
[ad_1]

A novel malware named ‘Agent Raccoon’ (or Agent Racoon) is being utilized in cyberattacks in opposition to organizations in the US, the Center East, and Africa.
The attackers are believed to be nation-state risk actors found by Palo Alto Community’s Unit 42, which stories seeing victims spanning numerous sectors, together with authorities, telecommunications, training, actual property, retail, and non-profit organizations.
“We assess with medium confidence that this risk exercise cluster aligns to nation-state associated risk actors as a result of nature of the organizations that had been compromised, the TTPs noticed and the customization of the device set,” explains the Unit 42 researchers.
“We now have not confirmed a specific nation-state or risk group.”
The collection of targets, nature of the deployed instruments, knowledge exfiltration strategies, focused intelligence, and the covert character of the assaults counsel that their purpose is espionage.
Agent Raccoon backdoor
Agent Raccoon is a .NET malware disguised as a Google Replace or Microsoft OneDrive Updater that leverages the DNS (Area Identify Service) protocol to ascertain a covert communication channel with the attackers’ C2 (command and management) infrastructure.
The backdoor constructs queries with Punycode-encoded subdomains for evasion, whereas it additionally contains random values to make communications more durable to trace.
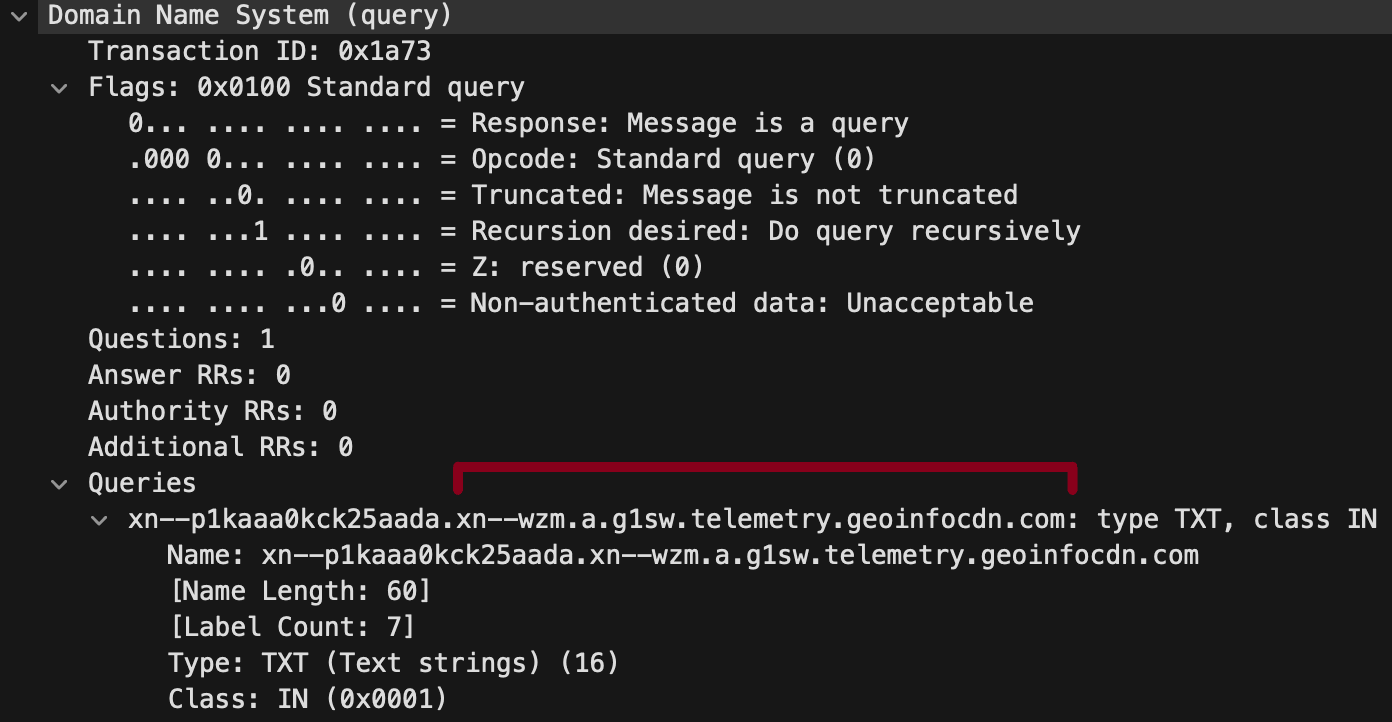
Unit 42 notes that whereas the malware itself lacks a persistence mechanism, their observations counsel that it’s executed by scheduled duties.
The malware is able to distant command execution, file importing and downloading, and offering distant entry to the contaminated system.
The analysts additionally be aware that they’ve captured totally different samples of Agent Raccoon with slight code variations and optimizations in its settings, indicating that the malware’s authors are actively growing and adapting it to particular operational necessities.
Different distinctive instruments
Other than Agent Raccoon, the attackers additionally used a custom-made model of the Mimikatz credential dumping utility, named ‘Mimilite,’ and a DLL credential stealer mimicking the Home windows Community Supplier module, named ‘Ntospy.’
Ntospy registers as a respectable Community Supplier module named “credman” to hijack the authentication course of and seize person credentials, a well-documented assault methodology.
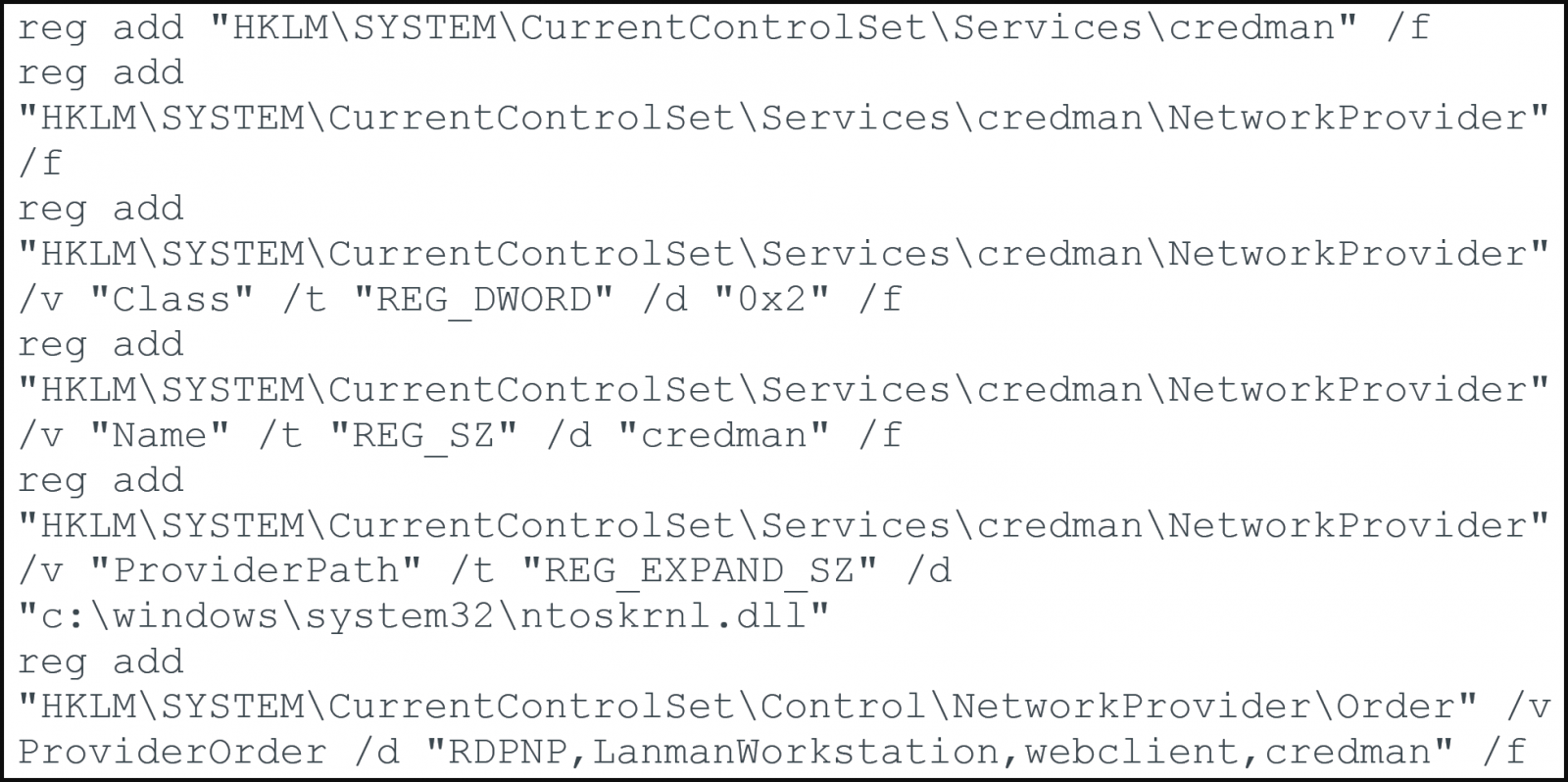
This device, too, makes use of filenames that resemble Microsoft Replace recordsdata and shops intercepted credentials in plaintext kind domestically on the breached gadget.
Lastly, the attackers use PowerShell snap-ins to steal emails from Microsoft Change servers or steal victims’ Roaming Profile folders, compressing the listing with 7-Zip for effectivity and stealth.
The noticed e-mail exfiltration course of concerned distinct search standards for every inbox, indicating a focused knowledge harvesting strategy that matches the presumed espionage operational profile.
The unknown exercise cluster has notable overlaps with one other risk actor that Unit 42 tracks as ‘CL-STA-0043,’ which is characterised as a nation-state risk actor with medium confi
[ad_2]