
[ad_1]

Researchers from Italy and the UK have found 4 vulnerabilities within the TP-Hyperlink Tapo L530E sensible bulb and TP-Hyperlink’s Tapo app, which might enable attackers to steal their goal’s WiFi password.
TP-Hyperlink Tapo L530E is a top-selling sensible bulb on a number of marketplaces, together with Amazon. TP-link Tapo is a brilliant gadget administration app with 10 million installations on Google Play.

The researchers from Universita di Catania and the College of London analyzed this product because of its recognition. Nonetheless, the purpose of their paper is to underscore safety dangers within the billions of sensible IoT units utilized by shoppers, lots of which comply with dangerous information transmission and lackluster authentication safeguards.
Sensible bulb flaws
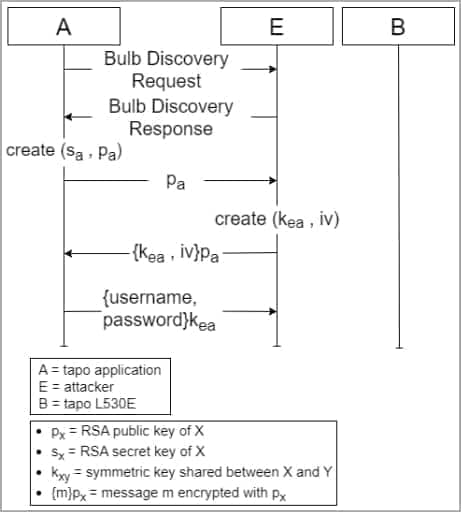
The primary vulnerability issues improper authentication on Tapo L503E, permitting attackers to impersonate the gadget throughout the session key trade step.
This high-severity vulnerability (CVSS v3.1 rating: 8.8) permits an adjoining attacker to retrieve Tapo person passwords and manipulate Tapo units.
The second flaw can also be a high-severity problem (CVSS v3.1 rating: 7.6) arising from a hard-coded quick checksum shared secret, which attackers can get hold of by way of brute-forcing or by decompiling the Tapo app.
The third drawback is a medium-severity flaw regarding the lack of randomness throughout symmetric encryption that makes the cryptographic scheme predictable.
Lastly, a fourth problem stems from the shortage of checks for the freshness of acquired messages, maintaining session keys legitimate for twenty-four hours, and permitting attackers to replay messages throughout that interval.
Assault eventualities
Essentially the most worrying assault state of affairs is bulb impersonation and retrieval of Tapo person account particulars by exploiting vulnerabilities 1 and a pair of.
Then, by accessing the Tapo app, the attacker can extract the sufferer’s WiFi SSID and password and acquire entry to all different units linked to that community.
The gadget must be in setup mode for the assault to work. Nonetheless, the attacker can deauthenticate the bulb, forcing the person to set it up once more to revive its perform.
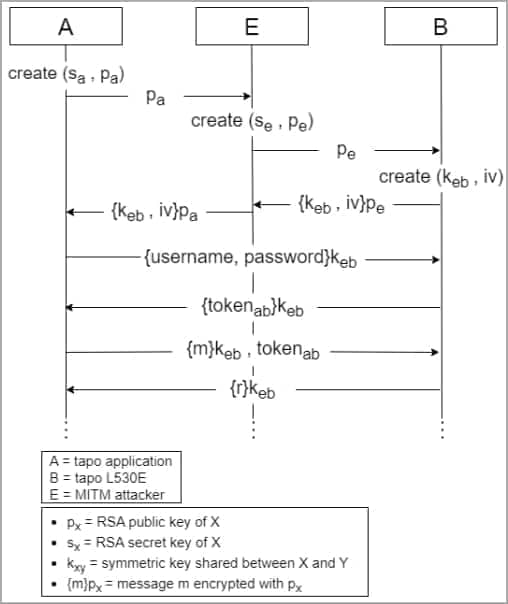
One other assault kind explored by the researchers is MITM (Man-In-The-Center) assault with a configured Tapo L530E gadget, exploiting vulnerability 1 to intercept and manipulate the communication between the app and the bulb and capturing the RSA encryption keys used for subsequent information trade.
MITM assaults are additionally potential with unconfigured Tapo units by leveraging vulnerability one once more by connecting to the WiFi throughout setup, bridging two networks, and routing discovery messages, ultimately retrieving Tapo passwords, SSIDs, and WiFi passwords in simply decipherable base64 encoded type.
Lastly, vulnerability 4 permits attackers to launch replay assaults, replicating messages which were sniffed beforehand to attain purposeful adjustments within the gadget.
Disclosure and fixing
The college researchers responsibly disclosed their findings to TP-Hyperlink, and the seller acknowledged all of them and knowledgeable them they might implement fixes on each the app and the bulb’s firmware quickly.
Nonetheless, the paper doesn’t make clear whether or not these fixes have already been made out there and which variations stay weak to assaults.
BleepingComputer has contacted TP-Hyperlink to study extra in regards to the safety updates and impacted variations and can replace this submit as quickly as we hear again.
As common recommendation for IoT safety, it is strongly recommended to maintain all these units remoted from vital networks, use the most recent out there firmware updates and companion app variations, and shield accounts with MFA and powerful passwords.
[ad_2]