[ad_1]
An evaluation of the Linux variant of a brand new ransomware pressure referred to as BlackSuit has lined important similarities with one other ransomware household referred to as Royal.
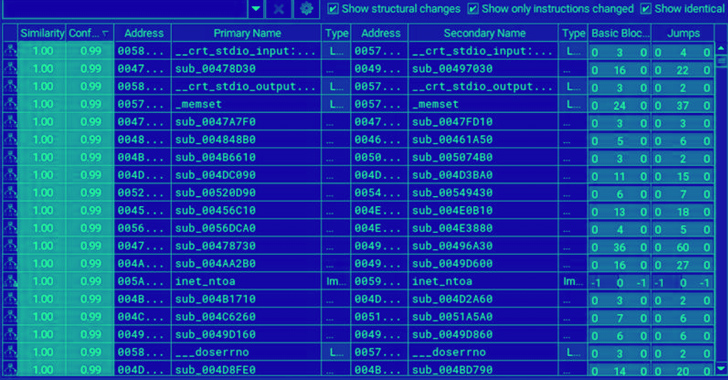
Pattern Micro, which examined an x64 VMware ESXi model focusing on Linux machines, mentioned it recognized an “extraordinarily excessive diploma of similarity” between Royal and BlackSuit.
“In actual fact, they’re almost an identical, with 98% similarities in capabilities, 99.5% similarities in blocks, and 98.9% similarities in jumps based mostly on BinDiff, a comparability instrument for binary recordsdata,” Pattern Micro researchers famous.
A comparability of the Home windows artifacts has recognized 93.2% similarity in capabilities, 99.3% in primary blocks, and 98.4% in jumps based mostly on BinDiff.
BlackSuit first got here to mild in early Could 2023 when Palo Alto Networks Unit 42 drew consideration to its capability to focus on each Home windows and Linux hosts.
In step with different ransomware teams, it runs a double extortion scheme that steals and encrypts delicate knowledge in a compromised community in return for financial compensation. Knowledge related to a single sufferer has been listed on its darkish net leak website.
The newest findings from Pattern Micro present that, each BlackSuit and Royal use OpenSSL’s AES for encryption and make the most of related intermittent encryption methods to hurry up the encryption course of.
The overlaps apart, BlackSuit incorporates extra command-line arguments and avoids a distinct record of recordsdata with particular extensions throughout enumeration and encryption.
“The emergence of BlackSuit ransomware (with its similarities to Royal) signifies that it’s both a brand new variant developed by the identical authors, a copycat utilizing related code, or an affiliate of the Royal ransomware gang that has applied modifications to the unique household,” Pattern Micro mentioned.
On condition that Royal is an offshoot of the erstwhile Conti workforce, it is also attainable that “BlackSuit emerged from a splinter group throughout the authentic Royal ransomware gang,” the cybersecurity firm theorized.
The event as soon as once more underscores the fixed state of flux within the ransomware ecosystem, at the same time as new risk actors emerge to tweak present instruments and generate illicit income.
🔐 Mastering API Safety: Understanding Your True Assault Floor
Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in the direction of ironclad safety. Be part of our insightful webinar!
This features a new ransomware-as-a-service (RaaS) initiative codenamed NoEscape that Cyble mentioned permits its operators and associates to reap the benefits of triple extortion strategies to maximise the impression of a profitable assault.
Triple extortion refers to a three-pronged method whereby knowledge exfiltration and encryption is coupled with distributed denial-of-service (DDoS) assaults towards the targets in an try to disrupt their enterprise and coerce them into paying the ransom.
The DDoS service, per Cyble, is out there for an added $500,000 payment, with the operators imposing circumstances that forbid associates from putting entities positioned within the Commonwealth of Impartial States (CIS) nations.
[ad_2]