
[ad_1]

The Metropolis of Dallas, Texas, mentioned this week that the Royal ransomware assault that pressured it to close down all IT techniques in Might began with a stolen account.
Royal gained entry to the Metropolis’s community utilizing a stolen area service account in early April and maintained entry to the compromised techniques between April 7 and Might 4.
Throughout this era, they efficiently collected and exfiltrated 1.169 TB value of information primarily based on system log information evaluation carried out by metropolis officers and exterior cybersecurity consultants.
The gang additionally ready the ransomware deployment part by dropping Cobalt Strike command-and-control beacons throughout the Metropolis’s techniques. At 2 AM on Might third, Royal began deploying the ransomware payloads, utilizing legit Microsoft administrative instruments to encrypt servers.
After detecting the assault, the Metropolis initiated mitigation efforts, taking high-priority servers offline to impede Royal’s progress. Concurrently, it began service restoration efforts with the assistance of groups of inside and exterior cybersecurity consultants.
The method of restoring all servers took simply over 5 weeks, from Might ninth, when the monetary server was revived, to June thirteenth, when the final server affected by the assault, the waste administration server, was restored.
“The Metropolis reported to the TxOAG that private info of 26,212 Texas residents and a complete of 30,253 people was probably uncovered because of the assault,” the Metropolis mentioned in a autopsy printed this week.
“The OAG’s web site indicated that private info similar to names, addresses, social safety info, well being info, medical insurance info, and different such info was uncovered by Royal.”
Up to now, the Dallas Metropolis Council has set a price range of $8.5 million for ransomware assault restoration efforts, with the ultimate prices to be shared later.
Dallas is the fourth-largest metropolitan space and the ninth-largest Metropolis in the US, with a inhabitants of roughly 2.6 million individuals.
Ransom notes delivered by way of community printers
Native media first reported that the Metropolis’s police communications and IT techniques have been shut down Monday morning, Might third, due to a suspected ransomware assault.
“Wednesday morning, the Metropolis’s safety monitoring instruments notified our Safety Operations Heart (SOC) {that a} seemingly ransomware assault had been launched inside our surroundings. Subsequently, the Metropolis has confirmed that various servers have been compromised with ransomware, impacting a number of practical areas, together with the Dallas Police Division Web site,” the Metropolis of Dallas defined in an announcement issued on Might third.
“The Metropolis crew, together with its distributors, are actively working to isolate the ransomware to stop its unfold, to take away the ransomware from contaminated servers, and to revive any providers at the moment impacted. The Mayor and Metropolis Council was notified of the incident pursuant to the Metropolis’s Incident Response Plan (IRP).”
Community printers on the Metropolis of Dallas’ community started printing out ransom notes the morning of the incident, permitting BleepingComputer to verify that the Royal ransomware gang was behind the assault after an image of the notice was shared with us.
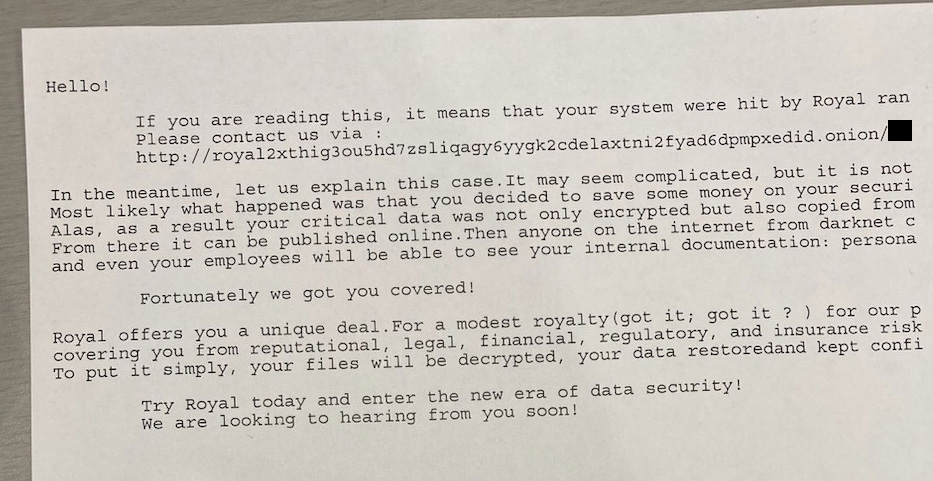
The Royal ransomware gang is believed to have emerged as an offshoot of the Conti cybercrime gang, gaining prominence after Conti shut down operations.
Upon its launch in January 2022, Royal initially used encryptors from different ransomware operations, similar to ALPHV/BlackCat, to keep away from drawing consideration. Nonetheless, they subsequently started using their very own encryptor, Zeon, of their assaults all year long.
The ransomware operation underwent a rebranding in direction of the top of 2022, adopting the identify “Royal” and rising as one of the vital lively ransomware gangs focusing on enterprises.
Whereas Royal is understood for exploiting safety flaws in publicly accessible gadgets to breach targets’ networks, it additionally continuously resorts to callback phishing assaults to achieve preliminary entry to enterprise networks.
When the targets name the cellphone numbers embedded in emails camouflaged as subscription renewals, the attackers use social engineering to trick the victims into putting in distant entry software program that gives the menace actors with entry to their community.
[ad_2]