[ad_1]

Over the weekend, safety researchers launched a proof-of-concept (PoC) exploit for a most severity distant code execution vulnerability in Progress Software program’s WS_FTP Server file sharing platform.
Assetnote researchers who found and reported the utmost severity flaw (CVE-2023-40044) printed a weblog publish with a PoC exploit and extra technical particulars on Saturday.
CVE-2023-40044 is brought on by a .NET deserialization vulnerability within the Advert Hoc Switch Module, permitting unauthenticated attackers to remotely execute instructions on the underlying working system by way of a easy HTTP request.
“This vulnerability turned out to be comparatively straight ahead and represented a typical .NET deserialization situation that led to RCE. It is stunning that this bug has stayed alive for therefore lengthy, with the seller stating that the majority variations of WS_FTP are susceptible,” Assetnote mentioned.
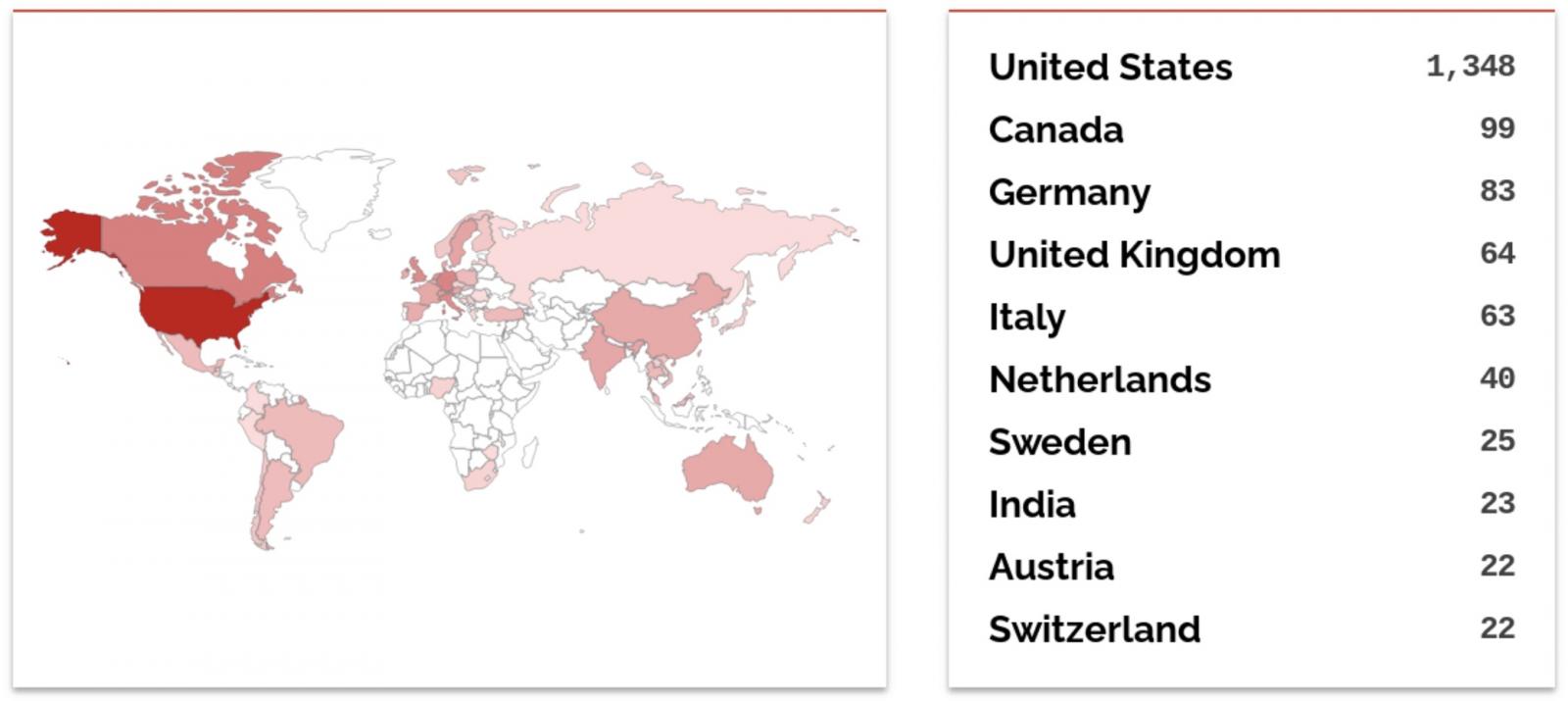
“From our evaluation of WS_FTP, we discovered that there are about 2.9k hosts on the web which might be operating WS_FTP (and still have their webserver uncovered, which is important for exploitation). Most of those on-line property belong to giant enterprises, governments and academic establishments.”
A Shodan search confirms Assetnote’s estimates, exhibiting that greater than 2,000 gadgets operating WS_FTP Server are at present reachable over the Web.
Exploited within the wild
The day the PoC exploit was launched, cybersecurity firm Rapid7 additionally revealed that attackers started exploiting CVE-2023-40044 on Saturday night, September 30.
“As of September 30, Rapid7 has noticed a number of situations of WS_FTP exploitation within the wild,” mentioned Caitlin Condon, Head of Vulnerability Analysis at Rapid7.
“The method execution chain seems the identical throughout all noticed situations, indicating potential mass exploitation of susceptible WS_FTP servers.
“Additionaly, our MDR group has noticed the identical Burpsuite area used throughout all incidents, which can level to a single risk actor behind the exercise we have seen.”
Progress Software program launched safety updates to deal with the important CVE-2023-40044 vulnerability on Wednesday, September 27.
“We now have addressed the vulnerabilities above and the Progress WS_FTP group strongly recommends performing an improve,” Progress warned on the time.
“We do advocate upgrading to probably the most highest model which is 8.8.2. Upgrading to a patched launch, utilizing the total installer, is the one strategy to remediate this situation.
Organizations that can’t instantly patch their servers can nonetheless thwart incoming assaults by disabling the susceptible WS_FTP Server Advert Hoc Switch Module.
On Friday, the Well being Sector Cybersecurity Coordination Heart (HC3), the U.S. Well being Division’s safety group, additionally warned all Healthcare and Public Well being sector organizations to patch their servers as quickly as potential.
Progress Software program remains to be coping with the fallout of an intensive collection of knowledge theft assaults that exploited a zero-day within the MOVEit Switch safe file switch platform and affected greater than 2,100 organizations and over 62 million people, in response to Emsisoft estimates.
Replace October 02, 13:33 EDT: A Progress spokesperson shared the next assertion after the article was printed:
We’re upset in how rapidly third events launched a proof of idea (POC), reverse-engineered from our vulnerability disclosure and patch, launched on Sept. 27. This supplied risk actors a roadmap on tips on how to exploit the vulnerabilities whereas a lot of our clients have been nonetheless within the strategy of making use of the patch.
We’re not conscious of any proof that these vulnerabilities have been being exploited previous to that launch. Sadly, by constructing and releasing a POC quickly after our patch was launched, a third-party has given cyber criminals a device to try assaults in opposition to our clients. We’re encouraging all WS_FTP server clients to patch their environments as rapidly as potential.
The safety of our clients is our high precedence and we proceed to work with our clients and accountable third-party analysis specialists to find, correctly disclose and remediate any points. We hope that the group will discourage the irresponsible publication of POCs quickly following the discharge of safety patches from software program distributors.
[ad_2]