[ad_1]
A brand new menace actor referred to as AtlasCross has been noticed leveraging Purple Cross-themed phishing lures to ship two beforehand undocumented backdoors named DangerAds and AtlasAgent.
NSFOCUS Safety Labs described the adversary as having a “excessive technical stage and cautious assault angle,” including that “the phishing assault exercise captured this time is a part of the attacker’s focused strike on particular targets and is its major means to attain in-domain penetration.”
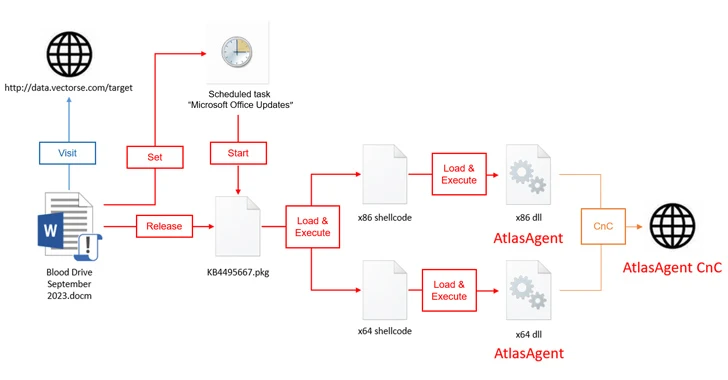
The assault chains begin with a macro-laced Microsoft doc that purports to be a couple of blood donation drive from the American Purple Cross that, when launched, runs the malicious macro to arrange persistence, exfiltrate system metadata to a distant server (information.vectorse[.]com) that is a sub-domain of a authentic web site belonging to a structural and engineering agency based mostly within the U.S.
Battle AI with AI — Battling Cyber Threats with Subsequent-Gen AI Instruments
Able to deal with new AI-driven cybersecurity challenges? Be a part of our insightful webinar with Zscaler to deal with the rising menace of generative AI in cybersecurity.
It additionally extracts a file named KB4495667.pkg (codenamed DangerAds), which, subsequently acts as a loader to launch shellcode that results in the deployment of AtlasAgent, a C++ malware able to gathering system info, shellcode operation, and working instructions to acquire a reverse shell in addition to inject code right into a thread within the specified course of.
Each AtlasAgent and DangerAds incorporate evasive options to make it much less prone to be found by safety instruments.
AtlasCross is suspected to have breached public community hosts by exploiting recognized safety vulnerabilities and turning them into command-and-control (C2) servers. NSFOCUS stated it recognized 12 totally different compromised servers within the U.S.
The true identification of AtlasCross and its backers presently stays a puzzle.
“At this present stage, AtlasCross has a comparatively restricted scope of exercise, primarily specializing in focused assaults towards particular hosts inside a community area,” the corporate stated. “Nevertheless, the assault processes they make use of are extremely sturdy and mature.”
[ad_2]