
[ad_1]
VMware Cloud Director (VCD) was designed from the bottom up with multi-tenancy in thoughts. It’s a product that permits a number of prospects or tenants to make use of the VMware Software program-Outlined Information Heart (SDDC) infrastructure whereas sustaining strict isolation, safety, and useful resource allocation.
VMware NSX has offered a multi-tenant data-plane mannequin because the starting of the product. Nonetheless, it began to help administration airplane multi-tenancy with the introduction of NSX Tasks in model 4.0.1.1 (API) and in 4.1 within the UI.
Naturally, to enhance the combination with NSX and unlock quite a few networking options, VCD improvement advanced in order that the most recent 10.5.1 launch now adopts the NSX Mutli-Tenancy mannequin. Learn extra about NSX Multi-Tenancy journey.
Ideas
Within the VCD platform, tenancy is carried out via the usage of the Organizations. Every tenant is assigned a devoted group, offering a logically segregated digital infrastructure and assets for his or her workloads. The Group assemble permits for fine-grained management over the tenant’s entry to assets and allows the tenant to handle their very own Customers, Digital Information Facilities (VDCs), Catalogs, Insurance policies, and extra.
To explicitly outline the tenant paradigm, VMware NSX carried out an answer known as Tasks. These Tasks delegate NSX customers to totally different areas with their very own objects, configurations, and monitoring (based mostly on alarms and logs).
VCD 10.5.1 gives administration capabilities related to NSX Tenancy, that are completely within the Supplier’s scope. The NSX Tenancy characteristic is out there per Group foundation, and when enabled, a VCD Group maps on to an NSX Mission.

After the NSX Tenancy is enabled on the Organizational degree, Suppliers can create Group Digital Information Facilities (VDCs) with Networking Tenancy enabled by way of the Org. VDC creation wizard.
Any present VDCs and Information Heart (DC) Teams owned by that Group are thought of brownfield and have the Networking Tenancy “Inactive”.
It’s vital to notice that VCD can’t acknowledge and import present NSX Tasks. As a way to use Networking Tenancy throughout the context of VCD, suppliers should first outline the Group inside VCD after which to allow the Networking Tenancy.
VCD Networking Tenancy Particulars
When a Supplier allows the NSX Tenancy (Networking Tenancy) for a selected Group, he can even outline a Log Identify. That is the Group’s distinctive identifier within the backing NSX Supervisor logs.

Activating the Networking Tenancy for the Group doesn’t set off fast NSX Mission creation. As an alternative, the NSX Mission will get created when the primary Networking Tenancy enabled VDC is created. The NSX Mission identify corresponds to the Group identify, although.

By default, the Networking Tenancy for a VDC that’s created in an NSX Tenancy enabled Group is “ON”. When the Networking Tenancy is enabled for a selected VDC, the Community Pool choice is disabled. That’s as a result of NSX helps Mission creation solely within the default overlay Transport Zone.

The Community Pool with the default overlay Transport Zone for the backing community supplier has to exit beforehand. In any other case, VCD will throw an error when creating Networking Tenancy enabled VDC.
Not all VDCs in a Mission-aware group have to take part within the Mission. Suppose a distinct Geneve-backed Community Pool (non-default Transport Zone) or solely VLAN networks are required in a VDC. In that case, the Supplier can disable the Networking Tenancy and choose the respective Community Pool.
Nonetheless, it’s important to notice that the Networking Tenancy (NSX Mission participation) can solely be specified throughout VDC creation. It can’t be modified afterward. Likewise, as soon as a Supplier allows the Networking Tenancy on VDC creation, they can’t swap Community Swimming pools.
VCD Mannequin to NSX Tasks
VCD makes the NSX Mission administration features, similar to creation, Tier-0 Gateway, and NSX Edge Cluster assignments, completely clear for each the Supplier and the Tenant. When an Edge Gateway is created in a Networking Tenancy enabled VDC, VMware Cloud Director takes care of the respective NSX Edge Cluster and Tier-0 Gateway to be shared with the Mission.
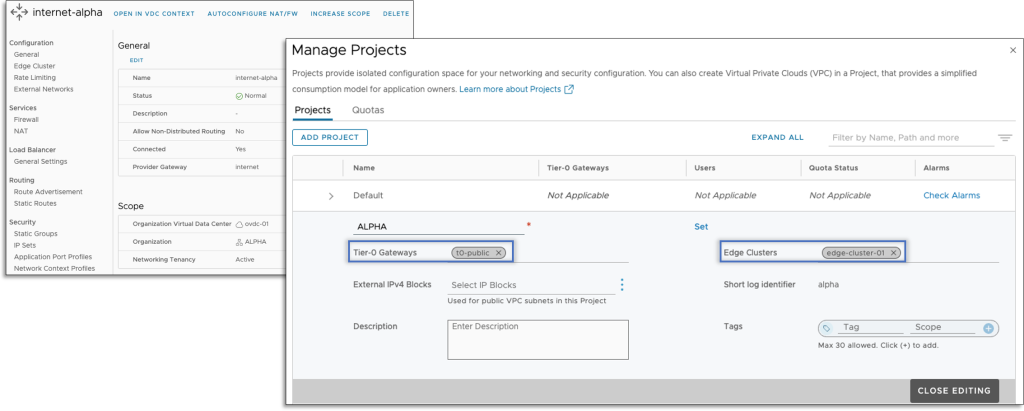
NSX segments related to exterior and imported networks don’t should be a part of the Mission. If mandatory, VCD takes care of those exterior elements to be related to Mission elements by way of an NSX Useful resource Share. When the connection is eliminated, the share is up to date accordingly.
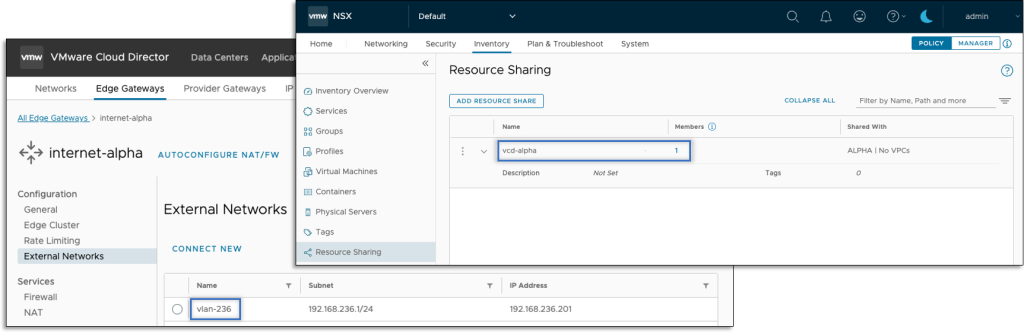
Information Heart Teams help
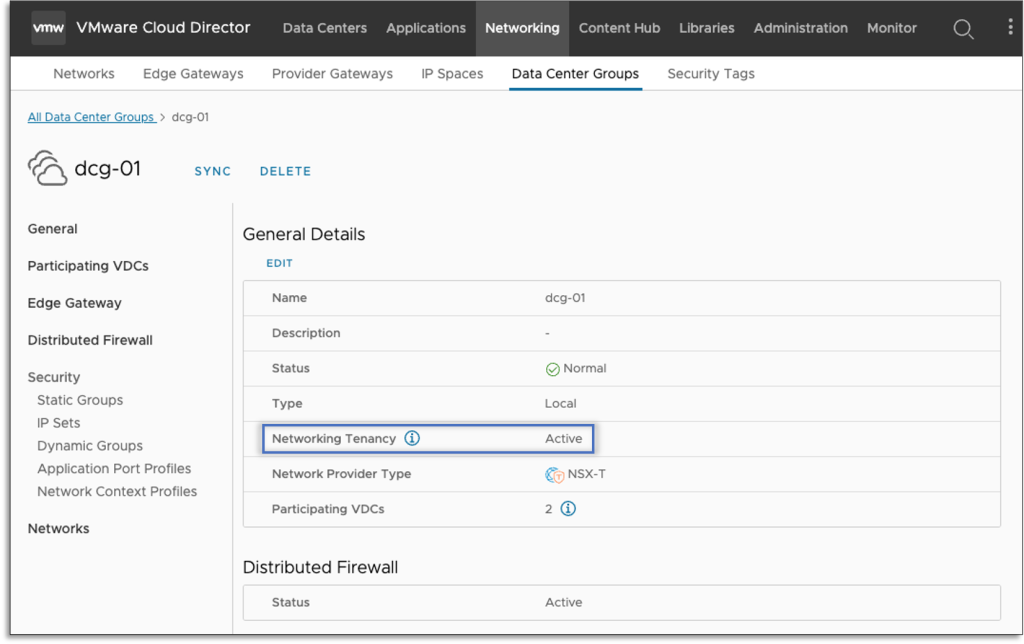
The NSX Mission is completely owned by the Group that created it. The DC Group beginning VDC sort (Networking Tenancy enabled or not) determines whether or not the DC Group could have the Networking Tenancy energetic. It’s not necessary for all VDC members of the DC Group to have an energetic Networking Tenancy. VMware Cloud Director helps a combined mode the place a DC Group has each Networking Tenancy energetic VDCs and Networking Tenancy inactive VDCs.
The NSX Mission related to the beginning VDC is the one which can be used for all DC Group networking and safety objects. Edge Gateways, Networks, Distributed Firewall Guidelines, Safety Teams, and many others., will sit throughout the scope of that NSX Mission.
Unsupported options
At present, NSX Tasks just isn’t a supported characteristic for NSX Federation deployments. Additionally, not all Edge Gateway options can be found for Networking Tenancy enabled VDCs or DC Teams. VPNs (IPsec/L2) and sharing phase profile templates are the primary notables.
To lear extra in regards to the NSX Tasks supportability matrix: Options Accessible for Consumption Beneath NSX Tasks
In Conclusion
By matching the NSX Tasks with VCD’s Tenancy, prospects will profit from a variety of networking capabilities the NSX Multi-tenancy answer gives. Considered one of these crucial options is tenant-focused logging for core VCD networking companies similar to Edge Companies and Distributed firewalls.
At present, the primary platform for offering log entry inside VCD is VMware Aria Operations (a.okay.a. LogInsight). Aria Operations is a part of the bottom VMware Cloud Supplier Platform (VCPP) bundle and, due to this fact, is out there for all suppliers at no cost as a part of the VCPP program.
NSX Tasks logs from the Distributed and Gateway firewalls are labeled with the NSX Mission log identifier, offering simple identification and separation per Tenant.
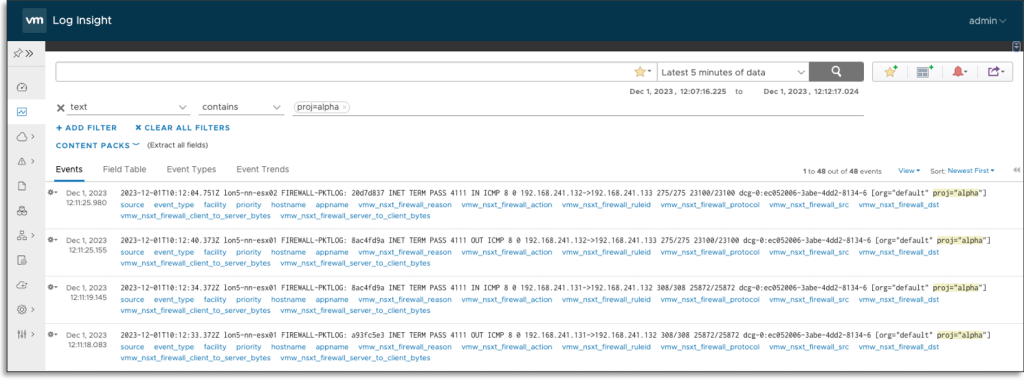
The combination with NSX Tasks may also enable exploring the potential for characteristic enhancements to supply tenant self-service login capabilities in VCD.
Beneath, you’ll find extra details about VMware Cloud Director 10.5.1’s new options and capabilities.
Stay up-to-date by usually checking this weblog for the most recent updates. You may as well join with us on Slack, Fb, Twitter, and LinkedIn.
Keep tuned for brand spanking new demo movies and enablement on YouTube, particularly our Characteristic Fridays sequence.
[ad_2]