
[ad_1]
In 2014, an information breach uncovered data of three billion Yahoo customers. In 2016, Sony Footage workers noticed delicate non-public data leaked together with 1000’s of firm paperwork. What do these two assaults have in frequent? Each began with a phishing electronic mail.
E-mail threats are nonetheless one of the frequent methods attackers should entry delicate data or set up malware. Whereas most recognized instances of phishing goal nameless customers, the attackers may use emails containing pretend hyperlinks or information to focus on particular people who maintain delicate data. And, as ESET researchers level out, in 2022, this type of menace noticed a year-over-year enhance of just about 30%. And as AI language fashions make it simpler to compose emails, likelihood is that these numbers are nearly to go up much more!
Phishing assaults are a type of social engineering that makes us react with a way of urgency and curiosity. Whereas we will all be victims of the sort of assault, we will additionally be taught to keep away from it. Let’s check out some real-life examples of the commonest phishing used to trick us.
1. “Your session expired. Click on right here to sign up once more.”
Among the most typical phishing strains and techniques simply briefly inform you that you simply’ve been logged out of an account and it pushes you to fill in your credentials. Clicking the hyperlink will take you to a web site wanting similar to the actual one. The distinction, nonetheless, is that inputting your credentials will ship them straight away to the attackers, who will then use them to entry your data. In some situations, they may even log in for you and alter the password to keep away from supplying you with entry.
This system depends on the customers’ behavior of responding to such messages robotically with out enthusiastic about the content material or with out checking for the standard indicators of a phishing electronic mail/message. (Study these indicators right here).
For instance, final yr, GitHub Safety warned about emails impersonating the favored software program growth CI/CD platform CircleCI. The impersonators would ship an alert with “session expired” and request a brand new login utilizing GitHub credentials. “We have now seen some uncommon exercise in your account. Please confirm.”
With this trick, scammers attempt to whip up a way of urgency. Who wouldn’t need to keep away from the sudden lack of an account, proper? Normally, these emails impersonate messages from authentic companies corresponding to Amazon, PayPal, and so on.
For instance, in late 2018, The USA Federal Commerce Fee (FTC) issued a warning about phishing emails impersonating the streaming large Netflix. These emails claimed that an account was placed on maintain resulting from one thing fallacious with fee particulars, asking individuals to replace their billing data utilizing an embedded hyperlink, which was, after all, malicious and used to acquire login credentials.
Equally, Apple prospects have been focused in 2016 when scammers tried to steal their private data with phishing emails claiming that customers wanted to reconfirm their account particulars as a result of “a virus” had been present in Apple’s iTunes database.
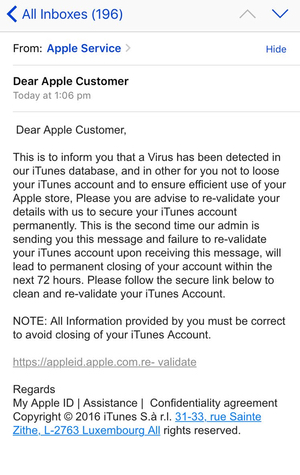
Spammed-out electronic mail
2. “I want you to make an pressing fee”
Impersonating company electronic mail accounts has been a long-time champion amongst spearphishing campaigns that don’t goal nameless individuals however as a substitute go after one particular individual or a gaggle of workers in a particular firm.
Earlier than sending these fraudulent emails, scammers be taught as a lot as doable about company buildings, visuals, language, and so on. of a enterprise, to make the phishing electronic mail nearly indistinguishable from a real one.
A few of these emails particularly goal workers who’re liable for money dealing with and monetary issues. They fake to be the CEO or a unique superior licensed to order a financial switch and ask the sufferer to ship funds to a selected account, supposedly the CEO’s, or perhaps the corporate’s.
In 2018, CEO impersonation was used to steal over CA$100,000 from the Canadian metropolis of Ottawa. Impersonating a request from the town supervisor, the town treasurer obtained a pretend electronic mail to switch the quantity that ended up within the pockets of fraudsters.
Grasping scammers additionally tried to deceive the treasurer for a second time, however when receiving one other electronic mail, the town supervisor was there to personally witness it. After asking whether or not the request was authentic, the rip-off was revealed, and the crooks have been caught in a lie.
3. “Expensive applicant…”
These phishing emails or messages depend on pretend job gives because the lure. They could trick potential victims into clicking on a phishing hyperlink or opening malicious information despatched together with an electronic mail message, asking the sufferer, for instance, to create an account and enter their private particulars as a method to use for the job.
As an example, the Lazarus menace group has run quite a few such campaigns, corresponding to Operation DreamJob, found by ESET researchers only recently, which lured its victims with pretend job gives.
These scams additionally exist on in style job promoting boards, so all the time attempt to confirm whether or not the headhunter who contacted you or the job give you see is authentic.
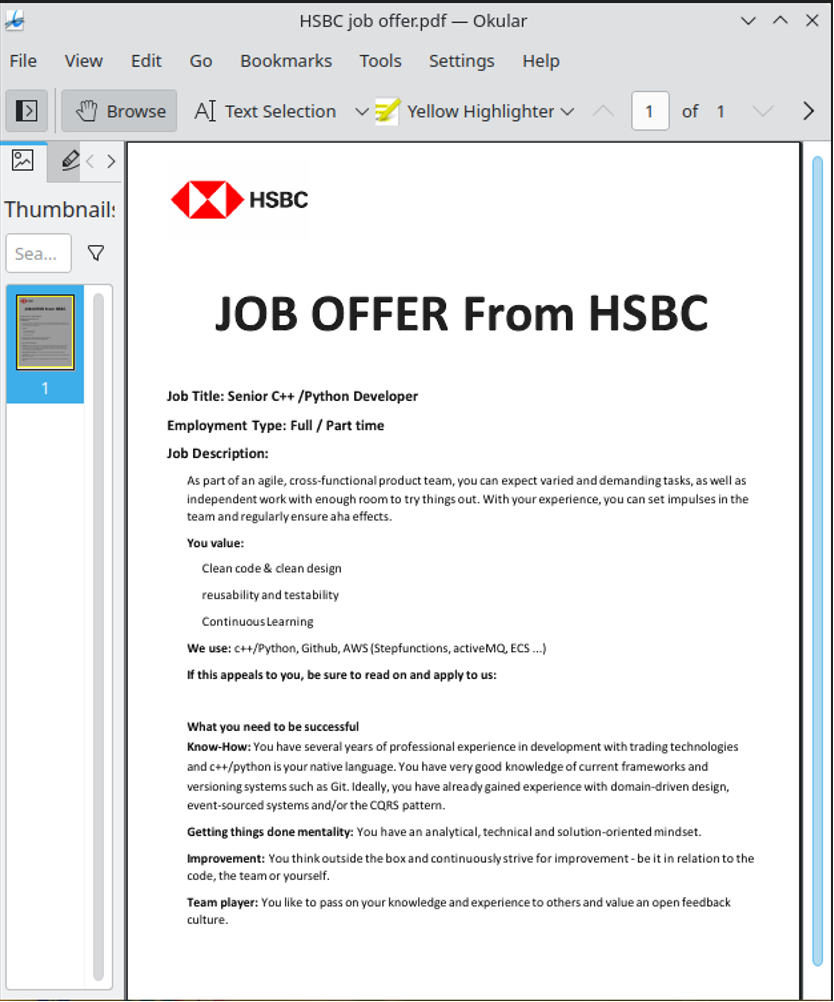
The most recent marketing campaign focused Linux customers with a ZIP file that delivers a pretend HSBC job supply as a decoy.
4. “Because of the present state of affairs… “
Phishing can be on the rise in instances of huge occasions – be it a sports activities occasion or a humanitarian disaster.
For instance, at first of 2023, the menace group Fancy Bear ran an electronic mail marketing campaign associated to the struggle in Ukraine. The emails have been carrying a malicious RTF file known as “Nuclear Terrorism A Very Actual Risk.” As soon as open, it might not solely compromise that laptop, but it surely was additionally a weblog by the respected assume tank Atlantic Council stating that the chance of Putin utilizing nuclear weapons within the struggle in Ukraine could be very low – the precise reverse of the declare within the doc title and that prompted the victims to open it.
5. “Merry Christmas!”
Scams throughout holidays typically abuse the purchasing spree with emails impersonating messages from authentic distributors. Emails include “too-good-to-be-true” gives or create a false sense of urgency to catch the last-minute deal!
One other strategy for scammers is to ship emails with malicious information associated to holidays, together with Christmas playing cards, present vouchers, and so on.
6. “We’re unable to course of your tax return”
Only some issues on this world are sure—demise, taxes, and phishing emails throughout tax season. As a result of persons are submitting their taxes, it isn’t stunning for them to obtain some electronic mail from a tax company.
Scammers abuse this example by sending phishing emails with pretend tax company messages. Normally, they declare that some data is lacking and request further private or monetary particulars.
Different emails supply a refund whereas asking for bank card data.
7. No response required
Some phishing emails have little to no content material, luring you to open an hooked up file to be taught extra concerning the matter.
For instance, ESET Analysis uncovered the malicious marketing campaign concentrating on company networks in Spanish-speaking international locations utilizing brief emails with PDF attachments in 2021.
The topic of the e-mail may be so simple as on this case: “Providers Assertion Dublin”; there was no message other than a signature and a cell phone contact in Venezuela.
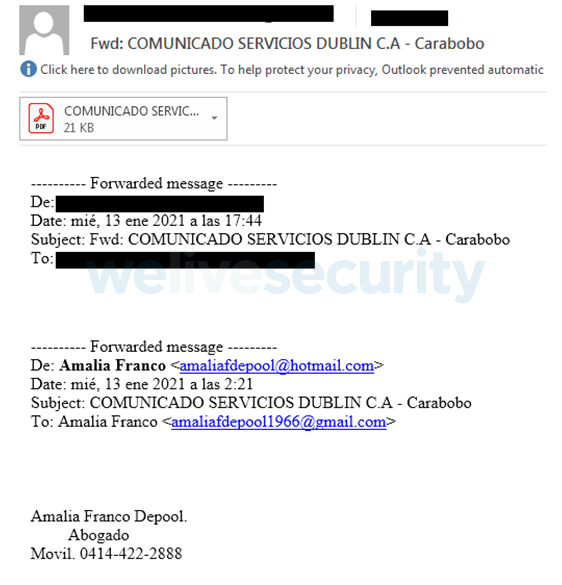
In the meantime, the attachment is an easy PDF file with no further informational worth, however contained a hyperlink redirecting victims to cloud storage companies, from which the malware could possibly be downloaded.
The best way to defend in opposition to phishing emails
- Fastidiously learn the e-mail. Don’t click on on something robotically.
- Examine whether or not the e-mail tackle matches the actual area.
- Be cautions with surprising sudden emails from a financial institution, vendor, or another group.
- Examine the crimson flag, corresponding to pressing or threatening emails requiring speedy response or requests for credentials, private, and monetary data. Quite a few grammar errors, spelling errors, and typos are additionally a crimson flag.
- Examine the hooked up URL with the respective area of a authentic firm or group. If you happen to spot something suspicious, don’t click on on it.
- Pay attention to gives which can be too good to be true and surprising items.
- Don’t ship cash swiftly. In case your superior out of the blue asks for such a switch, strategy them immediately.
- Set up a cybersecurity product with included anti-phishing instruments.
Phishing emails are a prevalent menace, and even IT professionals might fall for this rip-off. Fortunately, most of these emails are fairly simple to identify, in the event you management the urge to click on hyperlinks or open attachments earlier than confirming who’s the sender.
[ad_2]