[ad_1]
Having labored in quite a lot of cybersecurity roles for giant firms and startups for 20 years, Toptal cybersecurity advisor Ilia Tivin has a deep understanding of the sector—previous, current, and future. This Q&A is a abstract of a latest ask-me-anything-style Slack discussion board wherein Tivin fielded questions on synthetic intelligence (AI) in cybersecurity from different Toptal engineers and safety professionals world wide.
Editor’s observe: Some questions and solutions have been edited for readability and brevity.
Present and Future Makes use of of AI in Cybersecurity
Do you suppose fashionable cybersecurity requires AI options?
—Ok.S., Montreal, Canada
Sure, I do suppose AI can be required sooner or later. To be frank, AI’s capability for creating exploits is pretty weak in the present day. However that’s going to escalate over time—and so ought to our defenses.
Did you ever encounter a enterprise case wherein AI was used to search out safety breaches?
—J.O., Fortaleza, Brazil
The reply depends upon the way you outline a safety breach. AI that’s correctly programmed to go looking and sift by way of code can positively be used to establish vulnerabilities. You too can have AI generate very persuasive phishing emails that incorporate particular particulars regarding your group. I haven’t but seen something exterior of phishing emails, however that doesn’t imply it hasn’t occurred.
What are the downsides of AI in cybersecurity?
—Ok.B., Bergerac, France
The downsides of AI in cybersecurity are the identical because the downsides of AI in each different discipline. Once we apply AI, we delegate a layer of decision-making to a robotic. However typically we can’t totally perceive how the robotic arrives at its selections. If AI decides wrongly about safety automations, checks, or compliance, for instance, it may possibly result in vital regulatory fines, safety compromises, or lack of mental property.
What new cybersecurity dangers would possibly fashionable AI (e.g., generative AI) create?
—R.L., Lake Oswego, United States
A threat that involves thoughts is overreliance on AI, even when it advantages from the most recent developments. As builders transfer to make use of AI to code, in addition to to examine their code utilizing that very same AI, they might inadvertently introduce safety vulnerabilities to the code.
How would possibly AI enhance cybersecurity sooner or later?
—N.H., Tuzla, Bosnia and Herzegovina
First, AI will hopefully cease supplying unsuitable info and errors. I see a transfer towards extra automation worldwide. I additionally predict the enhancement of inspection strategies, contingent on the nations and jurisdictions wherein the varied AI firms function. Inspection enhancement is much less prone to be carried out in Europe, as a consequence of its robust regulatory frameworks.
Implementing AI in Cybersecurity
|
Upsides |
Downsides |
|---|---|
|
|
AI in Cybersecurity Examples
Do you utilize any AI cybersecurity instruments and, in that case, which of them would you advocate?
—M.D., Seattle, United States
To enrich the safety afforded by purchasers’ normal safety merchandise, I take advantage of the AironWorks phishing simulation platform, the place personalized phishing simulations are generated for organizations to examine the preparedness and safety consciousness of their workers. However presently, from a testing perspective, I don’t suppose that AI is nicely positioned to be of a lot assist in cybersecurity. Certain, all the large firms declare to have adopted AI for cybersecurity of their product choices, however the extent to which it’s usable varies.
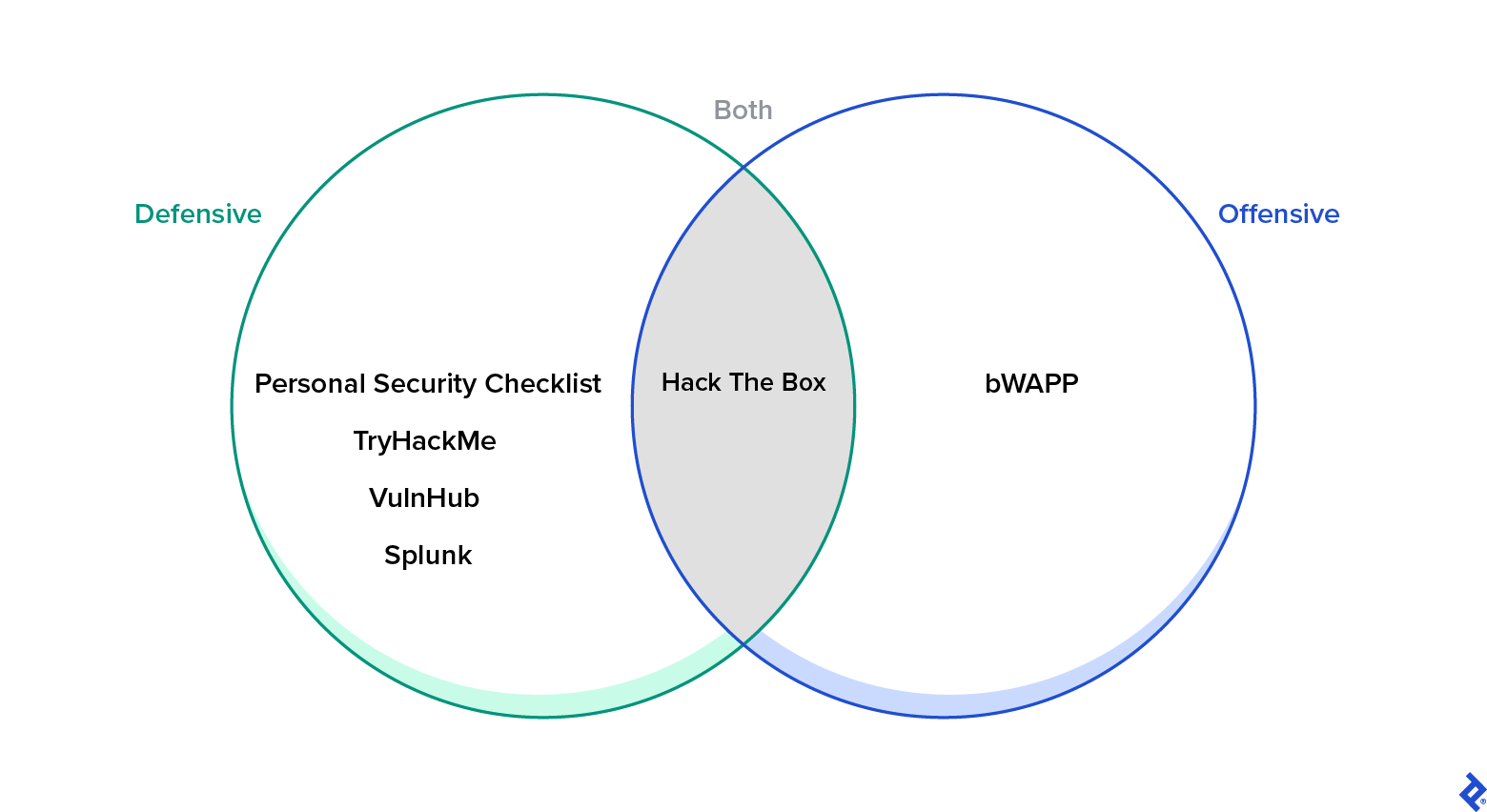
Are you able to counsel a enjoyable web site the place safety hobbyists can mess around with and uncover completely different matters of offensive or defensive safety?
—J.O., Fortaleza, Brazil
I, for one, am an enormous fan of private safety. From a defensive perspective, I at all times advocate the Private Safety Guidelines, a GitHub checklist of 300-plus suggestions for safeguarding digital safety and privateness. You should utilize TryHackMe as a solution to get began in safety, and even compete in a few of its on-line challenges. VulnHub is superior even when it’s not frequently up to date. Challenges at Splunk—which seems prepared for a refresh—come to thoughts. From an offensive perspective, bWAPP is an effective Docker container that means that you can attempt to exploit an online software for your self. And there’s additionally Hack The Field, which incorporates each defensive and offensive components.
I hear conflicting views concerning Mac safety: Some say that Mac is already safe, whereas others really feel that you would be able to’t be too cautious. What’s your opinion?
—M.Z., Santa Clarita, United States
Properly, there are considerably fewer Mac customers than PC customers, which might clarify why a majority of cyberattacks are geared toward PCs. Nevertheless, on common, Mac customers spend far extra money on their computer systems than PC customers do—so you possibly can see how Mac additionally makes for a popular goal. Judging by the various OS safety fixes launched currently, it seems to be to me—and in addition to Wired, which printed an article on this matter—as if Apple agrees that elevated Mac focusing on is an actual chance.
Would you advocate enhancing safety on Mac computer systems with antivirus instruments like Avast, or are these a waste of cash?
—M.Z., Santa Clarita, United States
You’ll be able to at all times go free with ClamAV together with maintaining your software program up to date. Additionally, Microsoft Defender is now obtainable for Mac.
The editorial crew of the Toptal Engineering Weblog extends its gratitude to Marco Jardim for reviewing the technical content material introduced on this article.
[ad_2]