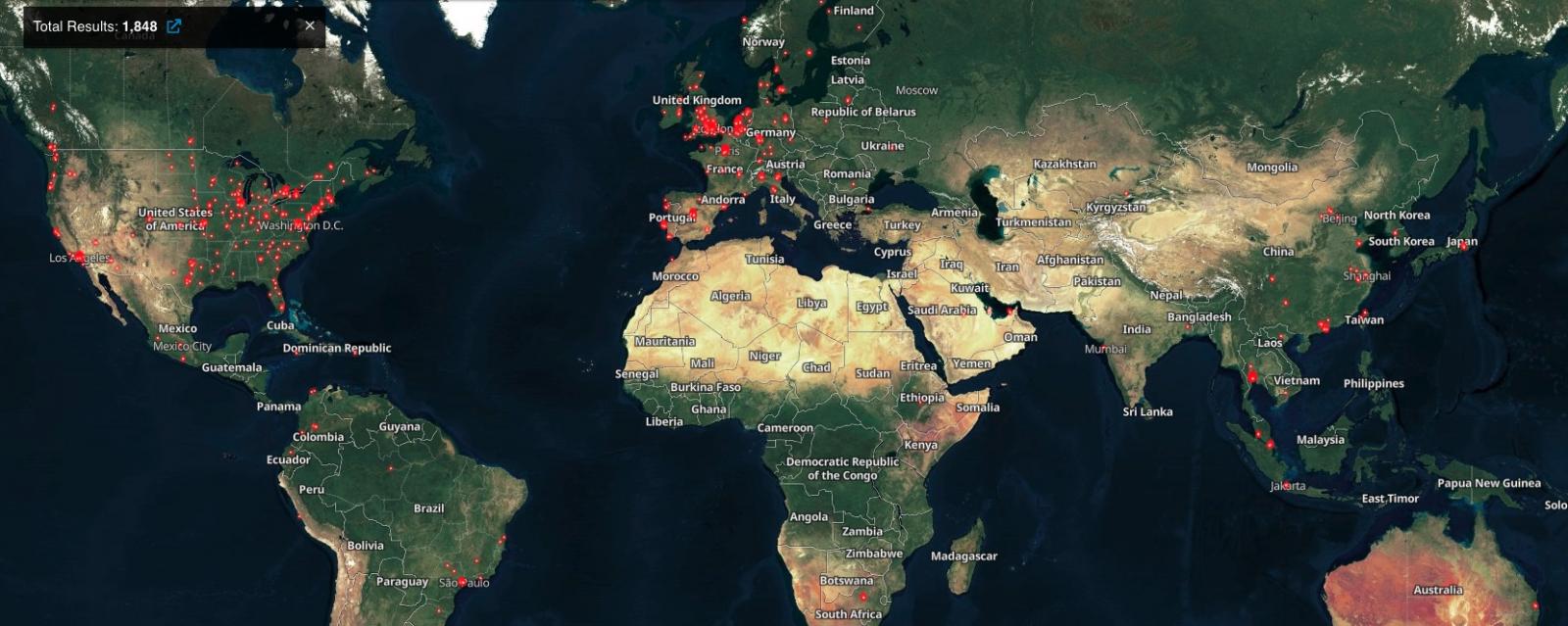
A Shodan search reveals that roughly 1,800 PaperCut servers are presently uncovered on-line, though not all are susceptible to CVE-2023-39143 assaults.
Focused by ransomware gangs, state hackers
PaperCut servers had been focused by a number of ransomware gangs earlier this yr by exploiting one other essential unauthenticated RCE vulnerability (CVE-2023–27350) and a high-severity data disclosure flaw (CVE-2023–27351).
The corporate disclosed on April nineteenth that these vulnerabilities had been being actively exploited in assaults, urging admins and safety groups to improve their servers urgently.
Just a few days after the preliminary disclosure, Horizon3 safety researchers launched an RCE Proof-of-Idea (PoC) exploit, opening the door for extra risk actors to focus on susceptible servers.
Microsoft linked the assaults focusing on PaperCut servers to the Clop and LockBit ransomware gangs, who used the entry to steal company information from compromised programs.
In these information theft assaults, the ransomware operation took benefit of the ‘Print Archiving‘ characteristic that saves all paperwork despatched by way of the PaperCut printing servers.
Nearly two weeks after, Microsoft revealed that Iranian state-backed hacking teams tracked as Muddywater and APT35 additionally joined the continuing assault.
CISA added the CVE-2023–27350 RCE bug to its record of actively exploited vulnerabilities on April twenty first, ordering all U.S. federal businesses to safe their servers by Might twelfth, 2023.
[ad_2]