[ad_1]
Excessive-profile people engaged on Center Jap affairs at universities and analysis organizations in Belgium, France, Gaza, Israel, the U.Ok., and the U.S. have been focused by an Iranian cyber espionage group known as Thoughts Sandstorm since November 2023.
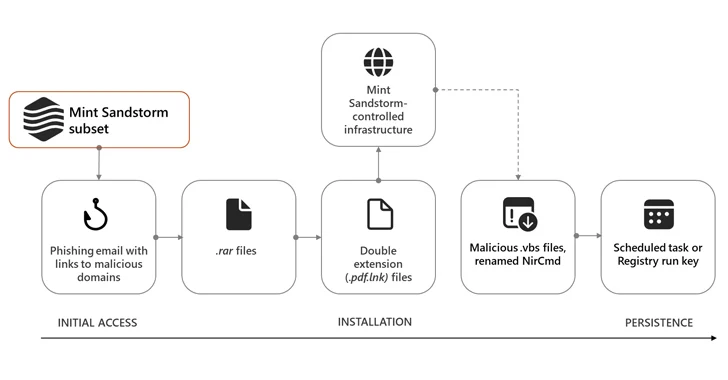
The risk actor “used bespoke phishing lures in an try to socially engineer targets into downloading malicious recordsdata,” the Microsoft Menace Intelligence crew stated in a Wednesday evaluation, describing it as a “technically and operationally mature subgroup of Thoughts Sandstorm.”
The assaults, in choose instances, contain using a beforehand undocumented backdoor dubbed MediaPl, indicating ongoing endeavors by Iranian risk actors to refine their post-intrusion tradecraft.
Mint Sandstorm, also referred to as APT35, Charming Kitten, TA453, and Yellow Garuda, is recognized for its adept social engineering campaigns, even resorting to professional however compromised accounts to ship bespoke phishing emails to potential targets. It is assessed to be affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC).
The sub-cluster, per Redmond, engages in resource-intensive social engineering to single out journalists, researchers, professors, and different people with insights on safety and coverage problems with curiosity to Tehran.
The newest intrusion set is characterised by way of lures pertaining to the Israel-Hamas conflict, sending innocuous emails underneath the guise of journalists and different high-profile people to construct rapport with targets and set up a stage of belief earlier than making an attempt to ship malware to targets.
Microsoft stated it is probably the marketing campaign is an effort undertaken by the nation-state risk actor to gather views on occasions associated to the conflict.
The usage of breached accounts belonging to the folks they sought to impersonate so as to ship the e-mail messages is a brand new Thoughts Sandstorm tactic not seen earlier than, as is its use of the curl command to hook up with the command-and-control (C2) infrastructure.
Ought to the targets have interaction with the risk actor, they’re despatched a follow-up e mail containing a malicious hyperlink that factors to a RAR archive file, which, when opened, results in the retrieval of Visible Fundamental scripts from the C2 server to persist inside the targets’ environments.
The assault chains additional pave the best way for customized implants like MischiefTut or MediaPl, the previous of which was first disclosed by Microsoft in October 2023.
Applied in PowerShell, MischiefTut is a fundamental backdoor that may run reconnaissance instructions, write outputs to a textual content file, and obtain extra instruments on a compromised system. The primary recorded use of the malware dates again to late 2022.
MediaPl, alternatively, masquerades as Home windows Media Participant and is designed to transmit encrypted communications to its C2 server and launch command(s) it has acquired from the server.
“Mint Sandstorm continues to enhance and modify the tooling utilized in targets’ environments, exercise that may assist the group persist in a compromised surroundings and higher evade detection,” Microsoft stated.
“The power to acquire and preserve distant entry to a goal’s system can allow Mint Sandstorm to conduct a spread of actions that may adversely impression the confidentiality of a system.”
The disclosure comes as Dutch newspaper De Volkskrant revealed earlier this month that Erik van Sabben, a Dutch engineer recruited by Israel and U.S. intelligence providers, could have used a water pump to deploy an early variant of the now-infamous Stuxnet malware in an Iranian nuclear facility someday in 2007.
[ad_2]