
[ad_1]
Ransomware is on monitor to victimize extra organizations in 2023, whereas attackers quickly escalate their assaults to wreak widespread injury earlier than defenders may even detect an an infection.
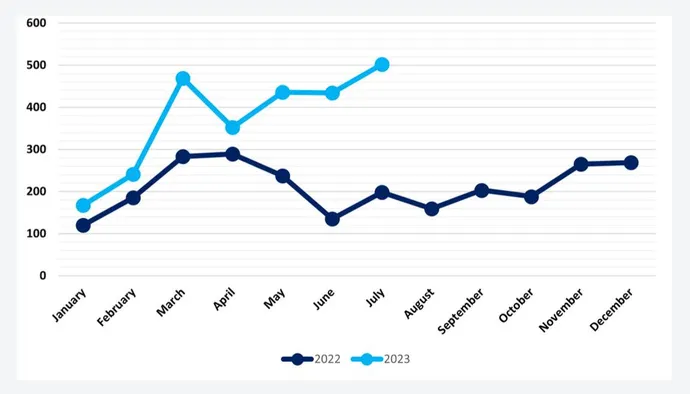
In July, knowledge from 502 compromises was posted to leak websites, a rise of greater than 150% in contrast with the identical month a 12 months in the past, in response to a report revealed on Aug. 23 by NCC Group, a safety consultancy. The expansion continues a rising development in 2023, with the variety of breaches publicized on the websites — now a standard tactic for double-extortion ransomware teams — rising 79% to this point, in contrast with the identical interval in 2022.
A convergence of things — reminiscent of current easy-to-exploit vulnerabilities in managed-file switch companies, reminiscent of MOVEit, and the rising quantity companies providing of preliminary entry — have led to the rise, says Matt Hull, international head of risk intelligence at NCC Group.
“Prison teams … are opportunistic in nature — they need to earn money and so they search for the simplest approach to make that cash,” he says. “So if there may be one other MOVEit in some unspecified time in the future this 12 months, or one thing much like that, I’ve little question in my thoughts that you will notice teams leaping on that bandwagon and seeing huge will increase in exercise.”
Different knowledge exhibits that ransomware criminals are shifting extra shortly to compromise corporations as soon as they’ve gained preliminary entry, with the typical dwell time in ransomware incidents shrinking to 5 days, from 9 days in 2022, in response to an evaluation of 80 incident response instances by Sophos, a cybersecurity firm. Different sorts of assaults are shifting slower, with non-ransomware attackers taking extra time, 13 days in contrast with 11 days in 2022, Sophos said in its midyear “Lively Adversary Report” evaluation.
The attackers are getting higher at what they do, honing their strategy of stealing and encrypting knowledge, says Chester Wisniewski, discipline CTO for utilized analysis at Sophos.
“While you take a look at a median dwell time of 5 days, that is smart [because it] takes that lengthy to do a full-scale, fashionable ransomware assault,” he says. “You have to discover a manner in, you bought to breach the Lively Listing and elevate your self to be an admin, you have obtained typically to disable the backups. … You are not going to actually get the dwell time a lot shorter than 4 or 5 days if you’ve obtained all these duties to do.”
Wipe and Launch
The conclusions from two separate reviews — each launched this week — underscore the continued risk that crypto-ransomware poses, even though some assault teams, such because the Cl0p group, are shifting away from encrypting knowledge to an easier theft-and-extortion scheme. Most teams proceed to pursue the technique often known as double extortion, which depends on the theft and encryption of information to persuade an organization to pay the ransom.
The economic sector in July continued to dominate the listing of victims whose knowledge had been posted to leak websites, in response to NCC Group’s “Cyber Risk Intelligence Report.” The patron cyclicals and expertise industries got here in a distant second and third place, respectively, with solely half the variety of breaches reported.
“What we’ve got seen throughout the industrial sector … we all know there may be much less regulation, we all know that there was much less spend on cybersecurity budgets during the last variety of years,” NCC Group’s Hull says. “While you examine that to, for instance, monetary companies, which had been a major goal for ransomware and prison teams 5 to 10 years in the past — they’ve virtually dropped off the face of the earth.”
Attackers additionally are inclined to shortly transfer laterally — typically known as “breakout” — particularly to compromise an Lively Listing servers, which may give them entry to most different assets within the inner community. The median time to compromise an Lively Listing server is about 16 hours, in response to Sophos’ incident abstract report.
“Establishing a foothold on an Lively Listing server enormously enhances the capabilities of an attacker,” the report said. “An AD server is often essentially the most highly effective and privileged asset inside a community, one which’s able to controlling id and insurance policies throughout a complete group. Attackers can siphon off extremely privileged accounts, create new ones, or disable legit ones.”
Lastly, attackers are utilizing time variations to their benefit, with most assaults occurring midweek however outdoors of enterprise hours, Sophos mentioned.
The Cl0p Issue
One specific group has accounted for a lot of the expansion: the Cl0p group. It has moved shortly to take advantage of vulnerabilities in two managed file switch platforms — attacking MOVEit in late Could and GoAnywhere MFT in early January — leading to a surge of profitable compromises. Nonetheless, the Cl0p ransomware group depends on straight theft and extortion now, stealing knowledge after which threatening to disclose it, if the sufferer doesn’t pay, says NCC’s Hull.
“We all know that a few of these teams aren’t utilizing what can be historically termed as ransomware — there is not any encryption of information,” he says. “And there may be been actually been — by some teams — a normal, if not full, shift from encrypting knowledge to concentrate on exfiltration of information.”
The Cl0p group posted thrice extra knowledge leaks on their leak websites than the second most profitable group, Lockbit 3.0, in response to NCC Group’s knowledge. The group’s success has resulted in a surge of posts to data-leak websites, which has pushed the NCC Group’s ransomware monitoring larger.
But even with out monitoring the Cl0p group’s endeavors, ransomware exercise has grown, Hull says. Ignoring Cl0p exercise, posts to data-leak websites nonetheless grew by 57% year-over-year, lower than the 79% general progress together with the extortion group, however nonetheless a big improve.
As well as, a summer season stoop in ransomware exercise in 2022 did not materialize this 12 months, presumably resulting from extra cybercriminals making an attempt to make ends meet throughout a world downturn, Hull says.
“With the downturn of the economic system final 12 months, there must be a manner for these prison teams to earn money,” he says. “They should … get their income again up, so there may be clearly some kind of drive to try this.”
[ad_2]