[ad_1]
Israeli organizations had been focused as a part of two completely different campaigns orchestrated by the Iranian nation-state actor often known as OilRig in 2021 and 2022.
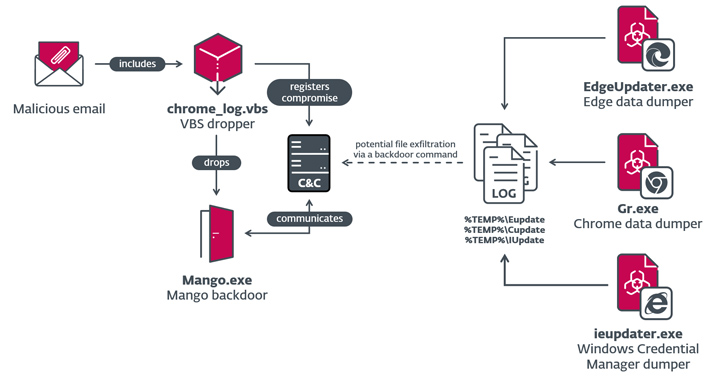
The campaigns, dubbed Outer Area and Juicy Combine, entailed using two beforehand documented first-stage backdoors referred to as Photo voltaic and Mango, which had been deployed to gather delicate data from main browsers and the Home windows Credential Supervisor.
“Each backdoors had been deployed by VBS droppers, presumably unfold through spear-phishing emails,” ESET safety researcher Zuzana Hromcová stated in a Thursday evaluation.
OilRig (aka APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten) is the title assigned to an intrusion set affiliated with Iran’s Ministry of Intelligence and Safety (MOIS). Lively since 2014, the risk actor has used a variety of instruments at its disposal to hold out data theft.

Earlier this February, Development Micro found OilRig’s use of a easy backdoor to steal customers’ credentials, highlighting its “flexibility to jot down new malware based mostly on researched buyer environments and ranges of entry.”
The group has additionally been noticed delivering an up to date model of SideTwist as a part of a phishing assault seemingly concentrating on U.S. companies.
That stated, using Mango malware was beforehand highlighted by each ESET and Microsoft in Could 2023, with the latter attributing it to an rising exercise cluster it tracks below the title Storm-0133.
Storm-0133, additionally related to MOIS, completely targets Israeli native authorities businesses and corporations serving the protection, lodging, and healthcare sectors, the Home windows maker stated.
The most recent findings from the Slovak cybersecurity agency set up the group’s continued deal with Israel, utilizing spear-phishing lures to trick potential targets into putting in the malware through booby-trapped attachments.
Within the Outer Area marketing campaign noticed in 2021, OilRig compromised an Israeli human assets web site and subsequently used it as a command-and-control (C2) server for Photo voltaic, a fundamental C#/.NET backdoor able to downloading and executing recordsdata and gathering data.
Photo voltaic additionally acts as a automobile to deploy a downloader named SampleCheck5000 (or SC5k), which makes use of the Workplace Trade Net Providers (EWS) API to obtain extra instruments for execution, in addition to a utility to exfiltrate information from the Chrome net browser known as MKG.
“As soon as SC5k logs into the distant Trade server, it retrieves all of the emails within the Drafts listing, types them by most up-to-date, preserving solely the drafts which have attachments,” Hromcová stated.
AI vs. AI: Harnessing AI Defenses In opposition to AI-Powered Dangers
Able to deal with new AI-driven cybersecurity challenges? Be part of our insightful webinar with Zscaler to deal with the rising risk of generative AI in cybersecurity.
“It then iterates over each draft message with an attachment, in search of JSON attachments that include “information” within the physique. It extracts the worth from the important thing information within the JSON file, base64 decodes and decrypts the worth, and calls cmd.exe to execute the ensuing command line string.”
The outcomes of the command execution are staged and despatched again to the operators through a brand new e mail message on the Trade server and saving it as a draft.
The Juicy Combine marketing campaign of 2022 concerned using Mango, an improved model of Photo voltaic incorporating extra capabilities and obfuscation strategies. For C2 functions, the risk actor compromised a authentic Israeli job portal web site.
“OilRig continues to innovate and create new implants with backdoor-like capabilities whereas discovering new methods to execute instructions on distant techniques,” Hromcová stated.
“The group deploys a set of customized post-compromise instruments which can be used to gather credentials, cookies, and shopping historical past from main browsers and from the Home windows Credential Supervisor.”
[ad_2]