
[ad_1]

Cloudflare’s Firewall and DDoS prevention could be bypassed via a particular assault course of that leverages logic flaws in cross-tenant safety controls.
This bypass might put Cloudflare’s clients below a heavy burden, rendering the safety programs of the web agency much less efficient.
To make issues worse, the one requirement for the assault is for the hackers to create a free Cloudflare account, which is used as a part of the assault.
Nonetheless, it must be famous that the attackers should know a focused net server’s IP deal with to abuse these flaws.
Cloudflare vs Cloudflare
Certitude’s researcher Stefan Proksch found that the supply of the difficulty is Cloudflare’s technique to make use of shared infrastructure that accepts connections from all tenants.
Particularly, the analyst recognized two vulnerabilities within the system impacting Cloudflare’s “Authenticated Origin Pulls” and “Allowlist Cloudflare IP Addresses.”
Authenticated Origin Pulls is a safety characteristic supplied by Cloudflare to make sure that HTTP(s) requests despatched to an origin server come via Cloudflare and never from an attacker.
When configuring this characteristic, clients can add their certificates utilizing an API or generate one via Cloudflare, the default and easiest way.
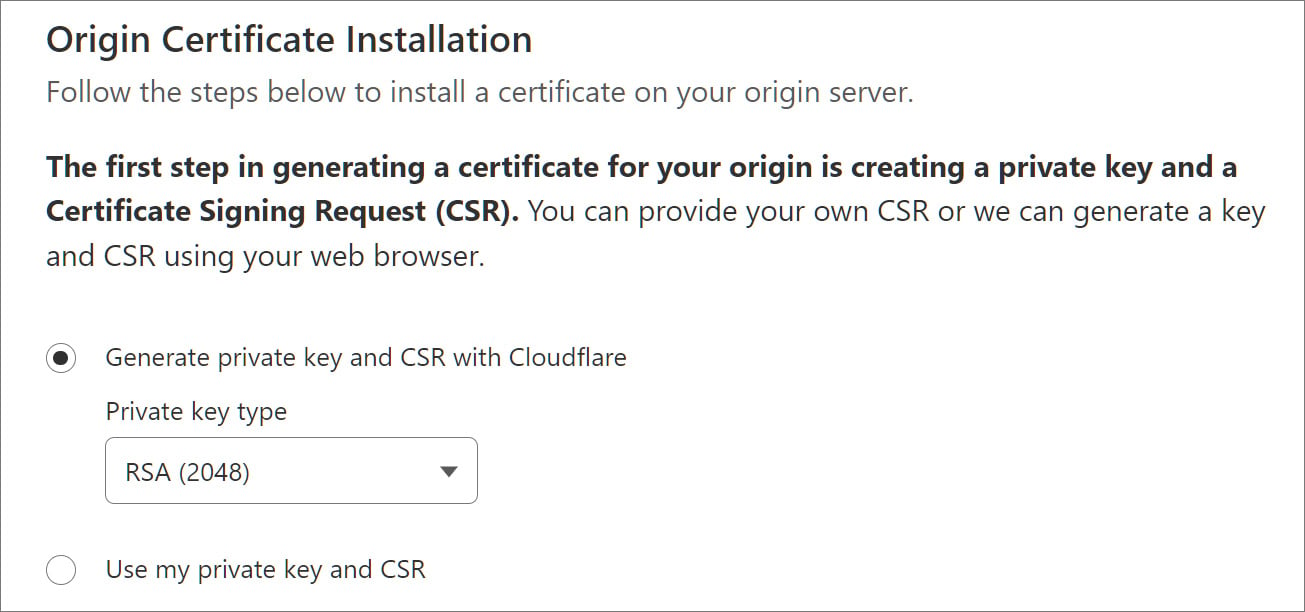
Supply: BleepingComputer
As soon as configured, Cloudflare makes use of the SSL/TLS certificates to authenticate any HTTP(S) requests between the service’s reverse proxies and the client’s origin server, stopping unauthorized requests from accessing the web site.
Nonetheless, as Proksch explains, attackers can bypass this safety as Cloudflare makes use of a shared certificates for all clients as an alternative of a tenant-specific one, inflicting all connections originating from Cloudflare to be permitted.
“An attacker can setup a customized area with Cloudflare and level the DNS A report to victims IP deal with,” explains Proksch.
“The attacker then disables all safety options for that customized area of their tenant and tunnel their assault(s) via the Cloudflare infrastructure.”
“This method permits attackers to bypass the safety options by the sufferer.”
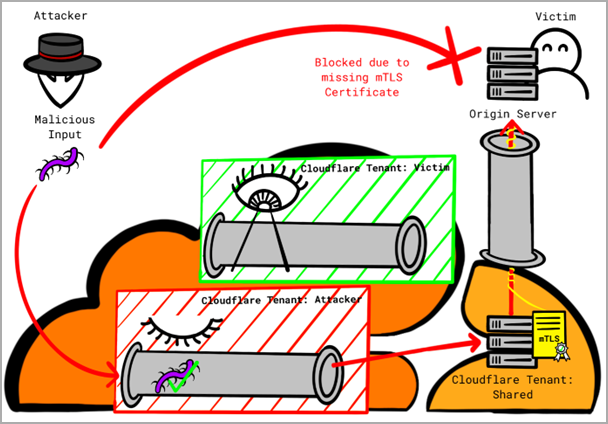
The issue arising from this logic hole is that attackers with a Cloudflare account can direct malicious site visitors to different Cloudflare purchasers or route their assaults via the corporate’s infrastructure.
Proksch says the one method to mitigate this weak point is to make use of customized certificates reasonably than one generated by Cloudflare.
The second challenge impacts Cloudflare’s Allowlist Cloudflare IP addresses, a safety measure that solely permits site visitors originating from Cloudflare’s IP deal with vary to achieve purchasers’ origin servers.
Once more, an attacker can leverage a flaw within the logic by organising a site with Cloudflare and pointing their area’s DNS A report to the IP deal with of the goal sufferer’s server.
Subsequent, they flip off all safety options for the customized area and route the malicious site visitors via Cloudflare’s infrastructure, which will likely be seen as trusted from the sufferer’s perspective and, therefore, permitted.
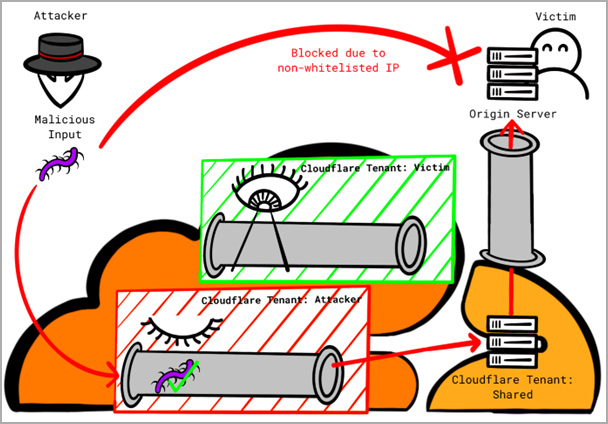
Proksch has additionally shared a proof-of-concept with configuration particulars to show how simple it’s to bypass Cloudflare protections by leveraging the issues.
Certitude proposes the next protection measures towards these assaults:
- Use a customized certificates to configure the “Authenticated Origin Pulls” mechanism as an alternative of Cloudflare’s shared certificates.
- Use Cloudflare Aegis (if obtainable) to outline a extra particular egress IP deal with vary devoted to every shopper.
Researchers Florian Schweitzer and Stefan Proksch, who found the logic flaws, reported it to Cloudflare by way of HackerOne on March 16, 2023, however the challenge was closed as “informative.”
BleepingComputer has contacted Cloudflare to ask if there are any plans to implement extra safety mechanisms or warn purchasers with probably dangerous configurations, however we now have but to listen to again.
[ad_2]