
[ad_1]
Authored by: Vallabh Chole and Yerko Grbic
On July twenty third, 2023, Elon Musk introduced that the social networking website, Twitter was rebranding as “X”. The information propelled Twitter and X to achieve headlines and turn into the highest trending subjects on widespread social media platforms.
Scammers pounced on this chance and began renaming numerous hacked YouTube and different social media accounts to “twitter-x” and “twitter fund” to advertise rip-off hyperlinks with new X branding.
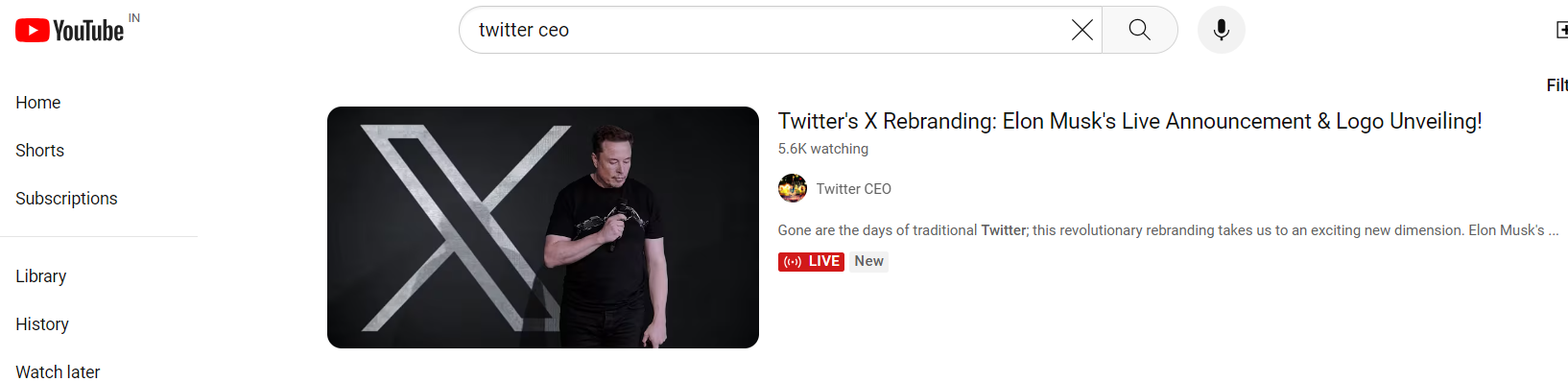
Determine 1. Twitter-X-themed YouTube Dwell Stream by scammer
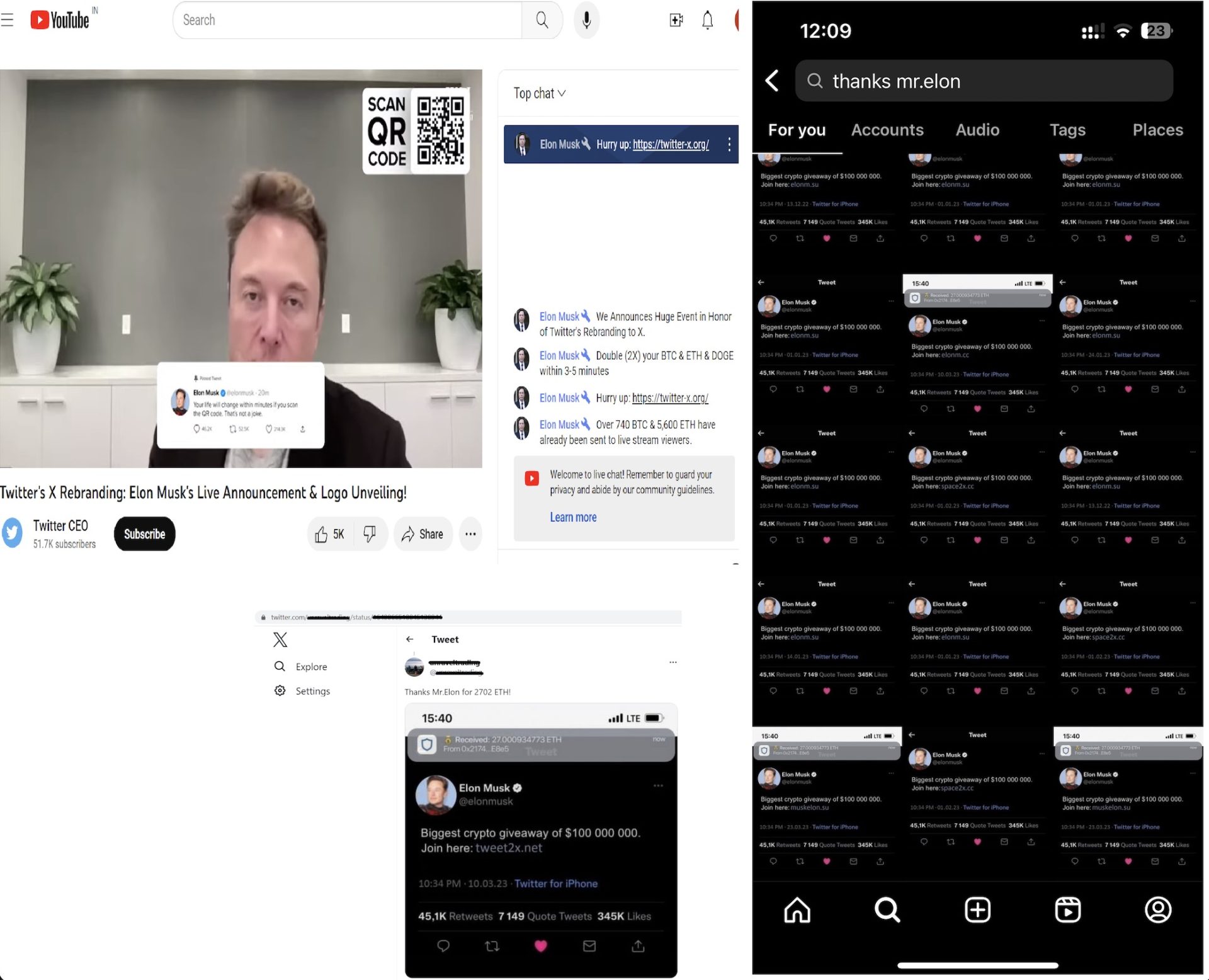
Determine 2. Twitter X Crypto Rip-off
This kind of rip-off has been lively for some time and makes use of an progressive method to lure victims. To make this rip-off extra genuine, attackers goal well-known Influencers with sponsorship emails that include password-stealing malware as e mail attachments. When password stealer malware is executed, the influencer’s session cookies (distinctive entry tokens) are stolen and uploaded to attacker-controlled programs.
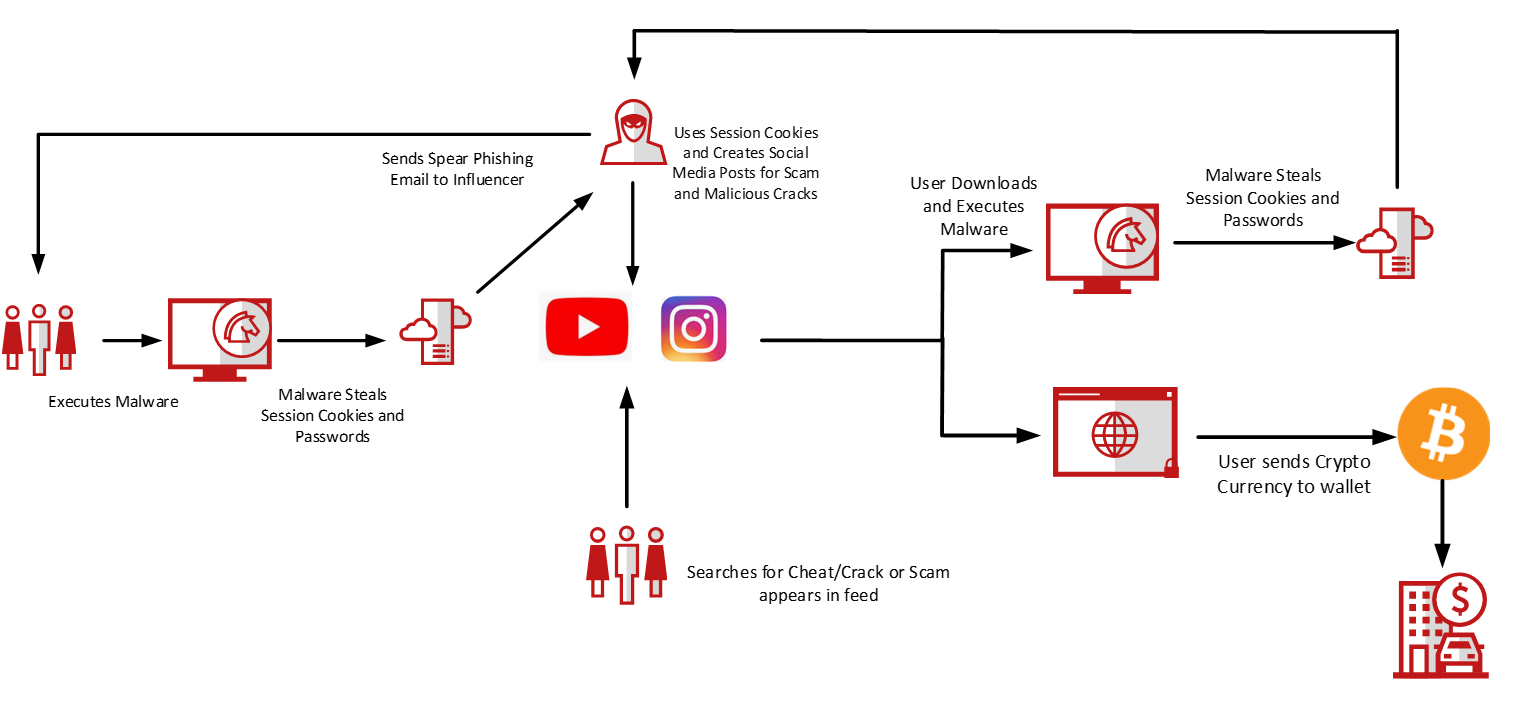
Determine 3. Malware Circulate Chart
After the influencer’s account has been compromised, the scammer begins to rename channels, on this case to “Twitter CEO” and then the scammers begin to reside stream an Elon Musk video on YouTube. They publish net hyperlinks for new rip-off websites in chat, and goal YouTube accounts with a massive variety of subscribers. On different social media platforms, corresponding to Instagram and Twitter, they use compromised accounts to comply with customers and publish screenshots with captions, corresponding to “Thanks Mr.Elon”. If we bathroomok for these phrases on Instagram, we observe 1000’s of comparable publishs. Compromised accounts are additionally used to publish movies for software program/recreation functions, that are malware masquerading as official software program or recreations. These movies display learn how to obtain and execute files, that are frequent password-stealing malware, and distributed by way of compromised social media accounts.
Safety with McAfee+:
McAfee+ offers all-in-one on-line safety in your identification, privateness, and safety. With McAfee+, you’ll really feel safer on-line since you’ll have the instruments, steering, and help to take the steps to be safer on-line. McAfee protects towards these kinds of rip-off websites with Internet Advisor safety that detects malicious web sites.
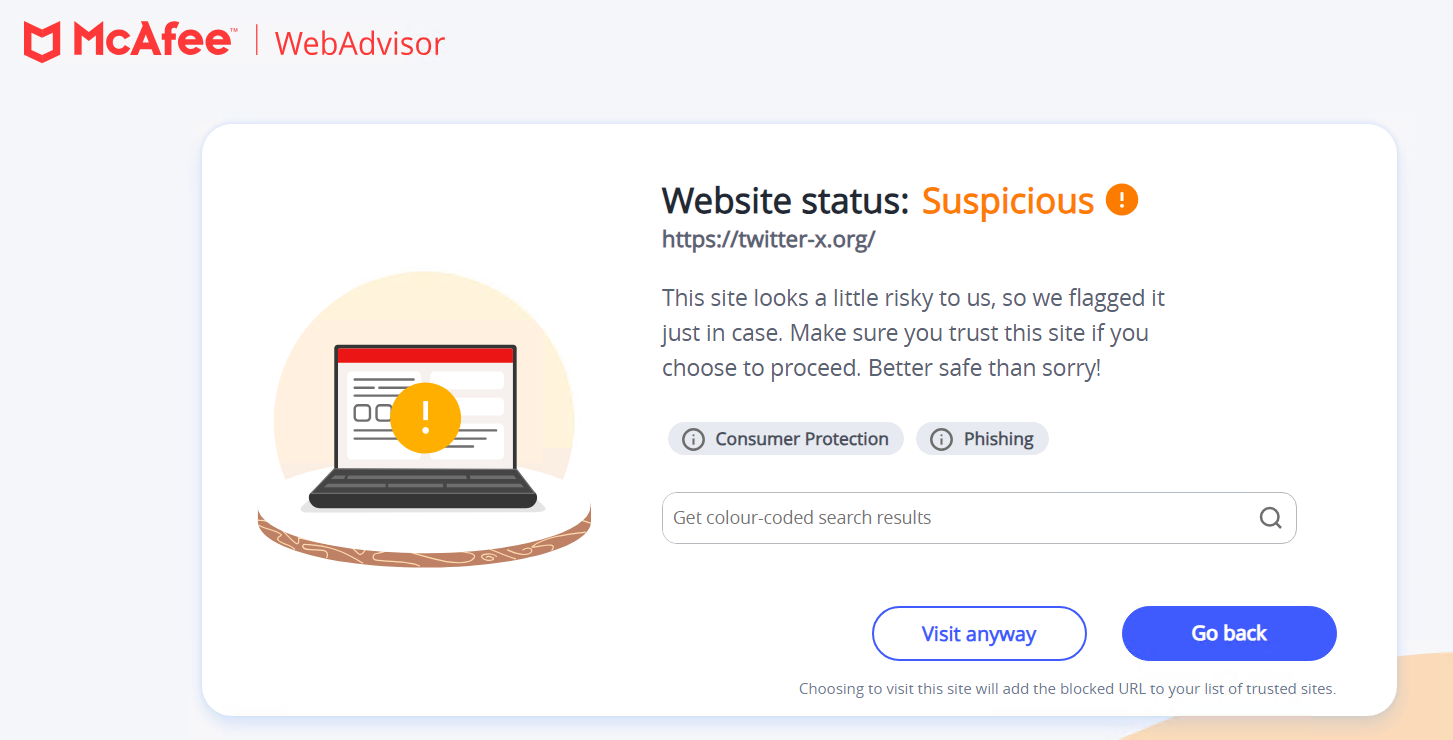
Determine 4. McAfee WebAdvisor detection
Under is a detection heatmap for rip-off URL’s focusing on twitter-x and selling crypto scams.
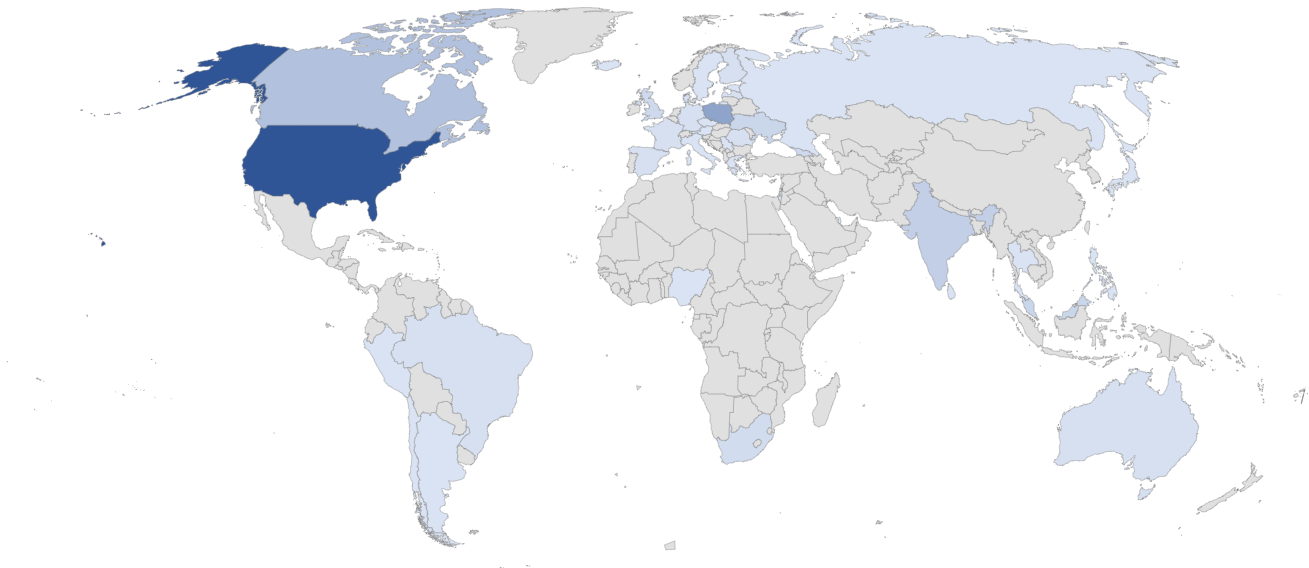
Determine 5. Rip-off URL Detection Heatmap
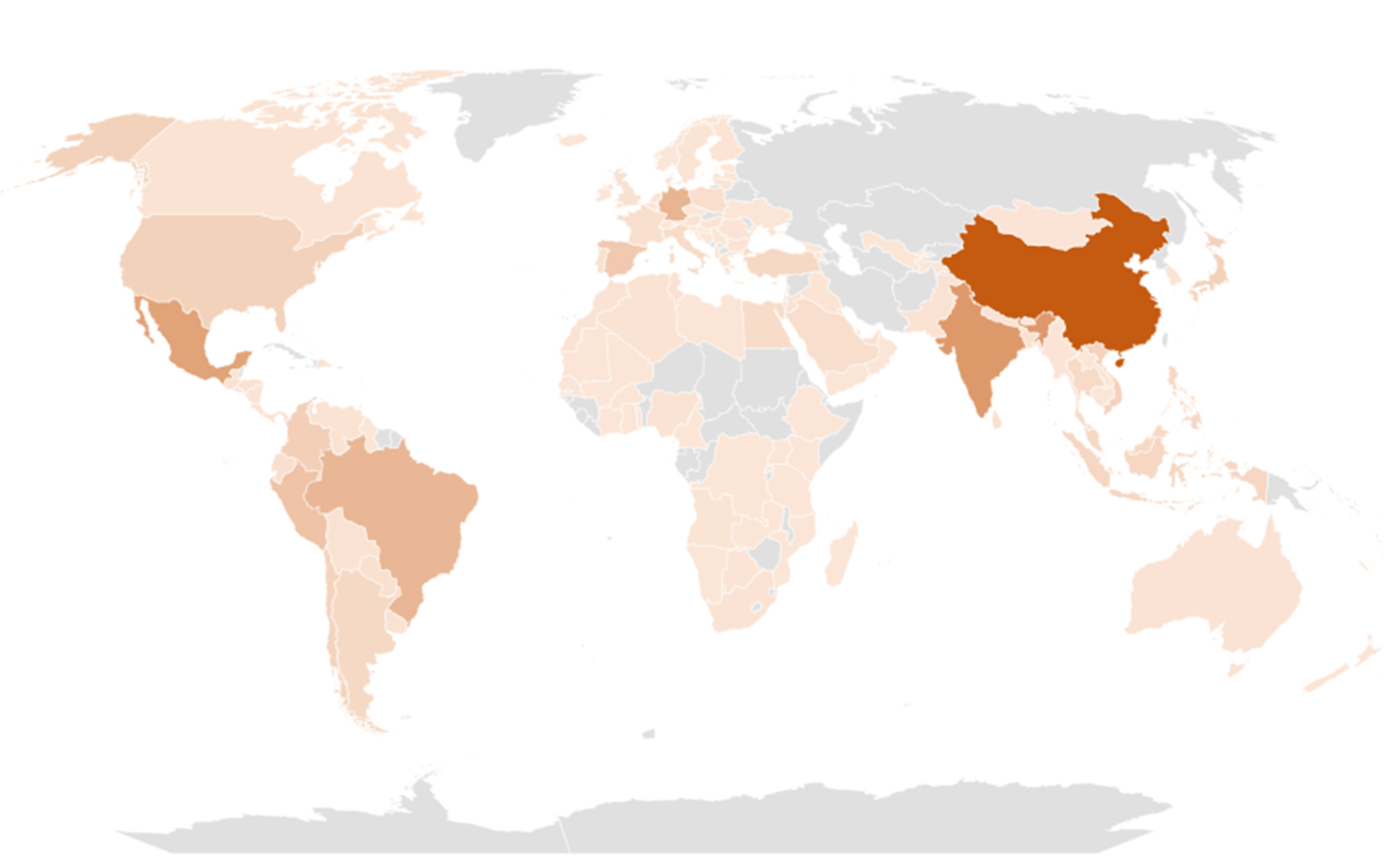
Determine 6. Password stealer Heatmap
Indicators of Compromise:
| Rip-off Web site | Crypto Sort | Pockets | |
| twitter-x[.]org | ETH | 0xB1706fc3671115432eC9a997F802aC79CD7f378a | |
| twitter-x[.]org | BTC | 1KtgaAjBETdcXiAdGsXJMePT4AEGWqtsug | |
| twitter-x[.]org | USDT | 0xB1706fc3671115432eC9a997F802aC79CD7f378a | |
| twitter-x[.]org | DOGE | DLCmD43eZ6hPxZVzc8C7eUL4w8TNrBMw9J |
[ad_2]
