[ad_1]

The LostTrust ransomware operation is believed to be a rebrand of MetaEncryptor, using virtually an identical knowledge leak websites and encryptors.
LostTrust started attacking organizations in March 2023 however didn’t develop into extensively recognized till September, after they started using an information leak website.
At the moment, the information leak website lists 53 victims worldwide, with some having their knowledge leaked already for not paying a ransom.
It’s unclear if the ransomware gang solely targets Home windows gadgets or in the event that they make the most of a Linux encryptor as properly.
A rebrand of MetaEncryptor
MetaEncryptor is a ransomware operation that’s believed to have launched in August 2022, amassing twelve victims on their knowledge leak website by means of July 2023, after which no new victims had been added to the positioning.
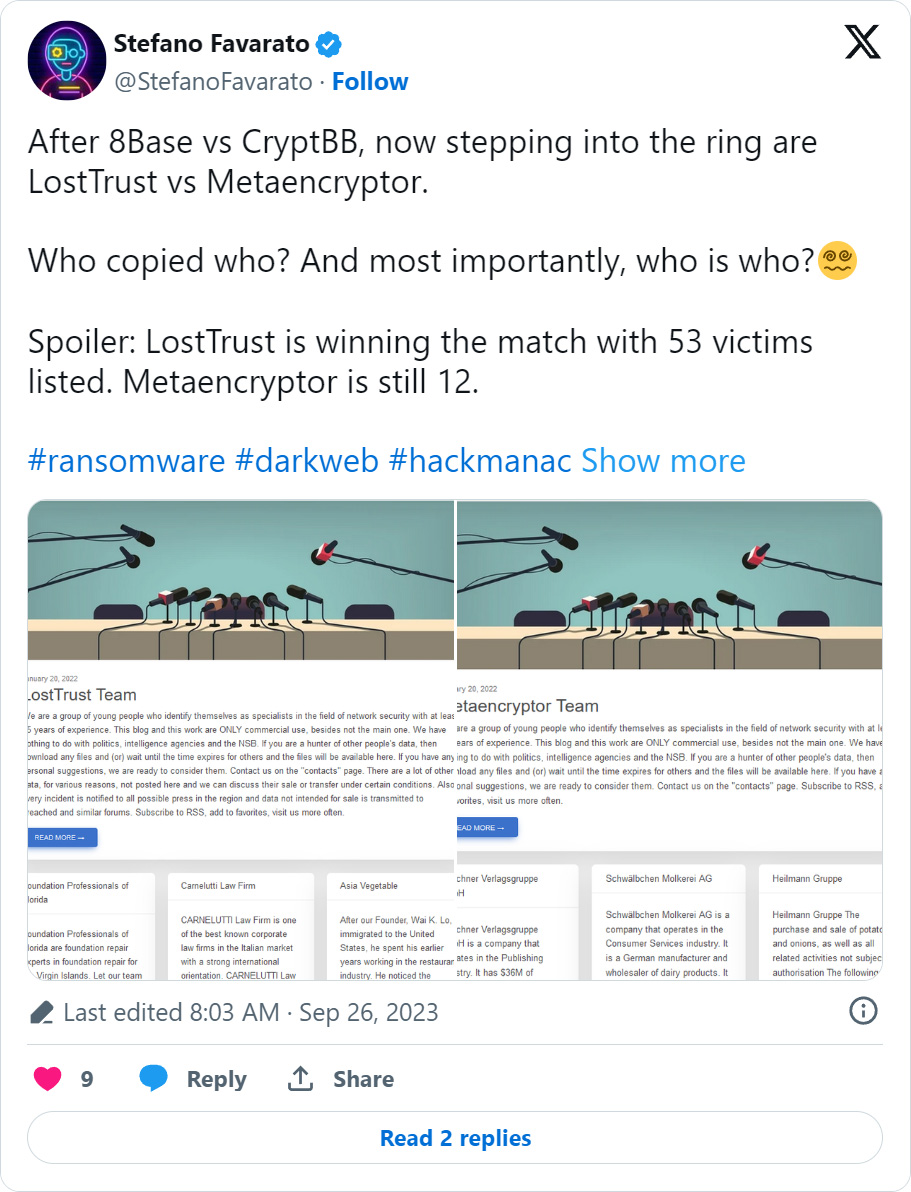
This month, a brand new knowledge leak website for the ‘LostTrust’ gang was launched, with cybersecurity researcher Stefano Favarato shortly noticing it makes use of the identical actual template and bio as MetaEncryptor’s knowledge leak website.
“We’re a bunch of younger individuals who establish themselves as specialists within the discipline of community safety with not less than 15 years of expertise,” reads an outline on each the MetaEncryptor and LostTrust knowledge leak websites.
“This weblog and this work are ONLY business use, apart from not the primary one. We now have nothing to do with politics, intelligence companies and the NSB.”
BleepingComputer additionally discovered that each the LostTrust [VirusTotal] and MetaEncryptor [VirusTotal] encryptors are just about an identical, with some minor adjustments to ransom notes, embedded public keys, ransom notice names, and encrypted file extensions.
Moreover, cybersecurity researcher MalwareHunterTeam advised BleepingComputer that LostTrust and MetaEncryptor are based mostly on the SFile2 ransomware encryptor. This relation is additional backed up by an Intezer scan exhibiting plenty of code overlap between the LostTrust and SFile encryptors.
As a result of vital overlap between the 2 operations, it’s believed that LostTrust is a rebrand of the MetaEncryptor operation.
The LostTrust encryptor
BleepingComputer discovered a pattern of the LostTrust encryptor and carried out a short evaluation beneath.
The encryptor might be launched with two non-compulsory command line arguments, –onlypath (encrypt a particular path) and –enable-shares (encrypt community shares).
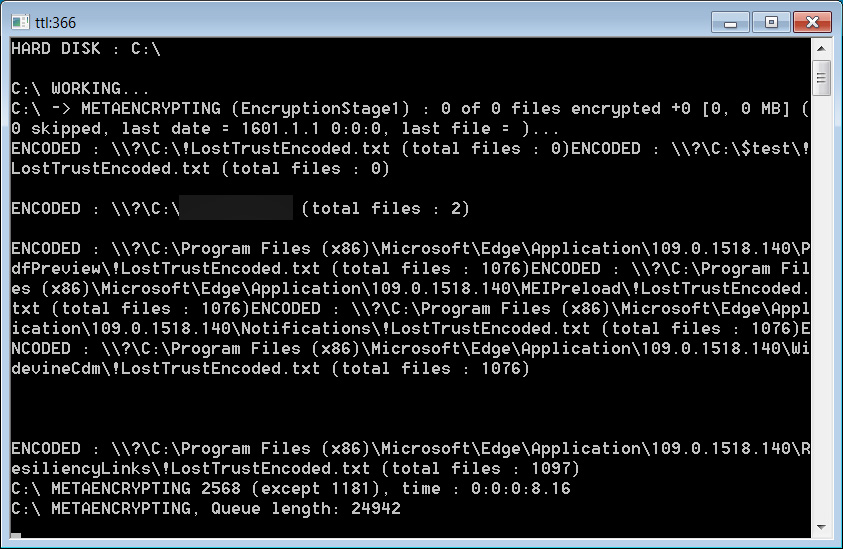
When launched, the encryptor will open a console displaying the present state of the encryption course of, as proven beneath.
Supply:BleepingComputer
Observe the ‘METAENCRYPTING‘ string within the encryptor, indicating it’s a modified MetaEncryptor encryptor.
When executed, LostTrust will disable and cease quite a few Home windows companies to make sure all recordsdata might be encrypted, together with any companies containing the Firebird, MSSQL, SQL, Alternate, wsbex, postgresql, BACKP, tomcat, SBS, and SharePoint strings.
The encryptor may also disable and cease further companies related to Microsoft Alternate.
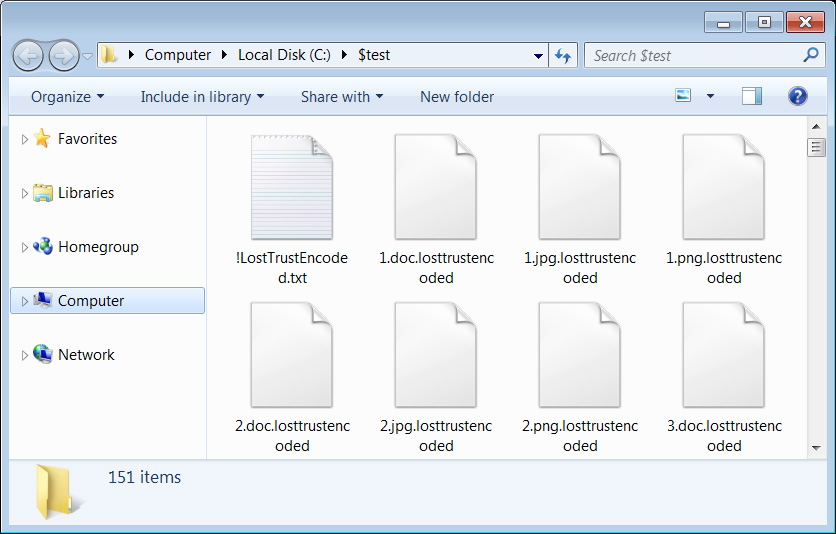
When encrypting recordsdata, the encryptor will append the .losttrustencoded extension to encrypted file’s names, as illustrated beneath.
Supply: BleepingComputer
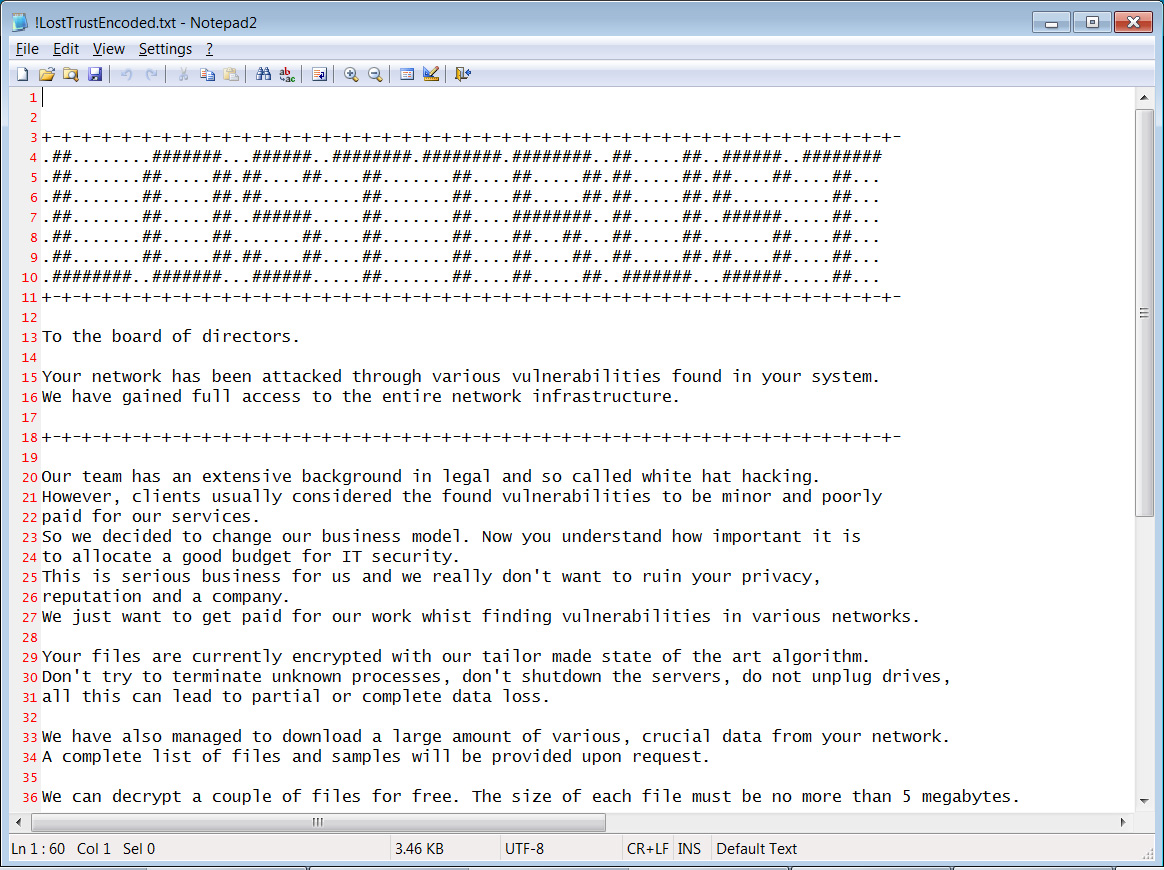
Ransom notes named !LostTrustEncoded.txt can be created in each folder on the system, with the menace actors introducing themselves as prior white hat hackers. Nevertheless, after being poorly paid, they determined to modify to cybercrime.
“Our group has an intensive background in authorized and so referred to as white hat hacking. Nevertheless, purchasers often thought-about the discovered vulnerabilities to be minor and poorly paid for our companies,” reads the LostTrust ransom notice.
“So we determined to vary our enterprise mannequin. Now you perceive how vital it’s to allocate a superb finances for IT safety.”
Supply: BleepingComputer
These ransom notes include data on what occurred to the corporate’s recordsdata and embody a novel hyperlink to the ransomware gang’s Tor negotiation website.
The negotiation website is naked bones, with solely a chat characteristic permitting firm representatives to barter with the menace actors.
Supply: BleepingComputer
BleepingComputer was advised that ransom calls for for LostTrust assaults vary from $100,000 to hundreds of thousands.
Information leak website used to extort victims
Like different ransomware operations, LostTrust makes use of a Tor knowledge breach website that’s used to extort firms by threatening to leak their stolen knowledge if a ransom will not be paid.
LostTrust has 53 victims on their knowledge leak website, with some firms already having their knowledge leaked.
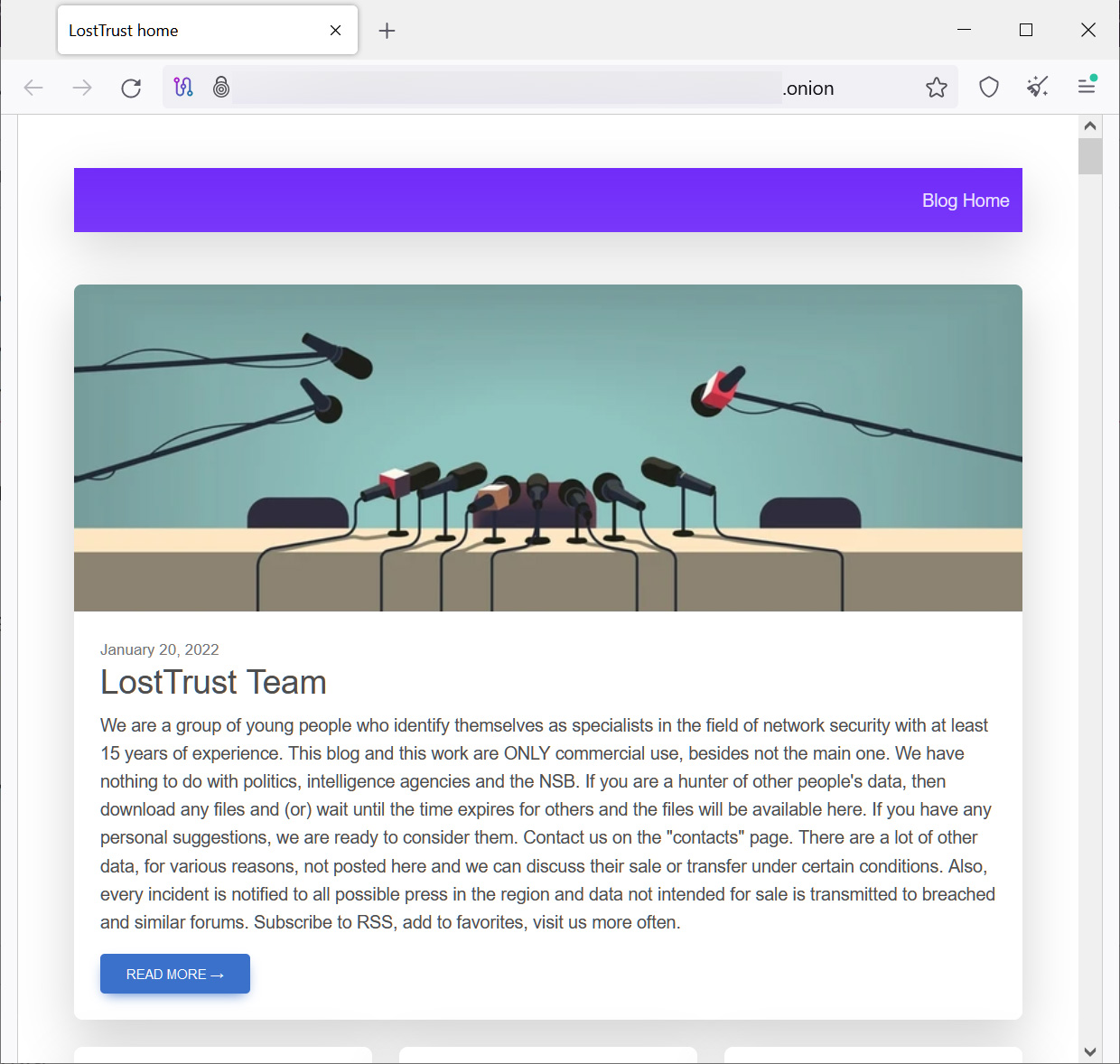
Supply: BleepingComputer
At the moment, it’s not recognized if paying a ransom demand will result in the deletion of knowledge and a working decryptor.
[ad_2]