
[ad_1]
IoT is creating new alternatives and offering a aggressive benefit for companies in present and new markets. It touches everythingnot simply the information, however how, when, the place and why you gather it. The applied sciences which have created the Web of Issues arent altering the web solely, however slightly change the issues related to the internetthe gadgets and gateways on the sting of the community that are actually capable of request a service or begin an motion with out human intervention at many ranges.
As a result of the technology and evaluation of information is so important to the IoT, consideration should be given to defending information all through its life cycle. Managing info in any respect ranges is advanced as a result of information will circulation throughout many administrative boundaries with completely different insurance policies and intents.
Given the assorted technological and bodily parts that actually make up an IoT ecosystem, it’s good to contemplate the IoT as a system-of-systems. The architecting of those methods that present enterprise worth to organizations will typically be a posh enterprise, as enterprise architects work to design built-in options that embrace edge gadgets, functions, transports, protocols, and analytics capabilities that make up a completely functioning IoT system. This complexity introduces challenges to protecting the IoT safe, and guaranteeing {that a} explicit occasion of the IoT can’t be used as a leaping off level to assault different enterprise info expertise (IT) methods.
Worldwide Information Company (IDC) estimates that 90% of organizations that implement the IoT will endure an IoT-based breach of back-end IT methods by the yr 2017.
Challenges to Safe IoT Deployments
Whatever the function your enterprise has throughout the Web of Issues ecosystem gadget producer, answer supplier, cloud supplier, methods integrator, or service provideryou have to know tips on how to get the best profit from this new expertise that gives such extremely numerous and quickly altering alternatives.
Dealing with the big quantity of current and projected information is daunting. Managing the inevitable complexities of connecting to a seemingly limitless listing of gadgets is sophisticated. And the aim of turning the deluge of information into worthwhile actions appears unimaginable due to the various challenges. The prevailing safety applied sciences will play a job in mitigating IoT dangers however they don’t seem to be sufficient. The aim is to get information securely to the best place, on the proper time, in the best format; its simpler stated than carried out for a lot of causes.
Coping with the Challenges and Threats
Gartnerpredicted that greater than 20% of companies will deploy safety options for safeguarding their IoT gadgets and providers by 2017, IoT gadgets and providers will increase the floor space for cyber-attacks on companies, by turning bodily objects that was once offline into on-line property speaking with enterprise networks. Companies should reply by broadening the scope of their safety technique to incorporate these new on-line gadgets.
Companies should tailor safety to every IoT deployment in keeping with the distinctive capabilities of the gadgets concerned and the dangers related to the networks related to these gadgets. BI Intelligence expects spending on options to safe IoT gadgets and methods to extend 5 fold over the following 4 years.
The Optimum Platform
Creating options for the Web of Issues requires unprecedented collaboration, coordination, and connectivity for every bit within the system, and all through the system as a complete. All gadgets should work collectively and be built-in with all different gadgets, and all gadgets should talk and work together seamlessly with related methods and infrastructures in a safe means. Its potential, however it may be costly, time consuming, and troublesome, until new line of pondering and new strategy to IoT safety emerged away from the present centralized mannequin.
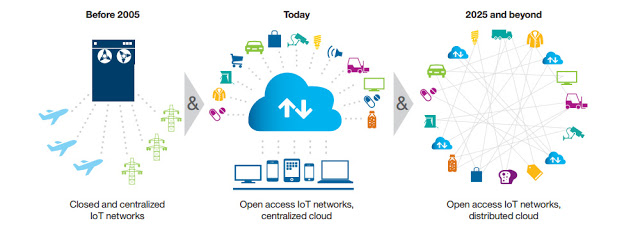
The Downside with the Present Centralized Mannequin
The present IoT ecosystems depend on centralized, brokered communication fashions, in any other case often called the server/shopper paradigm. All gadgets are recognized, authenticated and related by means of cloud servers that sport large processing and storage capacities. Connection between gadgets should completely undergo the web, even when they occur to be a couple of toes aside.
Whereas this mannequin has related generic computing gadgets for many years, and can proceed to help small-scale IoT networks as we see them right now, it won’t be able to reply to the rising wants of the large IoT ecosystems of tomorrow.
Current IoT options are costly due to the excessive infrastructure and upkeep price related to centralized clouds, massive server farms and networking tools. The sheer quantity of communications that should be dealt with when IoT gadgets develop to the tens of billions will improve these prices considerably.
Even when the unprecedented economical and engineering challenges are overcome, cloud servers will stay a bottleneck and level of failure that may disrupt your entire community. That is particularly essential as extra essential duties
Furthermore, the range of possession between gadgets and their supporting cloud infrastructure makes machine-to-machine (M2M) communications troublesome. Theres no single platform that connects all gadgets and no assure that cloud providers supplied by completely different producers are interoperable and suitable.
Decentralizing IoT Networks
A decentralized strategy to IoT networking would remedy most of the questions above. Adopting a standardized peer-to-peer communication mannequin to course of the lots of of billions of transactions between gadgets will considerably scale back the prices related to putting in and sustaining massive centralized information facilities and can distribute computation and storage wants throughout the billions of gadgets that kind IoT networks. This can stop failure in any single node in a community from bringing your entire community to a halting collapse.
Nevertheless, establishing peer-to-peer communications will current its personal set of challenges, chief amongst them the difficulty of safety. And as everyone knows, IoT safety is way more than simply about defending delicate information. The proposed answer should preserve privateness and safety in large IoT networks and provide some type of validation and consensus for transactions to forestall spoofing and theft.
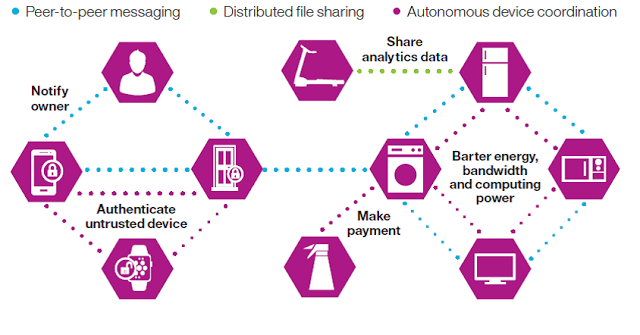
To carry out the features of conventional IoT options with out a centralized management, any decentralized strategy should help three basic features:
- Peer-to-peer messaging
- Distributed file sharing
- Autonomous gadget coordination
The Blockchain Strategy
Blockchain, the distributed ledger expertise that underpins bitcoin, has emerged as an object of intense curiosity within the tech business and past. Blockchain expertise presents a means of recording transactions or any digital interplay in a means that’s designed to be safe, clear, extremely immune to outages, auditable, and environment friendly; as such, it carries the potential of disrupting industries and enabling new enterprise fashions. The expertise is younger and altering very quickly; widespread commercialization remains to be a couple of years off. Nonetheless, to keep away from disruptive surprises or missed alternatives, strategists, planners, and determination makers throughout industries and enterprise features ought to pay heed now and start to research functions of the expertise.
What’s Blockchain?
Blockchain is a database that maintains a constantly rising set of information data. It’s distributed in nature, which means that there isn’t a grasp laptop holding your entire chain. Moderately, the collaborating nodes have a replica of the chain. Its additionally ever-growing information data are solely added to the chain.
A blockchain consists of two forms of parts:
- Transactions are the actions created by the members within the system.
- Blocks report these transactions and ensure they’re within the right sequence and haven’t been tampered with. Blocks additionally report a time stamp when the transactions have been added.
What are Some Benefits of Blockchain?
The massive benefit of blockchain is that its public. Everybody collaborating can see the blocks and the transactions saved in them. This doesnt imply everybody can see the precise content material of your transaction, nevertheless; thats protected by your non-public key.
A blockchain is decentralized, so there isn’t a single authority that may approve the transactions or set particular guidelines to have transactions accepted. Meaning theres an enormous quantity of belief concerned since all of the members within the community have to succeed in a consensus to just accept transactions.
Most significantly, its safe. The database can solely be prolonged and former data can’t be modified (no less than, theres a really excessive price if somebody needs to change earlier data).
How Does it Work?
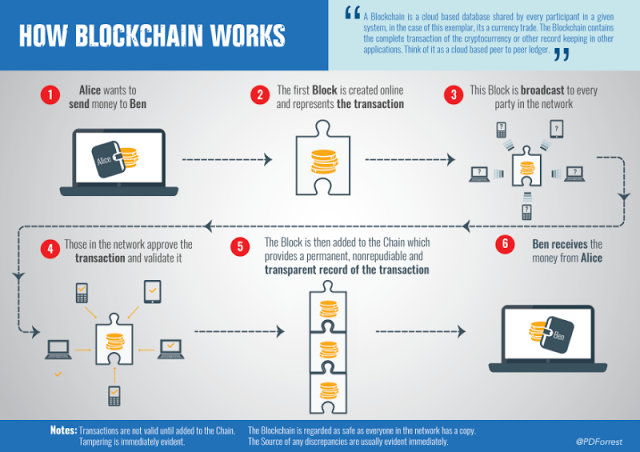
When somebody needs so as to add a transaction to the chain, all of the members within the community will validate it. They do that by making use of an algorithm to the transaction to confirm its validity. What precisely is known by legitimate is outlined by the blockchain system and may differ between methods. Then it’s as much as a majority of the members to agree that the transaction is legitimate.
A set of authorised transactions are then bundled in a block, which will get despatched to all of the nodes within the community. They in flip validate the brand new block. Every successive block accommodates a hash, which is a singular fingerprint, of the earlier block.
Two Major Sorts of Blockchain
- In a public blockchain, everybody can learn or write information. Some public blockchains restrict the entry to simply studying or writing. Bitcoin, for instance, makes use of an strategy the place anybody can write.
- In a non-public blockchain, all of the members are recognized and trusted. That is helpful when the blockchain is used between corporations that belong to the identical authorized mom entity.
The Blockchain and IoT
Blockchain expertise is the lacking hyperlink to settle scalability, privateness, and reliability considerations within the Web of Issues. Blockchain applied sciences may maybe be the silver bullet wanted by the IoT business. Blockchain expertise can be utilized in monitoring billions of related gadgets, allow the processing of transactions and coordination between gadgets; enable for vital financial savings to IoT business producers. This decentralized strategy would remove single factors of failure, making a extra resilient ecosystem for gadgets to run on. The cryptographic algorithms utilized by blockchains, would make client information extra non-public.
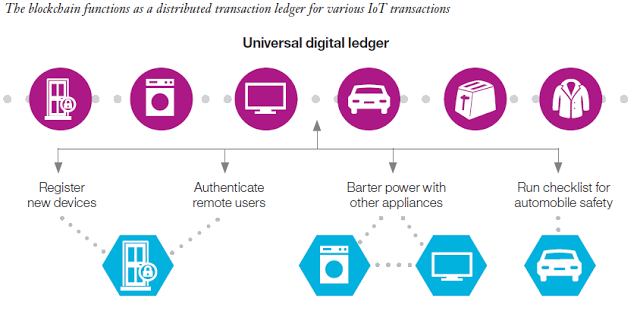
The ledger is tamper-proof and can’t be manipulated by malicious actors as a result of it doesnt exist in any single location, and man-in-the-middle assaults can’t be staged as a result of there isn’t a single thread of communication that may be intercepted. Blockchain makes trustless, peer-to-peer messaging potential and has already confirmed its value on this planet of monetary providers by means of cryptocurrencies akin to Bitcoin, offering assured peer-to-peer fee providers with out the necessity for third-party brokers.
The decentralized, autonomous, and trustless capabilities of the blockchain make it an excellent part to turn out to be a basic aspect of IoT options. It isn’t a shock that enterprise IoT applied sciences have rapidly turn out to be one of many early adopters of blockchain applied sciences.
In an IoT community, the blockchain can preserve an immutable report of the historical past of sensible gadgets. This characteristic permits the autonomous functioning of sensible gadgets with out the necessity for centralized authority. In consequence, the blockchain opens the door to a collection of IoT situations that have been remarkably troublesome, and even unimaginable to implement with out it.
By leveraging the blockchain, IoT options can allow safe, trustless messaging between gadgets in an IoT community. On this mannequin, the blockchain will deal with message exchanges between gadgets much like monetary transactions in a bitcoin community. To allow message exchanges, gadgets will leverage sensible contracts which then mannequin the settlement between the 2 events.
On this state of affairs, we are able to sensor from afar, speaking immediately with the irrigation system with the intention to management the circulation of water primarily based on circumstances detected on the crops. Equally, sensible gadgets in an oil platform can trade information to regulate functioning primarily based on climate circumstances.
Utilizing the blockchain will allow true autonomous sensible gadgets that may trade information, and even execute monetary transactions, with out the necessity of a centralized dealer. Any such autonomy is feasible as a result of the nodes within the blockchain community will confirm the validity of the transaction with out counting on a centralized authority.
On this state of affairs, we are able to envision sensible gadgets in a producing plant that may place orders for repairing a few of its components with out the necessity of human or centralized intervention. Equally, sensible autos in a truck fleet will have the ability to present a whole report of an important components needing substitute after arriving at a workshop.
Some of the thrilling capabilities of the blockchain is the flexibility to take care of a duly decentralized, trusted ledger of all transactions occurring in a community. This functionality is important to allow the various compliance and regulatory necessities of commercial IoTapplications with out the necessity to depend on a centralized mannequin.
The put up Easy methods to Safe the Web of Issues (IoT) with Blockchain appeared first on Datafloq.
[ad_2]