
[ad_1]

Hackers have been exploiting the 2 zero-day vulnerabilities in Ivanti Join Safe disclosed this week since early December to deploy a number of households of customized malware for espionage functions.
Recognized as CVE-2023-46805 and CVE-2024-21887, the safety points enable bypassing authentication and injecting arbitrary instructions on weak techniques. Ivanti stated that the attackers focused a small variety of its prospects.
A report from Mandiant, who works with Ivanti investigating the incident, notes that the risk actor behind the assaults is engaged in espionage and is at present tracked internally as UNC5221.
At present, risk monitoring service Shadowserver has posted on X that its scanners detect 17,100 Invanti CS home equipment on the general public internet, most of them in the USA.
Nonetheless, there is no such thing as a indication to what number of of them are weak.
Deployed malware
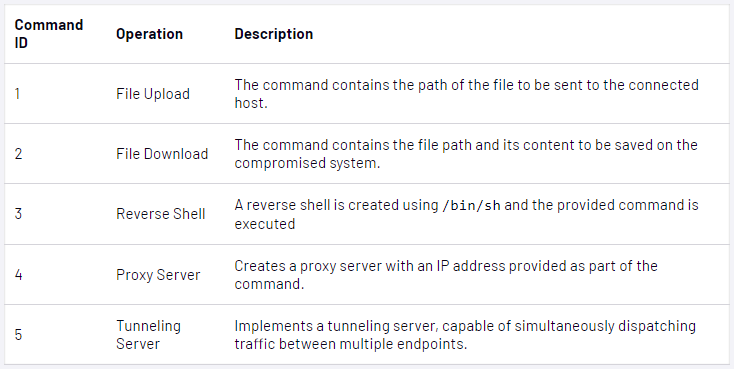
Mandiant discovered that UNC5221 makes use of a set of instruments through the post-compromise stage that features 5 customized malware for planting webshells, executing instructions, dropping payloads, and stealing credentials.
Right here’s a abstract of the instruments used within the assaults:
- Zipline Passive Backdoor: customized malware that may intercept community visitors, helps add/obtain operations, creating reverse shells, proxy servers, server tunneling
- Thinspool Dropper: customized shell script dropper that writes the Lightwire internet shell onto Ivanti CS, securing persistence
- Wirefire internet shell: customized Python-based internet shell supporting unauthenticated arbitrary command execution and payload dropping
- Lightwire internet shell: customized Perl internet shell embedded in a reliable file, enabling arbitrary command execution
- Warpwire harverster: customized JavaScript-based instrument for harvesting credentials at login, sending them to a command and management (C2) server
- PySoxy tunneler: facilitates community visitors tunneling for stealthiness
- BusyBox: multi-call binary combining many Unix utilities utilized in varied system duties
- Thinspool utility (sessionserver.pl): used to remount the filesystem as ‘learn/write’ to allow malware deployment
“ZIPLINE is probably the most notable of those households, it’s a passive backdoor that hijacks an exported perform settle for() from libsecure.so. ZIPLINE intercepts incoming community visitors and helps file switch, reverse shell, tunneling, and proxying,” acknowledged a Mandiant safety researcher on X (previously Twitter).
Mandiant additionally discovered that the attackers used compromised end-of-life Cyberoam VPN home equipment as C2 servers, with their location set in the identical area because the goal, to evade detection.
Volexity beforehand reported seeing indicators of the assaults being carried out by Chinese language state-sponsored risk actors. Nonetheless, Mandiant’s report doesn’t make any attribution or present details about the potential origin or affiliation of the risk actor.
The Google firm says there’s not sufficient information to evaluate the origin of UNC5221 with confidence and famous that its exercise isn’t linked to any beforehand identified risk teams.
Even with out attribution, using customized malware that gives continued entry signifies that “UNC5221 meant to keep up its presence on a subset of excessive precedence targets” even after a patch turned accessible.
Mandiant suspects that UNC5221 is a sophisticated persistent risk (APT) that set sight on high-priority targets.
System admins are reminded that there’s at present no safety replace that addresses the 2 zero-days, however Ivanti gives mitigations that ought to be carried out instantly.
[ad_2]