[ad_1]
A brand new malware marketing campaign has been noticed making use of malicious OpenBullet configuration recordsdata to focus on inexperienced cyber criminals with the aim of delivering a distant entry trojan (RAT) able to stealing delicate data.
Bot mitigation firm Kasada stated the exercise is designed to “exploit trusted felony networks,” describing it for instance of superior menace actors “preying on newbie hackers.”
OpenBullet is a reliable open-source pen testing device used for automating credential stuffing assaults. It takes in a configuration file that is tailor-made to a particular web site and may mix it with a password record procured by different means to log profitable makes an attempt.
“OpenBullet can be utilized with Puppeteer, which is a headless browser that can be utilized for automating net interactions,” the corporate stated. “This makes it very simple to launch credential stuffing assaults with out having to take care of browser home windows popping up.”

The configurations, primarily a bit of executable code to generate HTTP requests in opposition to the goal web site or net utility, are additionally traded, or bought inside felony communities, decreasing the bar for felony exercise and enabling script kiddies to mount their very own assaults.
“The curiosity within the buy of configs, for instance, may point out that the customers of OpenBullet are comparatively unsophisticated,” Israeli cybersecurity firm Cybersixgill famous again in September 2021.
“Nevertheless it is also one more instance of the darkish net’s extremely environment friendly division of labor. That’s, menace actors promote that they need to purchase configs as a result of they do not know the way to script them, however as a result of it is simpler and quicker.”
This flexibility may also be a double-edged sword, because it opens up a brand new vector, solely it targets different felony actors who’re actively in search of such configuration recordsdata on hacking boards.
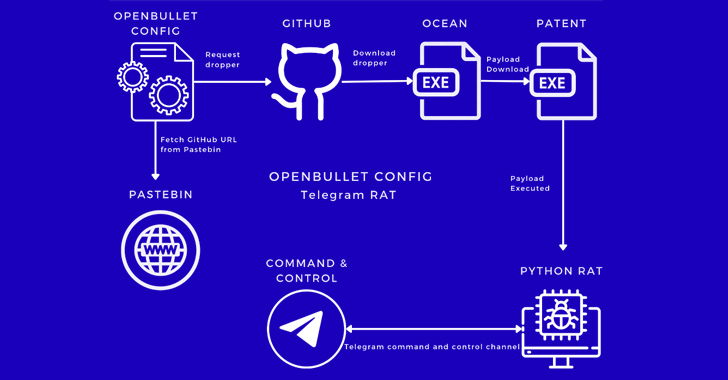
The marketing campaign found by Kasada employs malicious configs shared on a Telegram channel to succeed in out to a GitHub repository to retrieve a Rust-based dropper known as Ocean that is designed to fetch the next-stage payload from the identical repository.
The executable, a Python-based malware known as Patent, in the end launches a distant entry trojan that makes use of Telegram as a command-and-control (C2) mechanism and points directions to seize screenshots, record listing contents, terminate duties, exfiltrate crypto pockets data, and steal passwords and cookies from Chromium-based net browsers.

Focused browsers and crypto wallets embrace Courageous, Google Chrome, Microsoft Edge, Opera, Opera GX, Opera Crypto, Yandex Browser, Atomic, Sprint Core, Electron Money, Electrum, Electrum-LTC, Ethereum Pockets, Exodus, Jaxx Liberty, Litecoin Pockets, and Mincoin.
The trojan additionally capabilities as a clipper to watch the clipboard for cryptocurrency pockets addresses and substitute contents matching a predefined common expression with an actor-controlled handle, resulting in unauthorized fund transfers.
Two of the Bitcoin pockets addresses operated by the adversary have obtained a complete of $1,703.15 over the previous two months, which have been subsequently laundered utilizing an nameless crypto trade generally known as Mounted Float.
“The distribution of the malicious OpenBullet configs inside Telegram is a novel an infection vector, doubtless concentrating on these felony communities attributable to their frequent use of cryptocurrencies,” the researchers stated.
“This presents a chance for attackers to form their assortment to a particular goal group and procure different members’ funds, accounts, or entry. Because the outdated saying goes, there isn’t a honor amongst thieves.”
[ad_2]