
[ad_1]

Juniper Networks has launched safety updates to repair a important pre-auth distant code execution (RCE) vulnerability in its SRX Sequence firewalls and EX Sequence switches.
Discovered within the gadgets’ J-Internet configuration interfaces and tracked as CVE-2024-21591, this important safety flaw can be exploited by unauthenticated menace actors to get root privileges or launch denial-of-service (DoS) assaults towards unpatched gadgets.
“This situation is brought on by use of an insecure perform permitting an attacker to overwrite arbitrary reminiscence,” the corporate defined in a safety advisory printed Wednesday.
Juniper added that its Safety Incident Response Workforce has no proof that the vulnerability is being exploited within the wild.
The whole listing of weak Junos OS variations affected by the SRX Sequence and EX Sequence J-Internet bug consists of:
- Junos OS variations sooner than 20.4R3-S9
- Junos OS 21.2 variations sooner than 21.2R3-S7
- Junos OS 21.3 variations sooner than 21.3R3-S5
- Junos OS 21.4 variations sooner than 21.4R3-S5
- Junos OS 22.1 variations sooner than 22.1R3-S4
- Junos OS 22.2 variations sooner than 22.2R3-S3
- Junos OS 22.3 variations sooner than 22.3R3-S2
- Junos OS 22.4 variations sooner than 22.4R2-S2, 22.4R3
The bug has been addressed in Junos OS 20.4R3-S9, 21.2R3-S7, 21.3R3-S5, 21.4R3-S5, 22.1R3-S4, 22.2R3-S3, 22.3R3-S2, 22.4R2-S2, 22.4R3, 23.2R1-S1, 23.2R2, 23.4R1, and all subsequent releases.
Admins are suggested to right away apply the safety updates or improve JunOS to the most recent launch or, not less than, disable the J-Internet interface to take away the assault vector.
One other non permanent workaround is to limit J-Internet entry to solely trusted community hosts till patches are deployed.
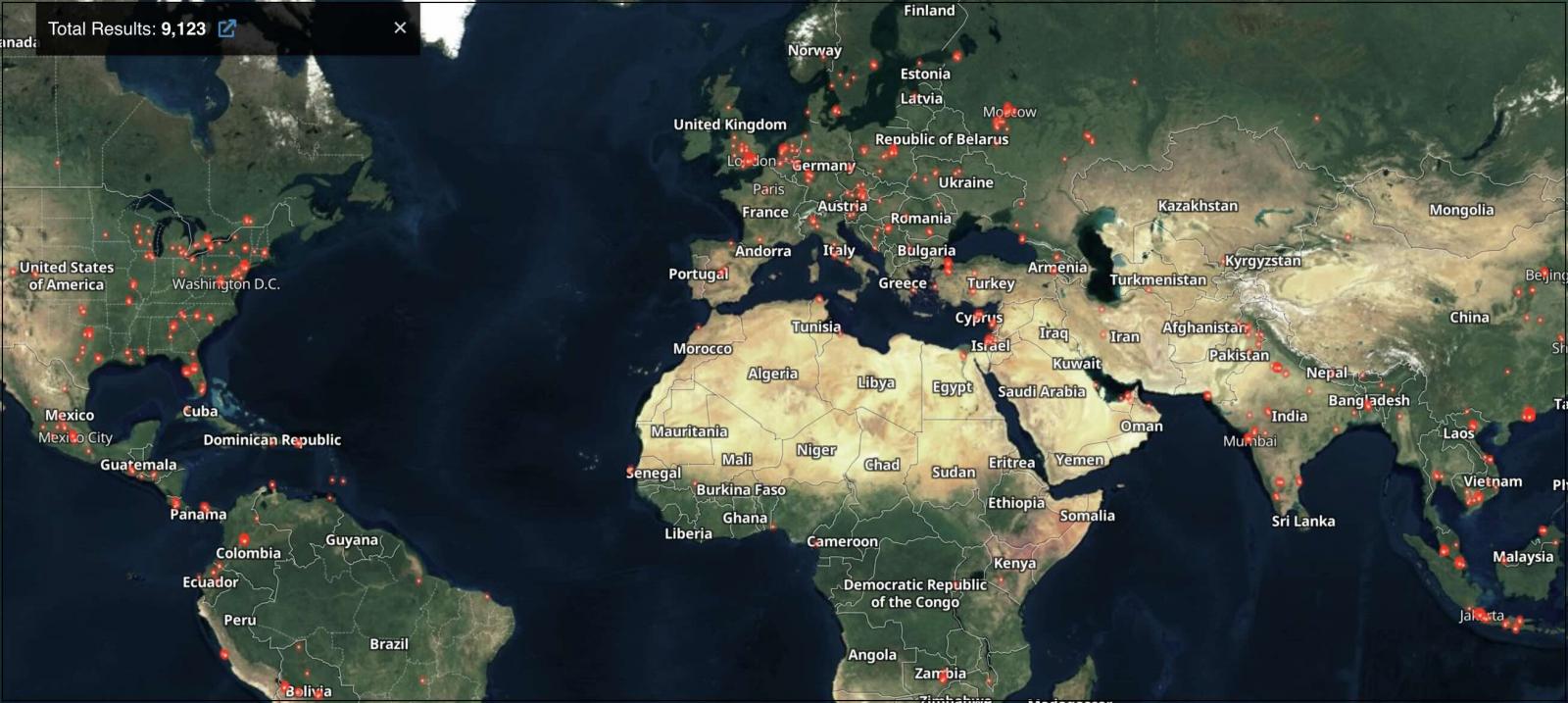
Based on knowledge from nonprofit web safety group Shadowserver, greater than 8,200 Juniper gadgets have their J-Internet interfaces uncovered on-line, most from South Korea (Shodan additionally tracks over 9,000).
CISA additionally warned in November of a Juniper pre-auth RCE exploit used within the wild, chaining 4 bugs tracked as CVE-2023-36844, CVE-2023-36845, CVE-2023-36846, and CVE-2023-36847 and impacted the corporate’s SRX firewalls and EX switches.
The alert got here months after ShadowServer detected the primary exploitation makes an attempt on August 25, one week after Juniper launched patches and as quickly as watchTowr Labs launched a proof-of-concept (PoC) exploit.
In September, vulnerability intelligence agency VulnCheck discovered 1000’s of Juniper gadgets nonetheless weak to assaults utilizing this exploit chain.
CISA added the 4 bugs to its Identified Exploited Vulnerabilities Catalog on November 17, tagging them as “frequent assault vectors for malicious cyber actors” with “important dangers to the federal enterprise.”
The U.S. cybersecurity company issued the first binding operational directive (BOD) of the yr final June, requiring federal companies to safe their Web-exposed or misconfigured networking gear (comparable to Juniper firewalls and switches) inside a two-week window following discovery.
[ad_2]