
[ad_1]
Many safety professionals at present affiliate the Darkish Net with named leaks, that are leaked credentials from worker password reuse. That is nonetheless a related risk; within the final six years, the Flare platform has counted over 12 billion leaked credentials. The Darkish Net is quickly rising together with the number of cybercrime. So is the worth in monitoring it.
The cybercrime ecosystem not solely consists of personal communications platforms like I2P and Tor but in addition reaches throughout clear web sites and Telegram channels.
Darkish Net Monitoring: What to Watch For
There’s tangible worth in monitoring the Darkish Net for potential dangers. Following are among the threats you would possibly encounter.
Infostealer Malware
Stealer logs with company entry are seemingly one of the vital vectors for knowledge breaches and ransomware assaults at present.
Infostealer variants resembling RedLine, Raccoon, Vidar, Titan, and Aurora infect computer systems, then exfiltrate the browser fingerprint containing all of the saved passwords within the browser. Menace actors then promote the outcomes on Darkish Net marketplaces or Telegram channels.
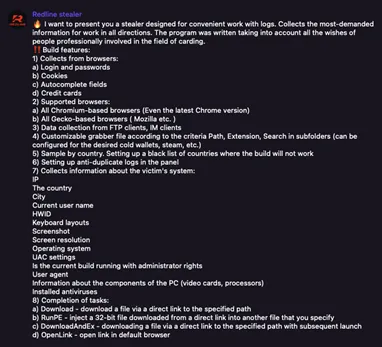
These logs are then used for account takeover assaults, stealing cryptocurrency, or as preliminary entry for ransomware assaults. Flare screens greater than 20 million infostealer logs and is including 1 million new logs per thirty days, a lot of which include credentials to a number of company purposes. We consider that someplace between 2% and 4% of logs include entry to company IT environments that might pose vital danger if compromised.
To detect malicious actors distributing stealer logs throughout the Darkish Net and Telegram, corporations can monitor for any logs that include an inner company area entry, resembling sso.companyname.com.
Preliminary Entry Brokers
Preliminary entry brokers (IABs) are lively throughout Darkish Net boards, resembling XSS and Exploit.in. IABs set up preliminary entry to corporations, which they resell in public sale and discussion board threads, usually for $10,000 to $500,000 per itemizing, relying on the corporate and stage of entry. A list often accommodates:
- Variety of units and providers compromised
- Business of the sufferer firm
- Antivirus or endpoint detection and response platform the corporate is utilizing
- Firm income
- Variety of staff
- Geographic location of firm
- Compromised hosts or servers
Menace actors should buy this entry and use it to deploy ransomware or steal delicate knowledge or monetary assets.
Monitoring IAB boards can present early warning that malicious actors have compromised units. IABs by no means record the precise firm identify however usually present sufficient element that in case your group is a sufferer, there’s a cheap likelihood you’ll be able to establish it.
IABs are additionally intentionally searching for out stealer logs to realize entry to IT infrastructure. An IAB might buy an contaminated machine for $10 from Russian Market, use the credentials to realize entry, escalate privileges, then record the entry on the market on Exploit.in with bids beginning at $20,000.
Ransomware Extortion and Information Breach Pages
Ransomware is not what it was. Ransomware teams have gotten decentralized, with many teams offering the supply code for ransomware and handing off the work of infecting corporations out to associates for a minimize of the ransom cost. As well as, the ubiquity of backup and restoration options has prompted many teams to completely ditch encryption and as a substitute give attention to knowledge exfiltration techniques involving knowledge theft and disclosure, concentrating on particular person staff, or concentrating on third events of the sufferer group,
One other disturbing pattern within the cybercriminal underground is ransomware extortion and knowledge breach blogs. Menace actors use these blogs to publicly disgrace and extort victims by threatening to leak delicate knowledge if they don’t pay ransom. This tactic has confirmed to be extremely efficient, as organizations concern the potential authorized and reputational penalties that might come up from an information breach.
As well as, some teams will launch recordsdata in batches, add timers counting all the way down to releasing delicate knowledge, and goal particular person staff to extend strain.
Because of this, many victims decide to pay the ransom, perpetuating the cycle of cybercrime and incentivizing additional assaults.
Your group would seemingly know if it was a sufferer of ransomware; nevertheless, many organizations endure knowledge publicity as a consequence of third-party breaches.
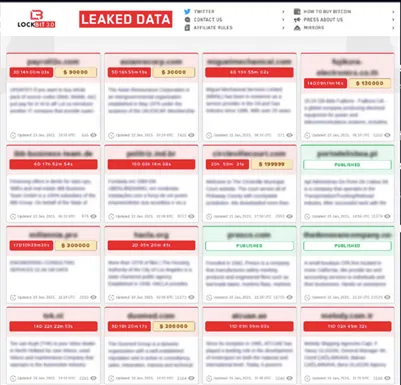
By proactively monitoring ransomware blogs resembling LockBit, you’ll be able to detect undesirable knowledge publicity from third events and quickly start incident response procedures.
Detect Darkish Net Threats
It is essential for organizations to have the ability to detect threats throughout the clear and Darkish Net and illicit Telegram channels. Search for an answer that integrates simply into your safety program and gives superior discover of potential high-risk publicity in a single platform.
You wish to establish high-risk vectors that might allow risk actors to entry your setting and conduct steady monitoring for contaminated units, ransomware publicity, public GitHub secrets and techniques, leaked credentials, and extra.
To be taught extra about utilizing Flare to detect Darkish Net threats, join a free trial.
Concerning the Writer:

Eric Clay has expertise throughout governance danger and compliance, safety knowledge evaluation, and safety analysis. He at the moment works because the VP of promoting at Flare, a Menace Publicity Administration SaaS answer.
[ad_2]