[ad_1]
Vietnamese public firms have been focused as a part of an ongoing marketing campaign that deploys a novel backdoor referred to as SPECTRALVIPER.
“SPECTRALVIPER is a closely obfuscated, beforehand undisclosed, x64 backdoor that brings PE loading and injection, file add and obtain, file and listing manipulation, and token impersonation capabilities,” Elastic Safety Labs stated in a Friday report.
The assaults have been attributed to an actor it tracks as REF2754, which overlaps with a Vietnamese menace group referred to as APT32, Canvas Cyclone (previously Bismuth), Cobalt Kitty, and OceanLotus.
Meta, in December 2020, linked the actions of the hacking crew to a cybersecurity firm named CyberOne Group.
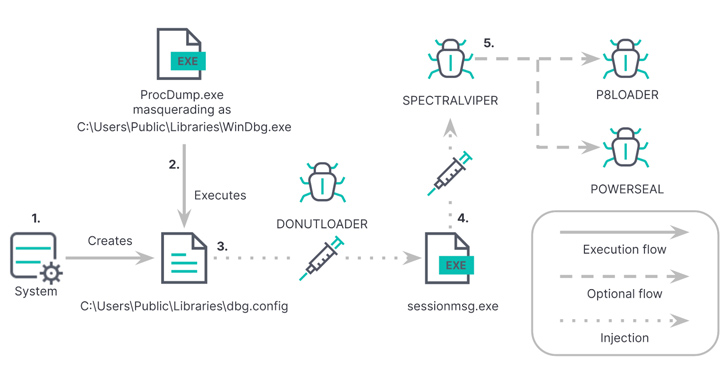
Within the newest an infection circulate unearthed by Elastic, the SysInternals ProcDump utility is leveraged to load an unsigned DLL file that incorporates DONUTLOADER, which, in flip, is configured to load SPECTRALVIPER and different malware equivalent to P8LOADER or POWERSEAL.
SPECTRALVIPER is designed to contact an actor-controlled server and awaits additional instructions whereas additionally adopting obfuscation strategies like management circulate flattening to withstand evaluation.
P8LOADER, written in C++, is able to launching arbitrary payloads from a file or from reminiscence. Additionally used is a purpose-built PowerShell runner named POWERSEAL that is geared up to run provided PowerShell scripts or instructions.
REF2754 is alleged to share tactical commonalities with one other group dubbed REF4322, which is understood to primarily goal Vietnamese entities to deploy a post-exploitation implant known as PHOREAL (aka Rizzo).
The connections have raised the chance that “each REF4322 and REF2754 exercise teams symbolize campaigns deliberate and executed by a Vietnamese state-affiliated menace.”
🔐 Mastering API Safety: Understanding Your True Assault Floor
Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in the direction of ironclad safety. Be a part of our insightful webinar!
The findings come because the intrusion set dubbed REF2924 has been tied to yet one more piece of malware referred to as SOMNIRECORD that employs DNS queries to speak with a distant server and bypass community safety controls.
SOMNIRECORD, like NAPLISTENER, makes use of current open supply tasks to hone its capabilities, enabling it to retrieve details about the contaminated machine, record all operating processes, deploy an online shell, and launch any executable already current within the system.
“Using open supply tasks by the attacker signifies that they’re taking steps to customise current instruments for his or her particular wants and could also be making an attempt to counter attribution makes an attempt,” the corporate stated.
[ad_2]