
[ad_1]

A member of U.S. Navy’s crimson group has revealed a instrument referred to as TeamsPhisher that leverages an unresolved safety problem in Microsoft Groups to bypass restrictions for incoming recordsdata from customers exterior of a focused group, the so-called exterior tenants.
The instrument exploits a drawback highlighted final month by Max Corbridge and Tom Ellson of UK-based safety companies firm Jumpsec, who defined how an attacker may simply go round Microsoft Groups’ file-sending restraints to ship malware from an exterior account.
The feat is feasible as a result of the appliance has client-side protections that may be tricked into treating an exterior person as an inside one simply by altering the ID within the POST request of a message.
Streamlining assaults on Groups
‘TeamsPhisher’ is a Python-based instrument that gives a totally automated assault. It integrates the assault thought of Jumpsec’s researchers, methods developed by Andrea Santese, and authentication and helper features from Bastian Kanbach’s ‘TeamsEnum‘ instrument.
“Give TeamsPhisher an attachment, a message, and a listing of goal Groups customers. It should add the attachment to the sender’s Sharepoint, after which iterate by means of the checklist of targets,” reads the outline from Alex Reid, the developer of the crimson group utility.
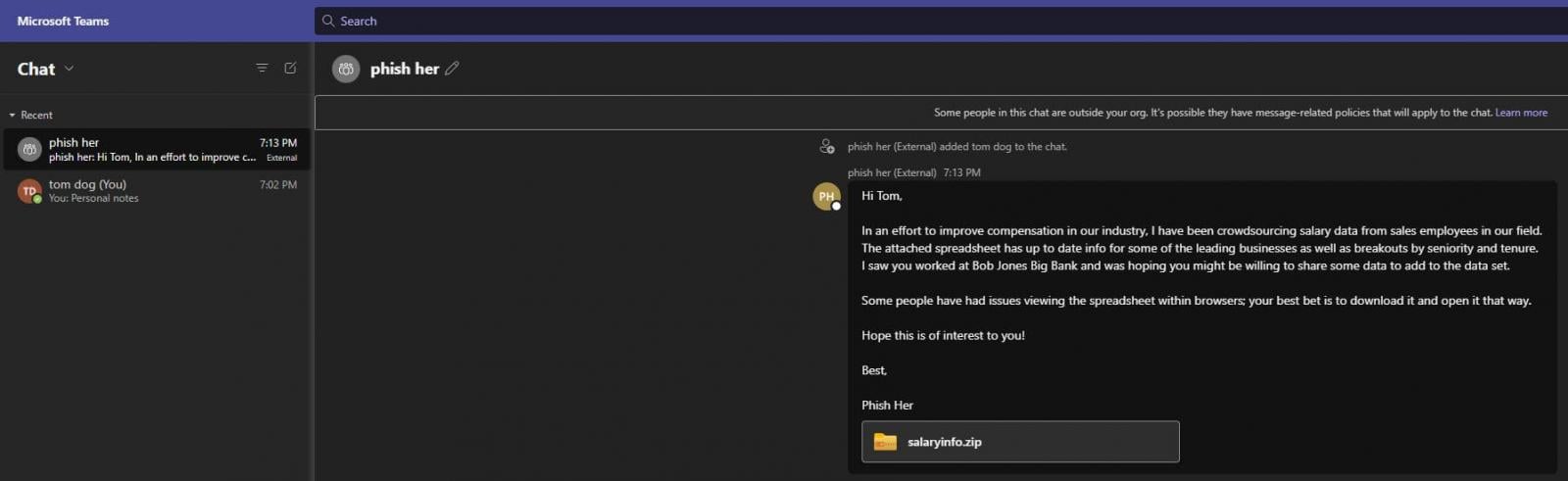
TeamsPhisher first verifies the existence of the goal person and their skill to obtain exterior messages, which is a prerequisite for the assault to work.
It then creates a brand new thread with the goal, sends them a message with a Sharepoint attachment hyperlink. The thread seems within the sender’s Groups interface for (potential) handbook interplay.
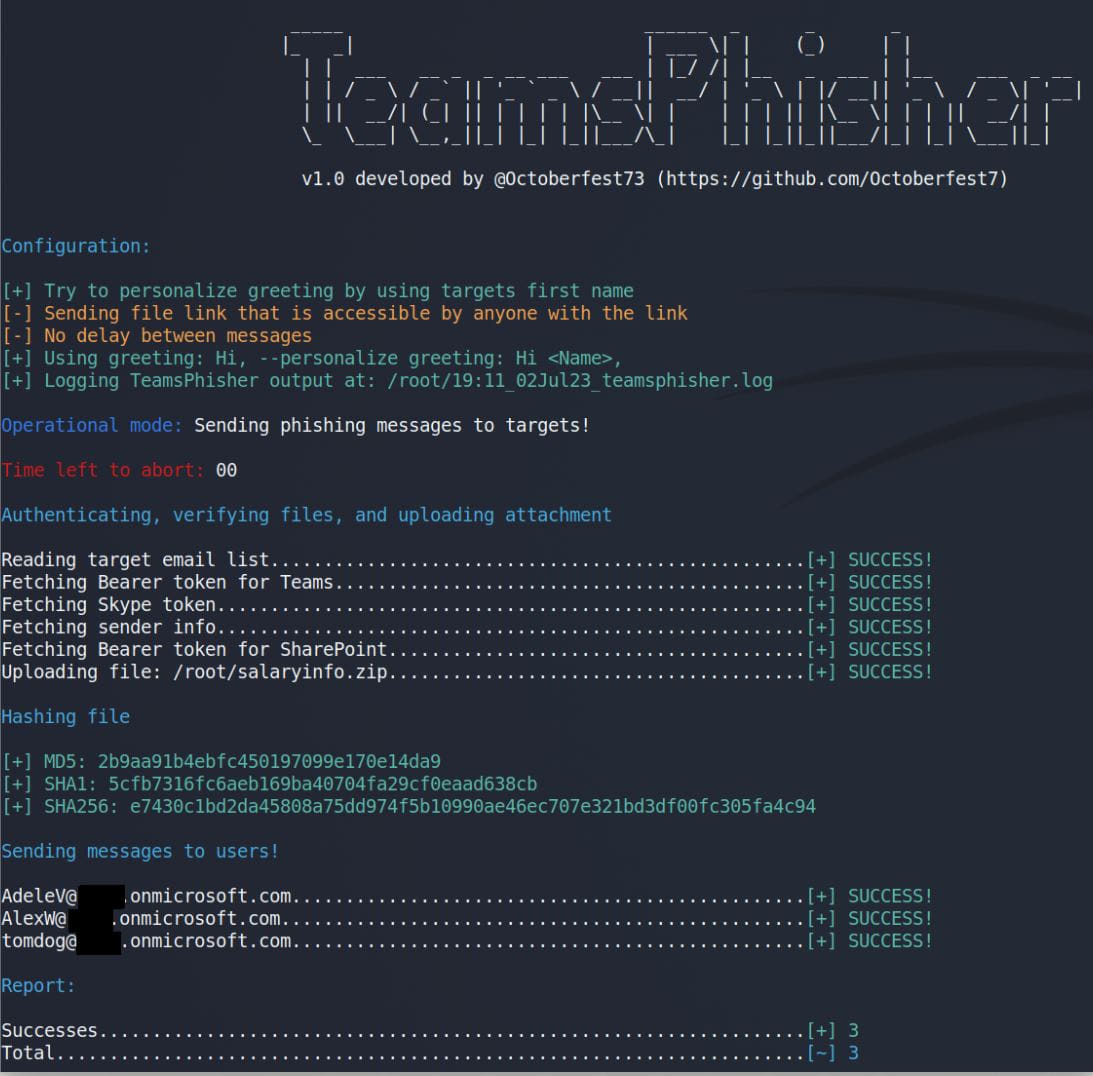
TeamsPhisher requires customers to have a Microsoft Enterprise account (MFA is supported) with a legitimate Groups and Sharepoint license, which is frequent for a lot of main firms.
The instrument additionally presents a “preview mode” to assist customers confirm the set goal lists and to verify the looks of messages from the recipient’s perspective.
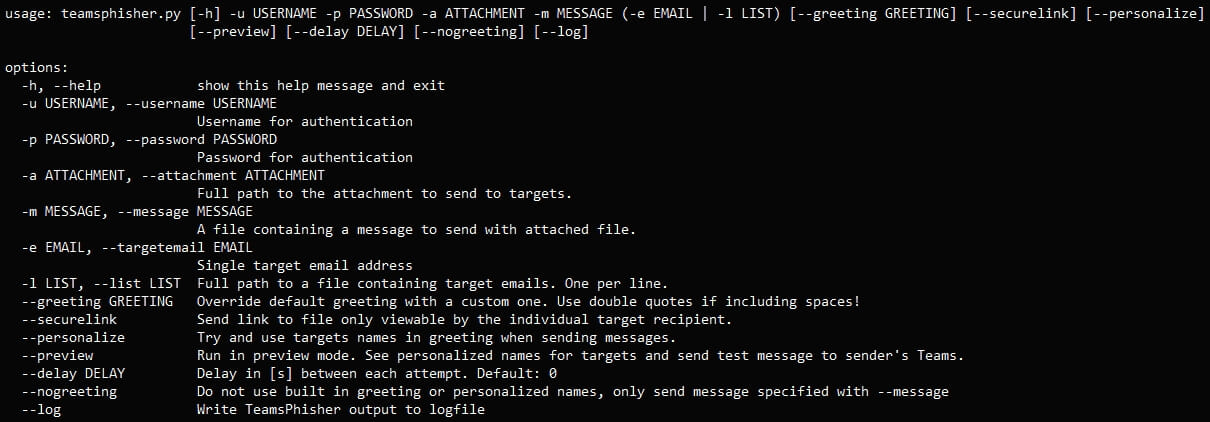
Different options and optionally available arguments in TeamsPhisher may refine the assault. These embody sending safe file hyperlinks that may solely be considered by the meant recipient, specifying a delay between message transmissions to bypass price limiting, and writing outputs to a log file.
Unsolved drawback
The difficulty that TeamsPhisher exploits continues to be current and Microsoft instructed Jumpsec researchers that it didn’t meet the bar for rapid servicing.
BleepingComputer additionally reached out to the corporate final month for a remark about plans to repair the issue however didn’t obtain a response. We reiterated our request for remark from Microsoft however didn’t obtain a reply at publishing time.
Though TeamPhisher was created for licensed crimson group operations, menace actors can even leverage it to ship malware to focus on organizations with out setting off alarms.
Till Microsoft decides to take motion about this, organizations are strongly suggested to disable communications with exterior tenants if not wanted. They will additionally create an allow-list with trusted domains, which might restrict the danger of exploitation.
[ad_2]