[ad_1]
An lively malware marketing campaign concentrating on Latin America is shelling out a brand new variant of a banking trojan known as BBTok, significantly customers in Brazil and Mexico.
“The BBTok banker has a devoted performance that replicates the interfaces of greater than 40 Mexican and Brazilian banks, and methods the victims into coming into its 2FA code to their financial institution accounts or into coming into their cost card quantity,” Examine Level stated in analysis revealed this week.
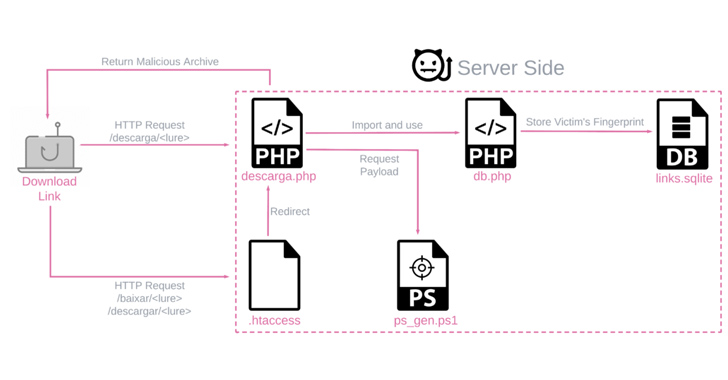
The payloads are generated by a customized server-side PowerShell script and are distinctive for every sufferer based mostly on the working system and nation, whereas being delivered by way of phishing emails that leverage quite a lot of file sorts.
BBTok is a Home windows-based banking malware that first surfaced in 2020. It is outfitted with options that run the standard trojan gamut, permitting it to enumerate and kill processes, problem distant instructions, manipulate keyboard, and serve pretend login pages for banks working within the two nations.
The assault chains themselves are pretty simple, using bogus hyperlinks or ZIP file attachments to stealthily deploy the banker retrieved from a distant server (216.250.251[.]196) whereas displaying a decoy doc to the sufferer.

However they’re additionally diversified for each Home windows 7 and Home windows 10 methods, primarily taking steps to evade newly applied detection mechanisms similar to Antimalware Scan Interface (AMSI) that permits for scanning the machine for any threats.
Two different key strategies to fly underneath the radar are using living-off-the-land binaries (LOLBins) and geofencing checks to make sure that the targets are solely from Brazil or Mexico earlier than serving the malware by way of the PowerShell script.
As soon as launched, BBTok establishes connections with a distant server to obtain instructions to simulate the safety verification pages for numerous banks.
In impersonating the interfaces of Latin American banks, the purpose is to reap credential and authentication info entered by the customers to conduct account takeovers of the web financial institution accounts.
“What’s notable is the operator’s cautious method: all banking actions are solely executed upon direct command from its C2 server, and are usually not mechanically carried out on each contaminated system,” the corporate stated.
Examine Level’s evaluation of the malware has revealed a major enchancment to its obfuscation and concentrating on since 2020, increasing past Mexican banks. The presence of Spanish and Portuguese language within the supply code in addition to in phishing emails presents a touch as to the attackers’ origin.
Greater than 150 customers are estimated to have been contaminated by BBTok, based mostly on an SQLite database discovered within the server internet hosting the payload technology part that data entry to the malicious utility.
The concentrating on and the language factors to the risk actors doubtless working out of Brazil, which continues to be the epicenter of potent financially-focused malware.
AI vs. AI: Harnessing AI Defenses Towards AI-Powered Dangers
Able to sort out new AI-driven cybersecurity challenges? Be a part of our insightful webinar with Zscaler to deal with the rising risk of generative AI in cybersecurity.
“Though BBTok has been capable of stay underneath the radar as a consequence of its elusive strategies and concentrating on victims solely in Mexico and Brazil, it is evident that it’s nonetheless actively deployed,” Examine Level stated.
“Resulting from its many capabilities, and its distinctive and artistic supply technique involving LNK information, SMB and MSBuild, it nonetheless poses a hazard to organizations and people within the area.”
The event comes because the Israeli cybersecurity firm detailed a brand new large-scale phishing marketing campaign that just lately focused over 40 distinguished corporations throughout a number of industries in Colombia with an final goal to deploy the Remcos RAT by way of a multi-stage an infection sequence.
“Remcos, a complicated ‘Swiss Military Knife’ RAT, grants attackers full management over the contaminated pc and can be utilized in quite a lot of assaults. Widespread penalties of a Remcos an infection embrace information theft, follow-up infections, and account takeover,” Examine Level stated.
[ad_2]