[ad_1]
Risk actors are benefiting from Android’s WebAPK know-how to trick unsuspecting customers into putting in malicious internet apps on Android telephones which are designed to seize delicate private data.
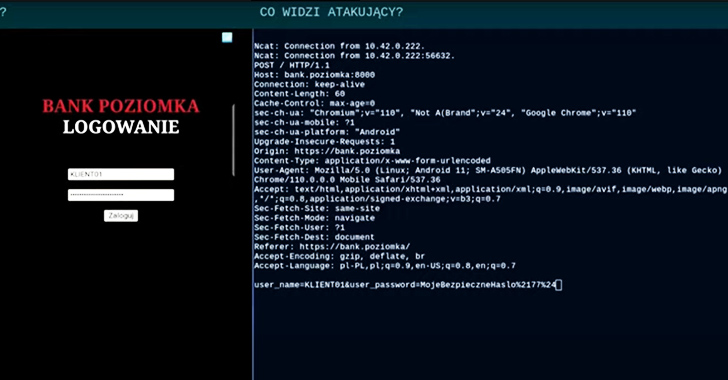
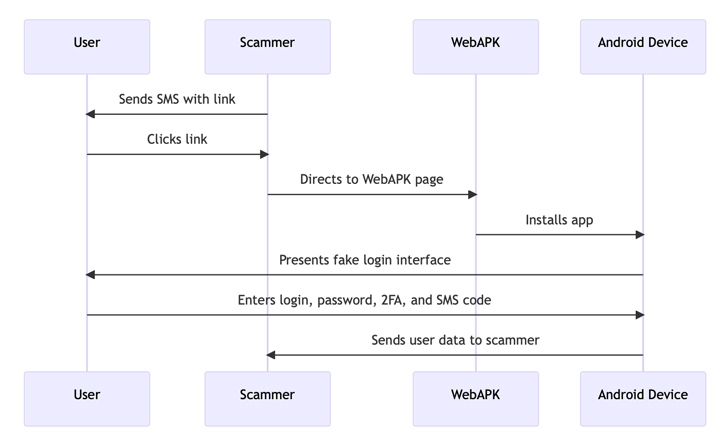
“The assault started with victims receiving SMS messages suggesting the necessity to replace a cell banking utility,” researchers from CSIRT KNF mentioned in an evaluation launched final week. “The hyperlink contained within the message led to a website that used WebAPK know-how to put in a malicious utility on the sufferer’s system.”
The applying impersonates PKO Financial institution Polski, a multinational banking and monetary companies firm headquartered in Warsaw. Particulars of the marketing campaign have been first shared by Polish cybersecurity agency RIFFSEC.
WebAPK permits customers to put in progressive internet apps (PWAs) to their dwelling display screen on Android gadgets with out having to make use of the Google Play Retailer.
“When a person installs a PWA from Google Chrome and a WebAPK is used, the minting server “mints” (packages) and indicators an APK for the PWA,” Google explains in its documentation.
“That course of takes time, however when the APK is prepared, the browser installs that app silently on the person’s system. As a result of trusted suppliers (Play Providers or Samsung) signed the APK, the telephone installs it with out disabling safety, as with all app coming from the shop. There isn’t a want for sideloading the app.”
As soon as put in, the faux banking app (“org.chromium.webapk.a798467883c056fed_v2”) urges customers to enter their credentials and two-factor authentication (2FA) tokens, successfully ensuing of their theft.
“One of many challenges in countering such assaults is the truth that WebAPK purposes generate completely different package deal names and checksums on every system,” CSIRT KNF mentioned. “They’re dynamically constructed by the Chrome engine, which makes the usage of this information as Indicators of Compromise (IoC) troublesome.”
Protect Towards Insider Threats: Grasp SaaS Safety Posture Administration
Nervous about insider threats? We have got you lined! Be part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
To counter such threats, it is advisable to dam web sites that use the WebAPK mechanism to hold out phishing assaults.
The event comes as Resecurity revealed that cybercriminals are more and more leveraging specialised system spoofing instruments for Android which are marketed on the darkish internet in a bid to impersonate compromised account holders and bypass anti-fraud controls.
The antidetect instruments, together with Enclave Service and MacFly, are able to spoofing cell system fingerprints and different software program and community parameters which are analyzed by anti-fraud programs, with risk actors additionally leveraging weak fraud controls to conduct unauthorized transactions by way of smartphones utilizing banking malware resembling TimpDoor and Clientor.
“Cybercriminals use these instruments to entry compromised accounts and impersonate reputable clients by exploiting stolen cookie information, impersonating hyper-granular system identifiers, and using fraud victims’ distinctive community settings,” the cybersecurity firm mentioned.
[ad_2]