
[ad_1]

A brand new ‘File Archivers within the Browser’ phishing package abuses ZIP domains by displaying pretend WinRAR or Home windows File Explorer home windows within the browser to persuade customers to launch malicious recordsdata.
Earlier this month, Google started providing the power to register ZIP TLD domains, corresponding to bleepingcomputer.zip, for internet hosting web sites or e mail addresses.
Because the TLD’s launch, there was fairly a little bit of debate over whether or not they’re a mistake and will pose a cybersecurity threat to customers.
Whereas some specialists consider the fears are overblown, the principle concern is that some websites will routinely flip a string that ends with ‘.zip,’ like setup.zip, right into a clickable hyperlink that could possibly be used for malware supply or phishing assaults.
For instance, if you happen to ship somebody directions on downloading a file referred to as setup.zip, Twitter will routinely flip setup.zip right into a hyperlink, making individuals suppose they need to click on on it to obtain the file.
Supply: BleepingComputer
Once you click on on that hyperlink, your browser will try to open the https://setup.zip web site, which may redirect you to a different web site, present an HTML web page, or immediate you to obtain a file.
Nevertheless, like all malware supply or phishing campaigns, you should first persuade a person to open a file, which might be difficult.
A file archiver within the browser
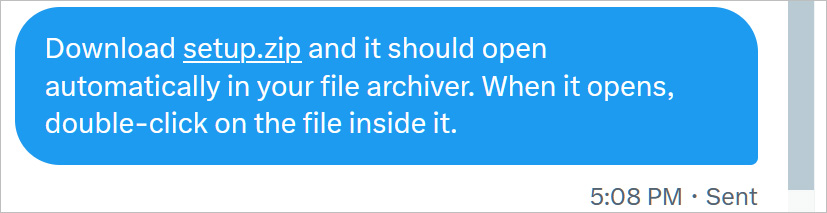
Safety researcher mr.d0x has developed a intelligent phishing toolkit that permits you to create pretend in-browser WinRar cases and File Explorer Home windows which might be displayed on ZIP domains to trick customers into considering they’re opened .zip file.
“With this phishing assault, you simulate a file archiver software program (e.g. WinRAR) within the browser and use a .zip area to make it seem extra authentic,” explains a new weblog publish by the researcher.
In an illustration shared with BleepingComputer, the toolkit can be utilized to embed a pretend WinRar window immediately within the browser when a .zip area is opened, making it seem like the person opened a ZIP archive and is now seeing the recordsdata inside it.
Whereas it appears to be like good when displayed within the browser, it shines as a popup window, as you’ll be able to take away the handle bar and scrollbar, leaving what seems to be a WinRar window displayed on the display, as proven beneath.
Supply: BleepingComputer
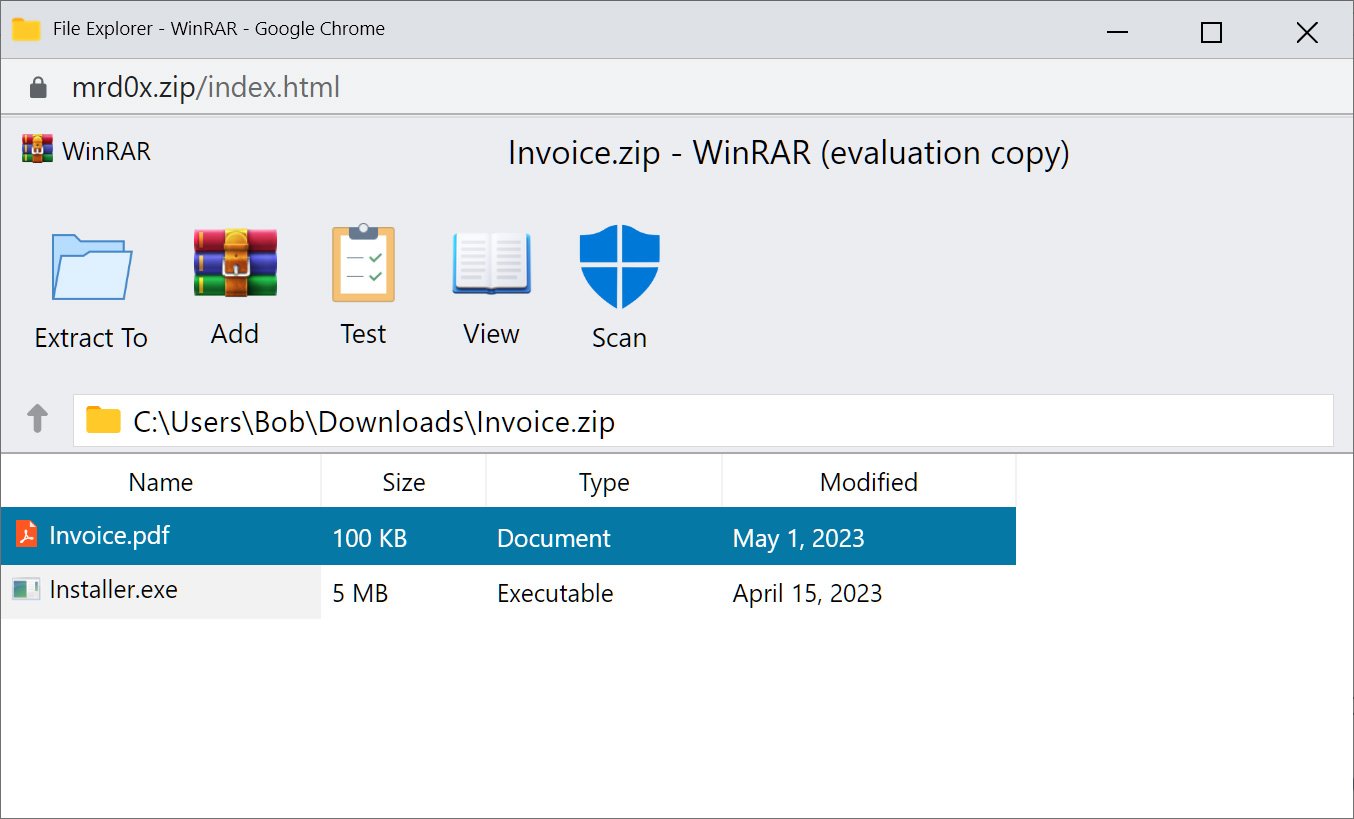
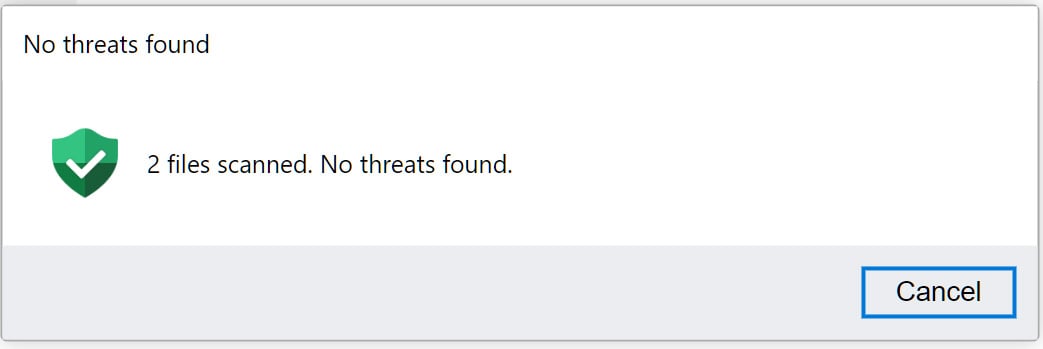
To make the pretend WinRar window much more convincing, the researchers applied a pretend safety Scan button that, when clicked, says that the recordsdata had been scanned and no threats had been detected.
Supply: BleepingComputer
Whereas the toolkit nonetheless shows the browser handle bar, it’s nonetheless prone to trick some customers into considering this can be a authentic WinRar archive. Moreover, inventive CSS and HTML may seemingly be used to refine the toolkit additional.
mr.d0x additionally created one other variant that shows a pretend in-browser Home windows File Explorer pretending to open a ZIP file. This template is extra of a work-in-progress, so has some objects lacking.
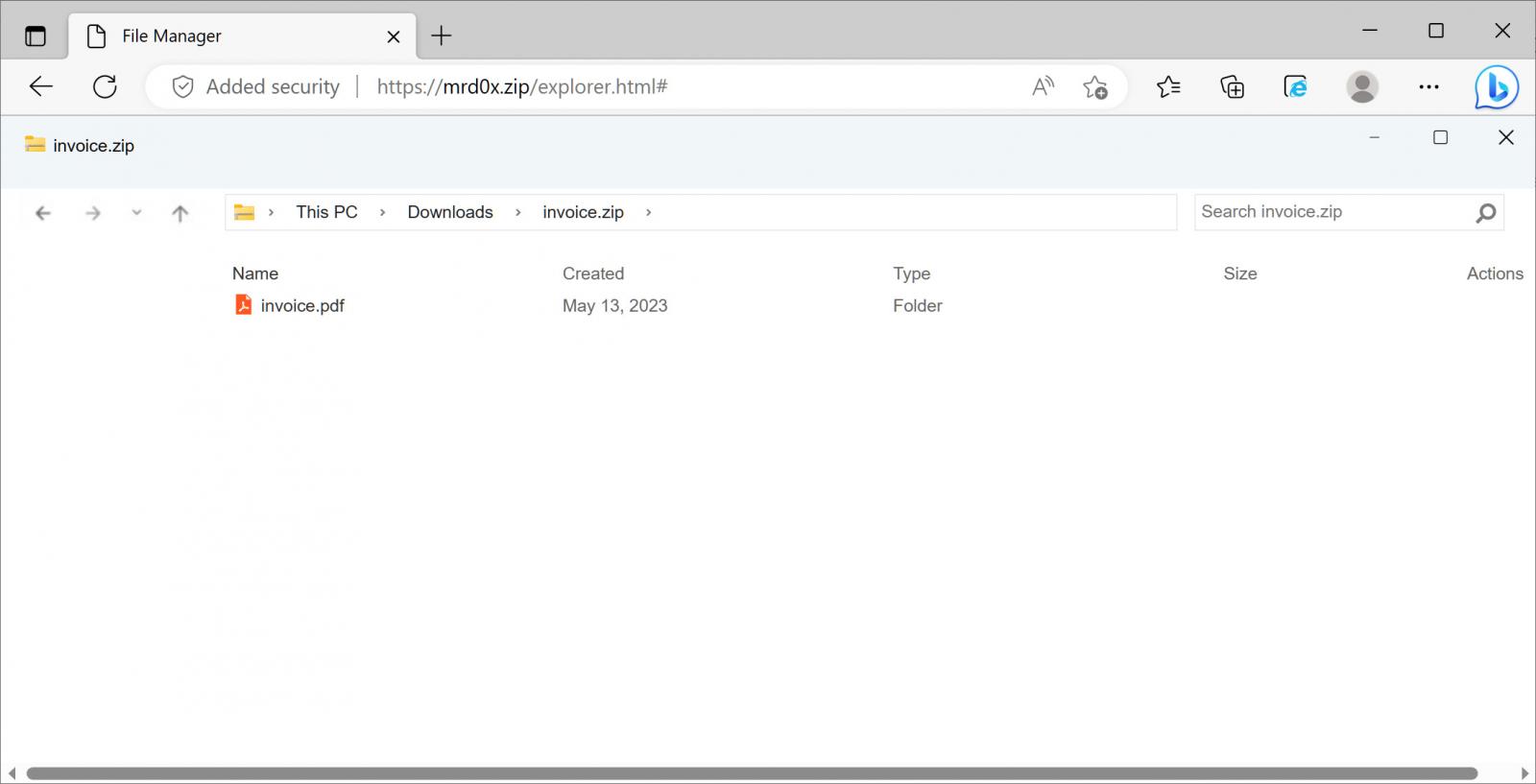
Supply: BleepingComputer
Abusing the phishing toolkit
mr.d0x explains that this phishing toolkit can be utilized for each credential theft and malware supply.
For instance, if a person double-clicks on a PDF within the pretend WinRar window, it may redirect the customer to a different web page asking for his or her login credentials to correctly view the file.
The toolkit can be used to ship malware by displaying a PDF file that downloads a equally named .exe as an alternative when clicked. For instance, the pretend archive window may present a doc.pdf file, however when clicked, the browser downloads doc.pdf.exe.
As Home windows doesn’t present file extensions by default, the person will simply see a PDF file of their downloads folder and probably double-click on it, not realizing it is an executable.
Of explicit curiosity is how Home windows searches for recordsdata and, when not discovered, makes an attempt to open the searched-for string in a browser. If that string is a authentic area, then the web site will probably be opened; in any other case, it’s going to present search outcomes from Bing.
If somebody registers a zipper area that’s the identical as a typical file title and somebody performs a search in Home windows, the working system will routinely open the positioning within the browser.
If that web site hosted the ‘File Archivers within the Browser’ phishing package, it may trick a person into considering WinRar displayed an precise ZIP archive.
This method illustrates how ZIP domains might be abused to to create intelligent phishing assaults and malware supply or credential theft.
mr.d0x is thought for earlier intelligent phishing toolkits, corresponding to utilizing VNC for phishing to bypass MFA and the Browser-in-the-Browser approach. Risk actors used the latter to steal Steam credentials.
[ad_2]