
[ad_1]

Hackers are utilizing a pretend Android app named ‘SafeChat’ to contaminate units with spyware and adware malware that steals name logs, texts, and GPS areas from telephones.
The Android spyware and adware is suspected to be a variant of “Coverlm,” which steals information from communication apps similar to Telegram, Sign, WhatsApp, Viber, and Fb Messenger.
CYFIRMA researchers say the Indian APT hacking group ‘Bahamut’ is behind the marketing campaign, with their newest assaults carried out primarily by spear phishing messages on WhatsApp that ship the malicious payloads on to the sufferer.
Additionally, the CYFIRMA’s analysts spotlight a number of TTP similarities to a different Indian state-sponsored risk group, the ‘DoNot APT’ (APT-C-35), that has beforehand infested Google Play with pretend chat apps performing as spyware and adware.
Late final yr, ESET reported that the Bahamut group was utilizing pretend VPN apps for the Android platform that included intensive spyware and adware capabilities.
Within the newest marketing campaign noticed by CYFIRMA, Bahamut targets people in South Asia.
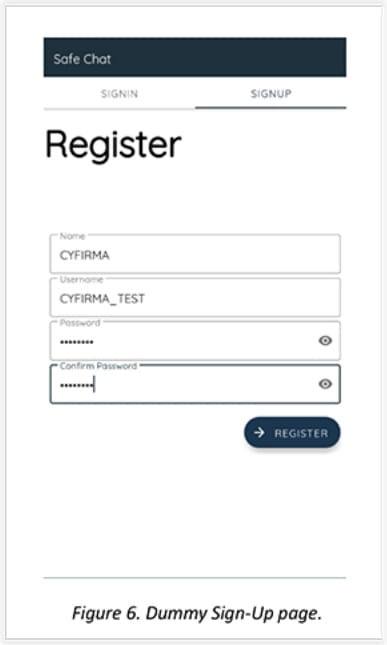
“Secure Chat” particulars
Whereas CYFIRMA would not delve into the specifics of the social engineering side of the assault, it’s normal for victims to be persuaded into putting in a chat app underneath the pretext of transitioning the dialog to a safer platform.
The analysts report that Secure Chat includes a deceiving interface that makes it seem as an actual chat app and in addition takes the sufferer by a seemingly respectable person registration course of that provides credibility and serves as a wonderful cowl for the spyware and adware.
One essential step within the an infection is the acquisition of permissions to make use of the Accessibility Providers, that are subsequently abused to mechanically grant the spyware and adware extra permissions.
These extra permissions allow the spyware and adware to entry to the sufferer’s contacts listing, SMS, name logs, exterior machine storage, and fetch exact GPS location information from the contaminated machine.
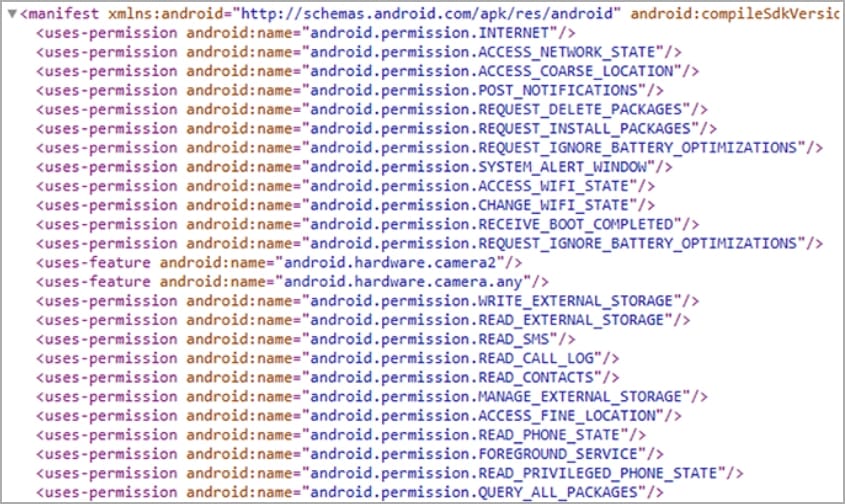
The app additionally requests the person to approve exclusion from Android’s battery optimization subsystem, which terminates background processes when the person is not actively partaking with the app.
“One other snippet from the Android Manifest file reveals that the risk actor designed the app to work together with different already put in chat purposes,” explains CYFIRMA.
“The interplay will happen utilizing intents, OPEN_DOCUMENT_TREE permission will choose particular directories and entry apps talked about in intent.”

A devoted information exfiltration module transfers info from the machine to the attacker’s C2 server by port 2053.
The stolen information is encrypted utilizing one other module that helps RSA, ECB, and OAEPPadding. On the similar time, the attackers additionally use a “letsencrypt” certificates to evade any community information interception efforts towards them.
CYFIRMA concludes the report by saying that it holds sufficient proof to hyperlink Bahamut to engaged on behalf of a particular state authorities in India.
Additionally, utilizing the identical certificates authority because the DoNot APT group, related information stealing methodologies, widespread focusing on scope, and the usage of Android apps to contaminate targets all point out overlap or shut collaboration between the 2 teams.
[ad_2]