
[ad_1]

Scammers are impersonating the chapter declare agent for crypto lender Celsius in phishing assaults that try and steal funds from cryptocurrency wallets.
In July 2022, crypto lender Celsius filed for chapter and froze withdrawals from person accounts. Clients have since filed claims in opposition to the corporate, hoping to get well a portion of the funds.
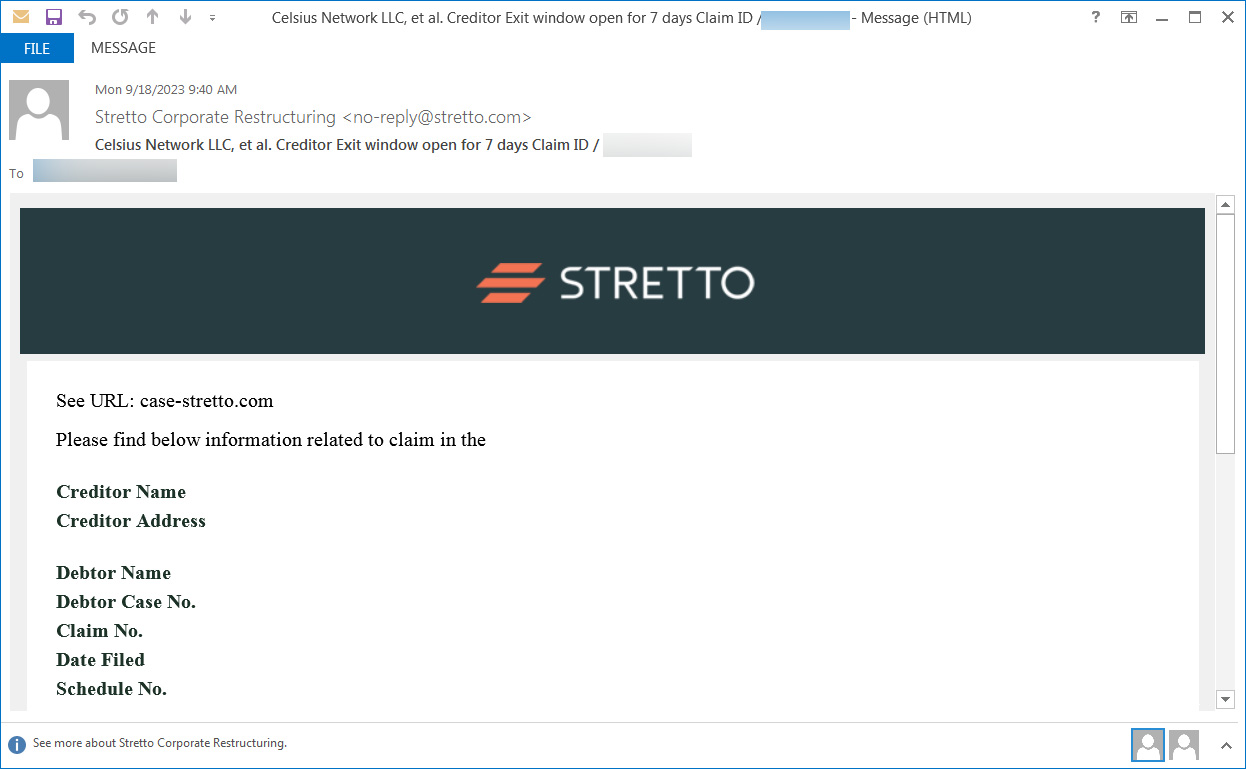
Over the previous few days, individuals have reported receiving phishing emails pretending to be from Stretto, the Claims Agent for the Celsius chapter continuing.
A recipient shared the phishing electronic mail with BleepingComputer, which claims to supply collectors a 7-day exit window to say their frozen funds.
The e-mail says they’re from “Stretto Company Restructing,” utilizing the e-mail tackle no-reply@stretto.com, as proven beneath.
Supply: BleepingComputer
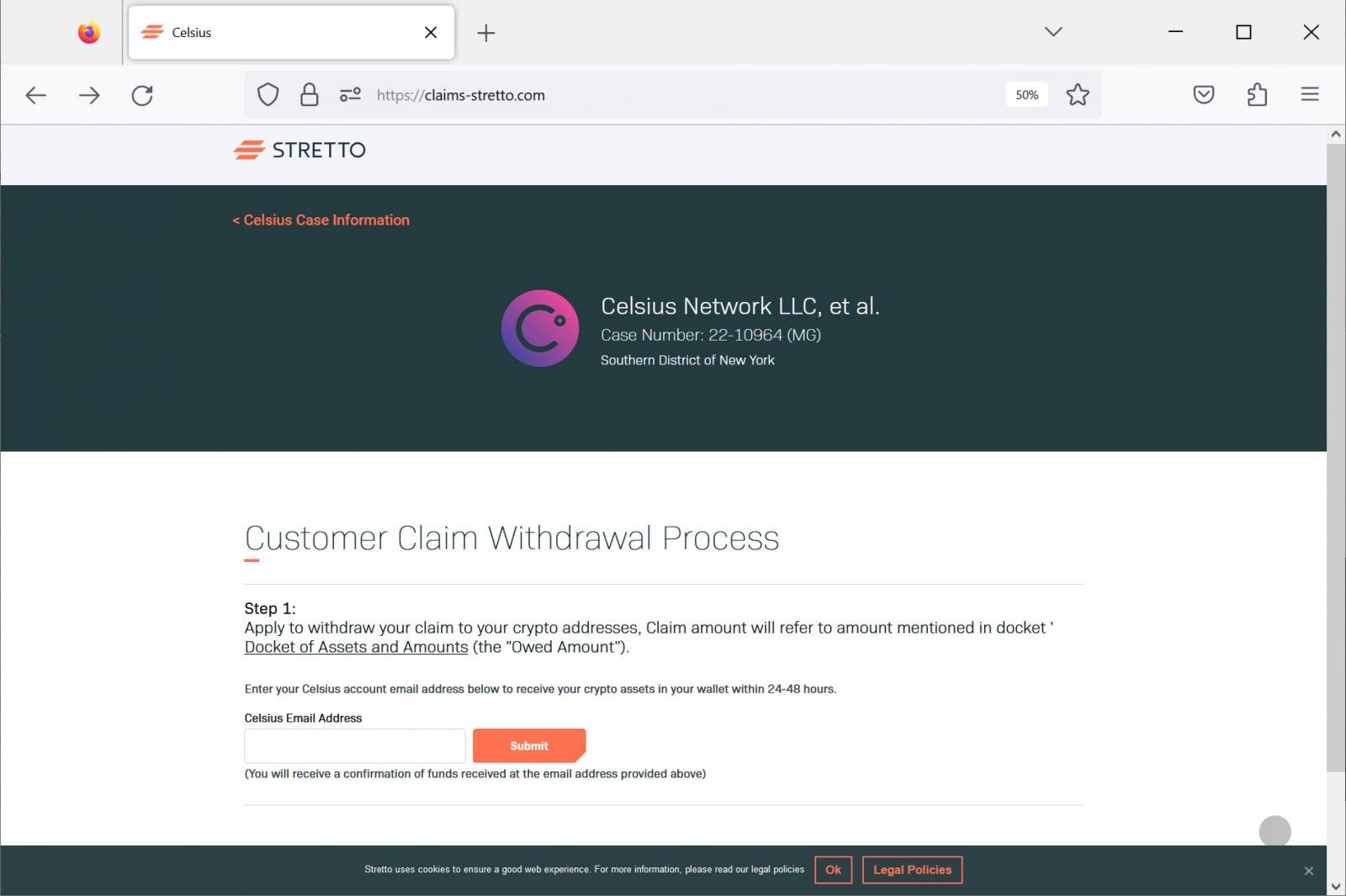
The phishing electronic mail features a hyperlink to the web site case-stretto[.]com, which redirects the recipient to the phishing website claims-stretto[.]com beneath. The claims-stretto[.]com area was registered as we speak and is hosted at a internet hosting supplier within the Seychelles.
The authentic Stretto website for Celsius claims is situated at https://circumstances.stretto.com/celsius/claims/.
Supply: BleepingComputer
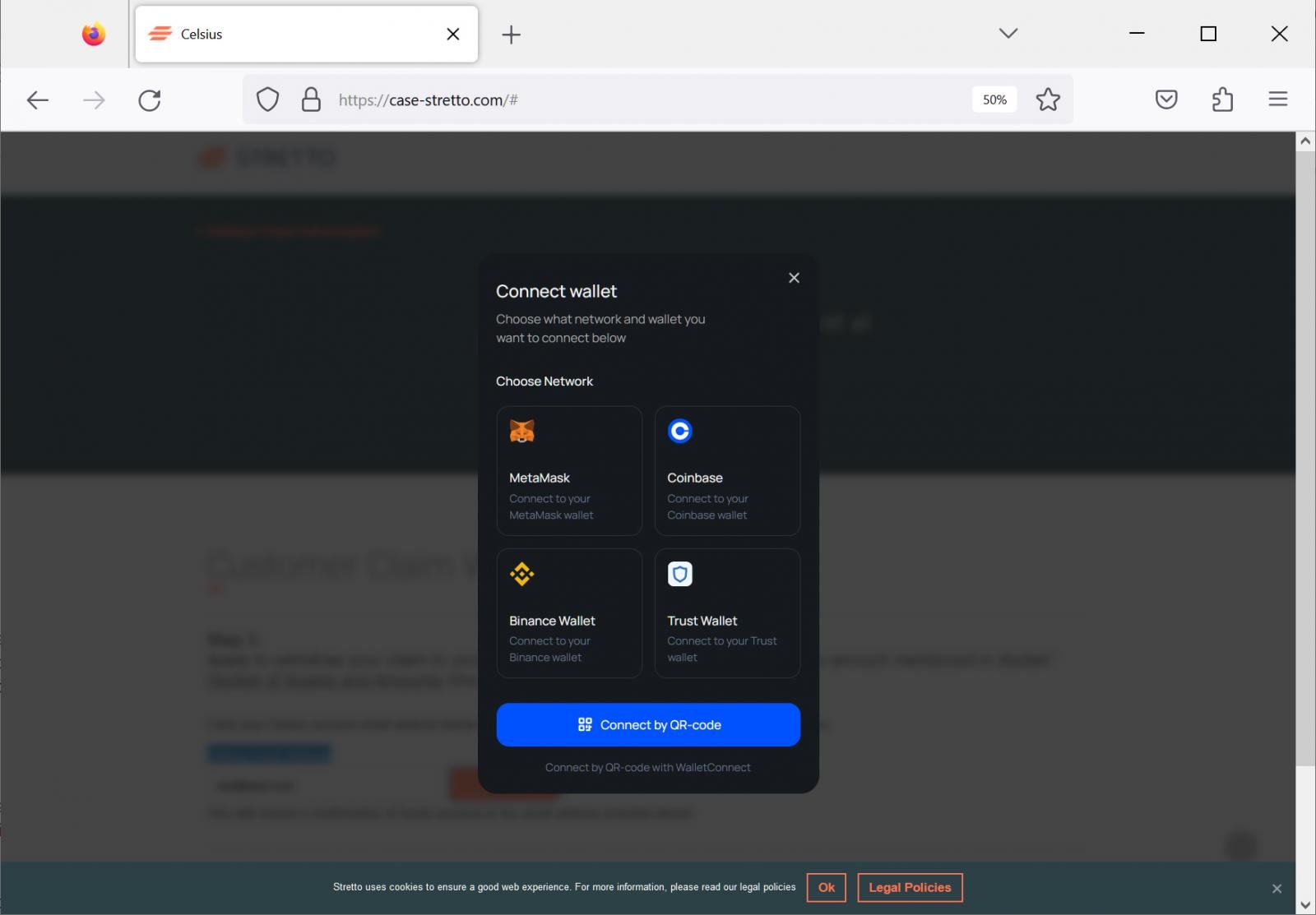
The web page prompts guests to enter their electronic mail tackle to withdraw their declare, and when the submit button is pressed, it opens a WalletConnect immediate to attach your put in cryptocurrency pockets with the web site.
Supply: BleepingComputer
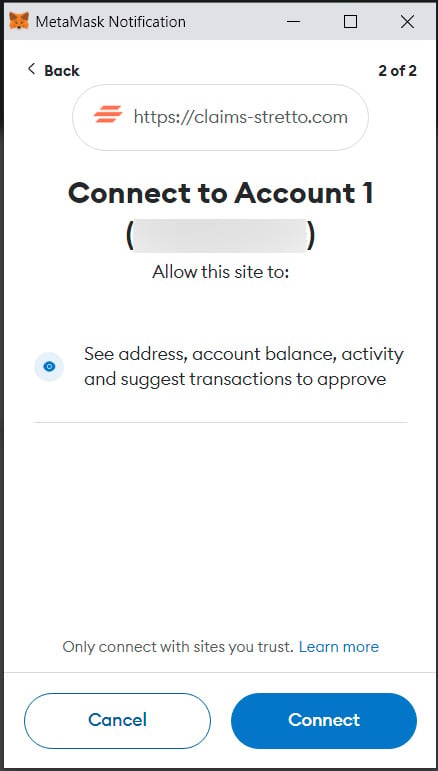
If you happen to join a pockets, the positioning will now have entry to all the data saved inside it, together with crypto addresses, balances, exercise, and the flexibility to counsel transactions.
Supply: BleepingComputer
With this connection in place, the menace actors can try to empty all belongings and NFTs saved throughout the pockets by disguising the transaction as a deposit.
Passes SPF checks
This phishing marketing campaign stands out as a result of the emails move Sender Coverage Framework (SPF) checks, which decide if an electronic mail comes from a sound electronic mail server for the sending area.
SPF performs this test by evaluating the IP tackle of the mail server that sends the e-mail to an inventory of IP addresses discovered within the DNS SPF report for the area used within the ‘Return-Path’ mail header.
On this case, the phishing electronic mail’s return path is ‘bounces+xxx-xx=xxx.com@em6462.stretto.com’, with em6462.stretto.com having an SPF report of v=spf1 ip4:149.72.171.199 -all. This SPF report implies that any emails from 149.72.171.199 needs to be thought of legitimate and never marked as spam.
As these phishing emails originate from 149.72.171.199, which belongs to the e-mail advertising and marketing agency SendGrid, they move the SPF test and are allowed for supply.
That is illustrated beneath (some data is redacted), the place the e-mail is efficiently delivered to Gmail after passing SPF checks.
ARC-Authentication-Outcomes: i=1; mx.google.com;
dkim=move header.i=@stretto.com header.s=s1 header.b=xx;
spf=move (google.com: area of bounces+xxx-xxx-xx=xxx.com@em6462.stretto.com designates 149.72.171.199 as permitted sender) smtp.mailfrom="bounces+xxx-xxx-xx=xxx.com@em6462.stretto.com";
dmarc=move (p=QUARANTINE sp=QUARANTINE dis=NONE) header.from=stretto.com
A recipient of one in every of these phishing emails instructed BleepingComputer that they didn’t have an account at Celsius and by no means filed as a creditor, making it unusual that they acquired this electronic mail.
The menace actors are probably utilizing older contact lists beforehand stolen via hacked cryptocurrency advertising and marketing accounts.
BleepingComputer has reached out to Stretto to verify if their SendGrid account was compromised to ship these emails however has not acquired a reply.
If you happen to obtain an electronic mail claiming to be about Celsius’ claims, please ignore it and test for brand new updates on the case on the authentic https://circumstances.stretto.com/celsius/ website.
Sadly, when you’ve got already visited one in every of these phishing websites and misplaced funds or NFTs after connecting your pockets, there’s probably no method to get well your belongings.
Celsius has beforehand reported related phishing assaults used to steal collectors’ funds.
[ad_2]