
[ad_1]

Open directories are a extreme safety risk to organizations as they could leak delicate information, mental property or technical information that might enable an attacker to compromise your complete system. In response to new analysis from Censys, an web intelligence platform, greater than 2,000 TB of unprotected information, together with full databases and paperwork, are at present accessible in open directories world wide.
Leap to:
What are open directories, and the way can individuals discover them?
Open directories are folders which are accessible immediately through a browser and made obtainable by the net server. This occurs when an online server has been configured to supply a listing itemizing when no index file is discovered within the specified folder. Relying on the net server’s configuration, a consumer might or will not be allowed to see the folder’s content material. In response to Censys, the default conduct for many internet servers is to not render the listing itemizing.
Open directories seem with just a few variations relying on their internet server (Determine A).
Determine A
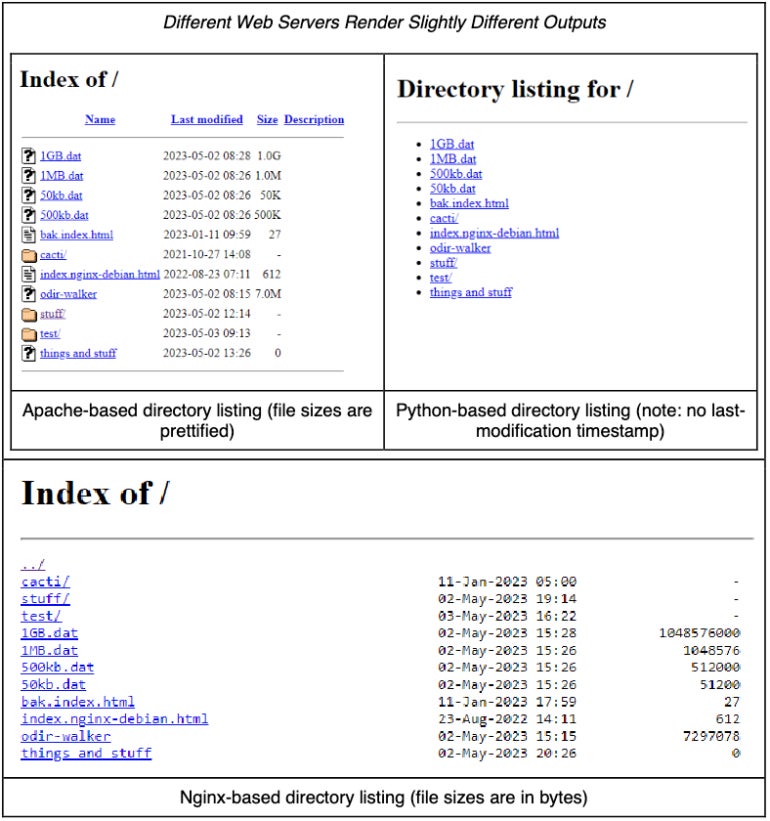
Open directories will be discovered through Google Dorks, that are queries that can be utilized on the Google search engine to seek out particular content material, resembling open directories. An analogous search will also be completed through Censys.
Why don’t search engines like google and yahoo prohibit individuals from seeing these open directories? Censys researchers informed TechRepublic that “whereas this may increasingly initially sound like an affordable strategy, it’s a bandage on the underlying difficulty of open directories being uncovered on the web within the first place. Simply because a search engine doesn’t show the outcomes doesn’t imply nefarious actors wouldn’t have the ability to discover them, but it surely might make it tougher for defenders to simply discover and remediate these situations. This additionally assumes that each one open directories are ‘unhealthy.’ Whereas lots of them are probably unintentionally uncovered, it doesn’t imply all of them are.”
Open directories statistics from the Censys analysis
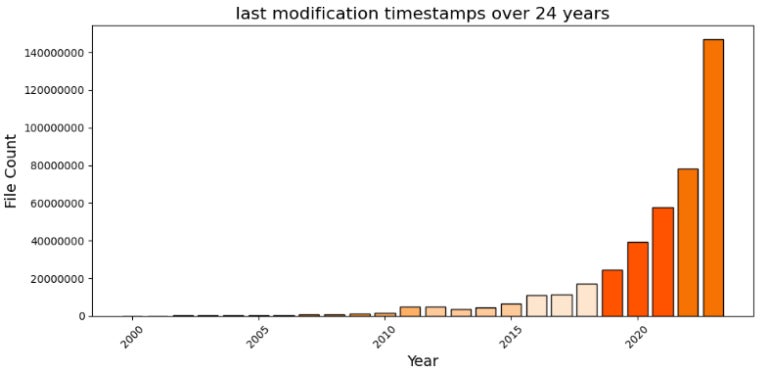
Censys discovered 313,750 totally different hosts with a complete of 477,330,039 recordsdata saved in these open directories. Analyzing the final modification timestamp of these recordsdata, the overwhelming majority of recordsdata have been created or modified in 2023 (Determine B).
Determine B
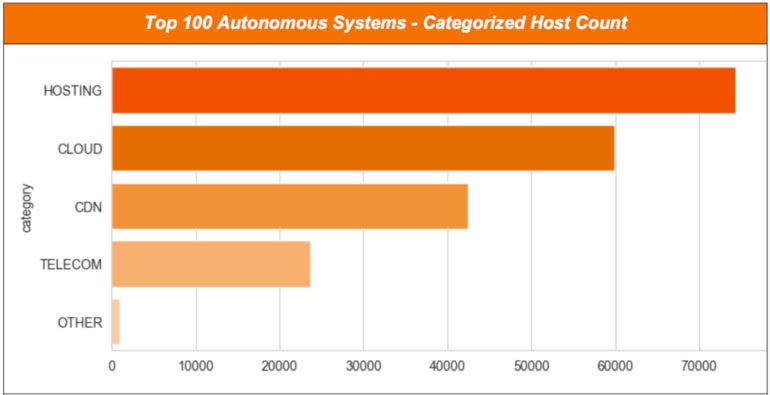
Relating to the internet hosting of these open directories on the Autonomous Programs degree, Censys has cut up the highest 100 AS into 4 classes to get a greater thought of what internet hosting companies are essentially the most used : internet hosting, cloud, content material supply networks and telecom.
Internet hosting: Most information is hosted by firms that present primary managed and unmanaged internet hosting companies, resembling digital internet hosting, shared internet hosting, digital non-public servers and devoted servers, for people and small to medium-sized organizations.
Cloud suppliers observe with the distinction being that they provide some ways to retailer and entry information in comparison with standard internet hosting.
CDNs resembling Akamai or Cloudflare are third (Determine C), earlier than telecoms, which embed extra people than organizations as in comparison with the opposite classes.
Determine C
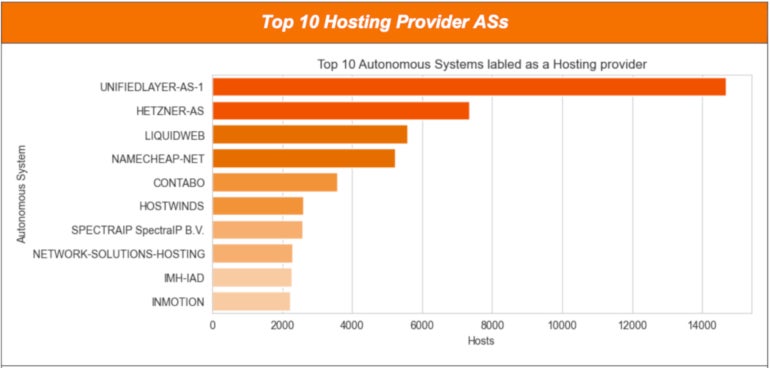
For the internet hosting class, the largest variety of uncovered open directories is situated at UnifiedLayer-AS-1, with greater than 14,000 distinctive hosts containing open directories. Second is Hetzner-AS, with greater than 7,000 hosts, adopted by Liquid Internet, with roughly 5,500 hosts (Determine D).
Determine D
What information pose safety dangers in open directories?
Censys categorized the recordsdata saved in these open directories primarily based on the file extensions (Determine E).
Determine E
Log recordsdata are significantly fascinating for an attacker as a result of these recordsdata would possibly include delicate info concerning the internet hosting infrastructure and the best way it’s accessed. Utility debug logs particularly might present a number of helpful info on the surroundings, whereas entry logs might include IP addresses. An attacker might exploit all this info to run focused assaults by discovering exploitable vulnerabilities or discovering insights between purposes and customers connecting to them.
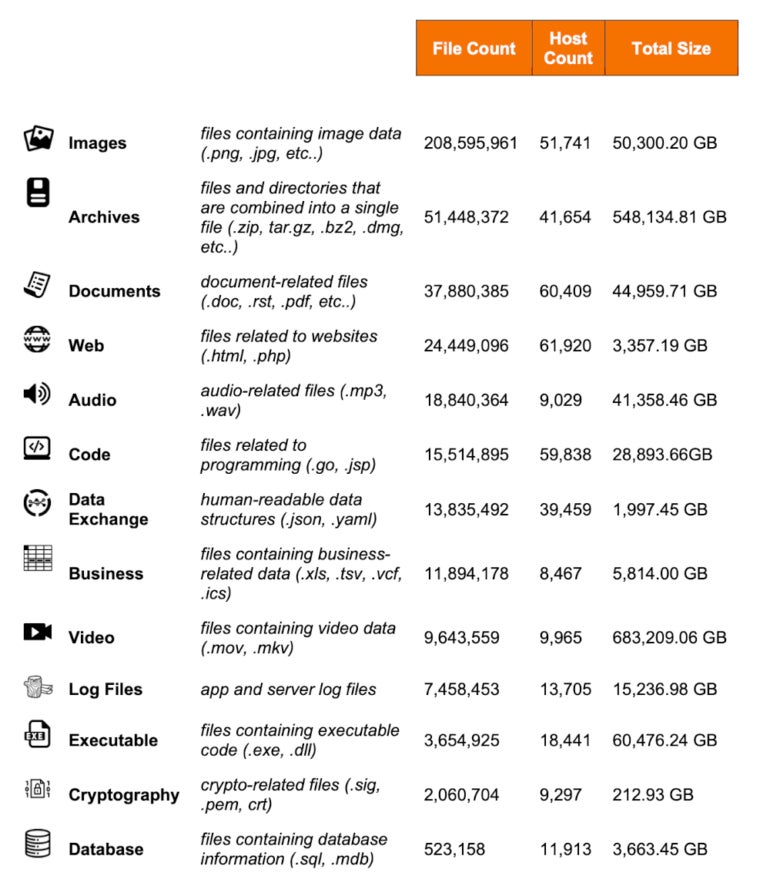
Databases are additionally very delicate as a result of they could include Private Figuring out Data, commerce secrets and techniques, mental property and technical details about the group or its infrastructure. A complete of 1,154 database recordsdata inside the measurement vary of 100-150 MB have been found within the open directories; 605 database recordsdata have been between 300 and 350 MB (Determine F).
Determine F
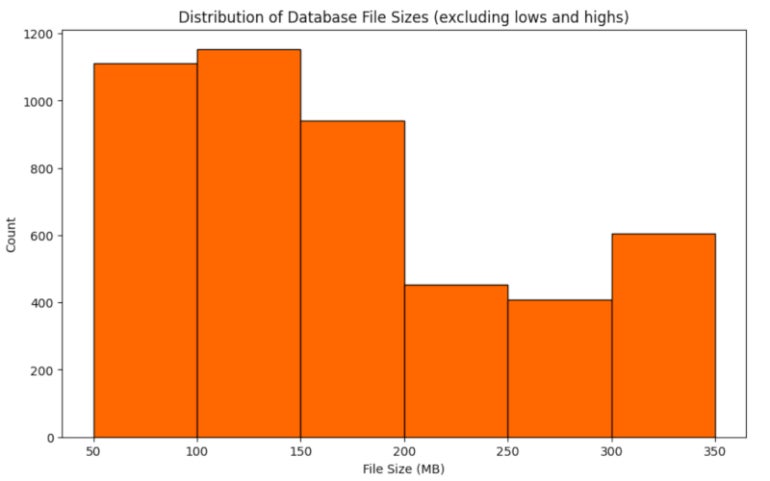
Censys didn’t view the content material of these database recordsdata, however the researchers did take a look at the frequency of phrases inside the file paths and file names (Determine G).
Determine G

The 713 occurrences of the phrase backup point out recordsdata which are a part of a database backup, whereas 334 occurrences of the phrase dump point out full copies of databases. Different phrases utilized in database file paths and names additionally point out doubtlessly delicate info being shared (Determine H).
Determine H

Censys discovered that 43,533 database recordsdata contained a development-related phrase (dev, take a look at, staging), and 25,427 database recordsdata contained a production-related phrase (prod, stay,p rd); this can be a potential goldmine of database-related info that attackers might use to use vulnerabilities, weaknesses or compromise delicate info.
Different phrases would possibly point out much less extreme points, resembling “schema” which could point out a database schema slightly than full content material,”aarch64/ppc641e/EPEL” which is likely to be databases distributed with open-source software program and “references” which might be take a look at information.
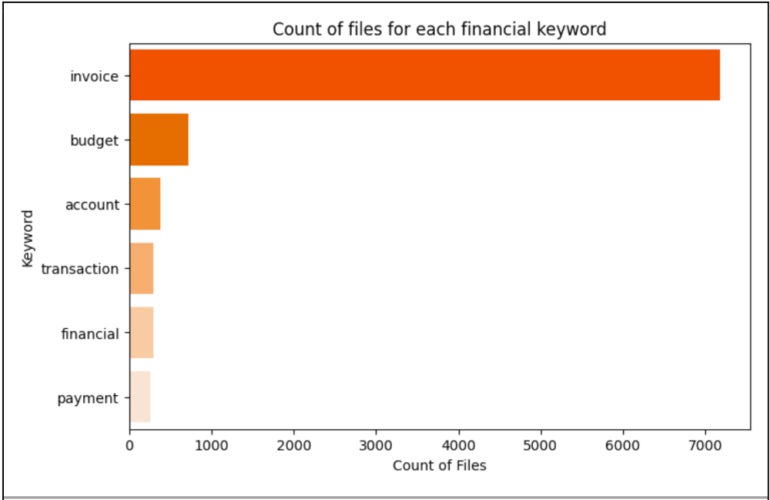
Other than database recordsdata, spreadsheets may additionally reveal delicate info. Over 370 GB of spreadsheet recordsdata are uncovered, a few of which have delicate phrases of their filename resembling bill, funds, account, transaction, monetary or cost (Determine I).
Determine I
Doubtlessly uncovered credentials will also be present in open directories in quite a lot of recordsdata (Determine J).
Determine J
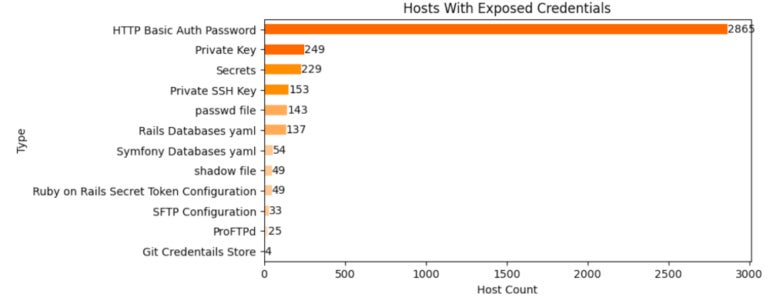
HTTP Fundamental Auth Password, generally known as .htpasswd, are text-based configuration recordsdata which may include credentials. Though the passwords in these recordsdata usually are not saved in plain textual content, they nonetheless is likely to be cracked by means of brute-force methods. Different recordsdata containing passwords or authentication strategies embody SSH non-public keys, purposes credentials and Unix password recordsdata.
Different file varieties may additionally characterize threats to the organizations exposing them. As an example, archives and emails would possibly leak inner, delicate or confidential info; delicate code or configuration recordsdata may additionally leak that info and may very well be exploited by attackers to seek out extra vulnerabilities.
Why are there so many open directories obtainable on the web?
As most main internet servers don’t allow listing itemizing by default when making an attempt to browse a folder that doesn’t include an index file, a number of hypotheses would possibly clarify why so many open directories can be found on-line.
- Some servers may need been rapidly configured, with system directors enabling listing itemizing for fast entry to recordsdata on previous servers. These directors have been then allowed to obtain their previous information however uncared for the server cleanup after the operation.
- Python’s built-in HTTP server exposes the present listing when launched within the command line. So long as the method isn’t stopped, it should preserve sharing that folder in public.
- Loads of these open directories look much like these of internet hosting resellers who solely implement minimal safety for his or her clients’ information; particularly, many use cPanel or Plesk as administration interfaces, and something exterior of these interfaces is uncared for.
We requested Censys researchers whether it is potential cybercriminals would create such open directories to contaminate guests with malware, they answered, “It’s potential, however there are far simpler malware supply mechanisms than hoping somebody will browse to an open listing and obtain a file. In circumstances the place malware is hosted in open directories, it’s extra probably that the recordsdata are remotely downloaded to a different host by a risk actor as soon as they achieve entry to stated different host.”
Safety finest practices and concerns for open directories
Organizations ought to continuously monitor their infrastructure for any open listing. Sharing recordsdata through open directories is a nasty IT apply that ought to cease. File transfers ought to all the time be completed through different strategies or protocols, resembling SFTP or through safe inner or exterior storage. When potential, multifactor authentication must be deployed to guard these folders.
Some open directories are made obtainable on function, whereas others outcome from errors. Organizations usually are not the one entities to show information this fashion — people additionally do and may not know how one can safe an online server. It’s tough to report open directories to these people as a result of they usually neglect to supply a option to report safety points on their web site, which has usually been created utilizing generic companies that don’t take safety into critical consideration. As compared, massive organizations usually have a correct safety.txt file at their root folder or a safety contact simply reachable on websites like LinkedIn, for instance.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.
[ad_2]