
[ad_1]

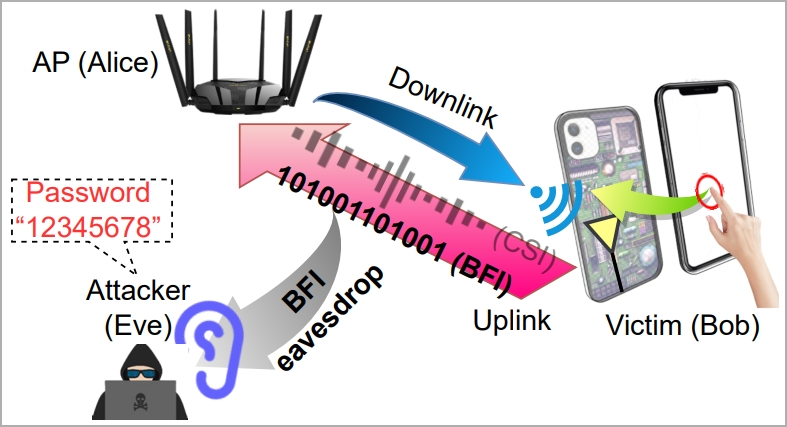
A brand new assault dubbed ‘WiKI-Eve’ can intercept the cleartext transmissions of smartphones related to trendy WiFi routers and deduce particular person numeric keystrokes at an accuracy charge of as much as 90%, permitting numerical passwords to be stolen.
WiKI-Eve exploits BFI (beamforming suggestions data), a function launched in 2013 with WiFi 5 (802.11ac), which permits units to ship suggestions about their place to routers so the latter can direct their sign extra precisely.
The issue with BFI is that the knowledge change comprises knowledge in cleartext kind, that means that this knowledge might be intercepted and readily used with out requiring {hardware} hacking or cracking an encryption key.
This safety hole was found by a crew of college researchers in China and Singapore, who examined the retrieval of potential secrets and techniques from these transmissions.
The crew discovered that it is moderately simple to establish numeric keystrokes 90% of the time, decipher 6-digit numerical passwords with an accuracy of 85%, and work out advanced app passwords at an accuracy of roughly 66%.
Whereas this assault solely works on numerical passwords, a research by NordPass confirmed that 16 out of 20 of the highest passwords solely used digits.
The WiKI-Eve assault
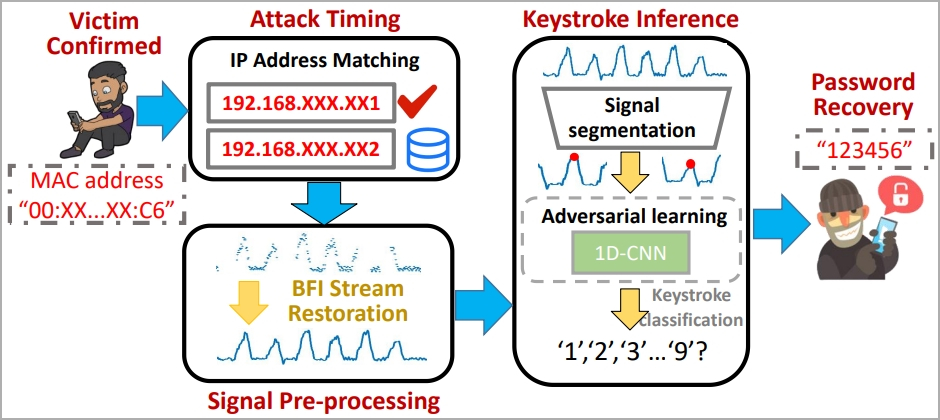
The WiKI-Eve assault is designed to intercept WiFi alerts throughout password entry, so it is a real-time assault that should be carried out whereas the goal actively makes use of their smartphone and makes an attempt to entry a particular utility.
.jpg)
The attacker should establish the goal utilizing an id indicator on the community, like a MAC handle, so some preparatory work is required.
“In actuality, Eve can purchase this data beforehand by conducting visible and visitors monitoring concurrently: correlating community visitors originating from numerous MAC addresses with customers’ behaviors ought to permit Eve to hyperlink Bob’s bodily machine to his digital visitors, thereby figuring out Bob’s MAC handle,” explains the researchers.
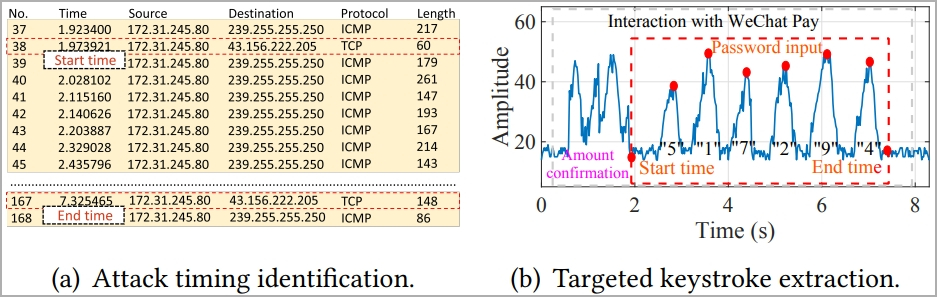
In the principle part of the assault, the sufferer’s BFI time sequence throughout password entry is captured by the attacker utilizing a visitors monitoring device like Wireshark.
Every time the person presses a key, it impacts the WiFi antennas behind the display, inflicting a definite WiFi sign to be generated.
“Although they solely account for a part of the downlink CSIs regarding the AP facet, the truth that on-screen typing straight impacts the Wi-Fi antennas (therefore channels) proper behind the display (see Determine 1) permits BFIs to include adequate details about keystrokes,” reads the paper.
Nonetheless, the paper emphasizes that the recorded BFI sequence would possibly blur boundaries between keystrokes, in order that they developed an algorithm for parsing and restoring usable knowledge.
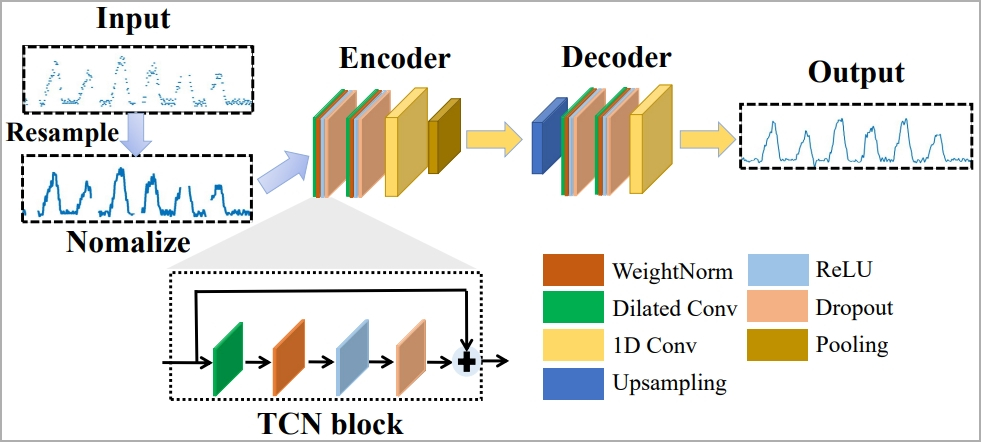
To deal with the problem of filtering out components that intrude with the outcomes, like typing type, typing velocity, adjoining keystrokes, and many others. the researchers use machine studying known as “1-D Convolutional Neural Community.”
The system is educated to constantly acknowledge keystrokes no matter typing types via the idea of “area adaptation,” which includes a function extractor, a keystroke classifier, and a site discriminator.
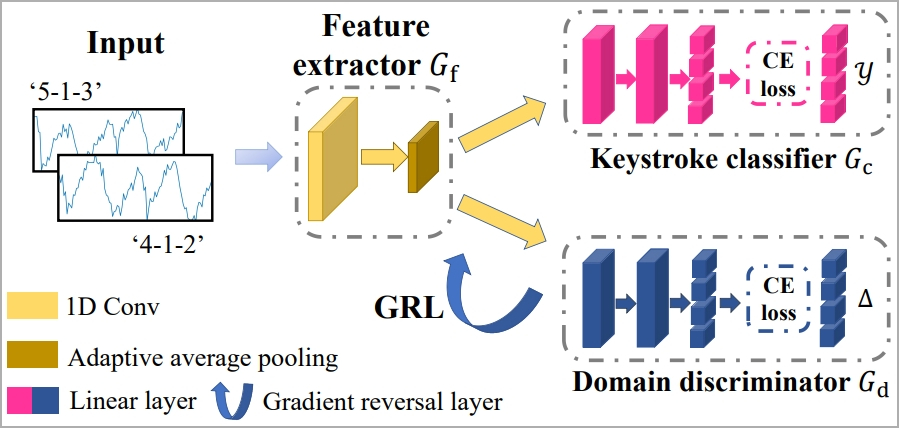
Lastly, a “Gradient Reversal Layer” (GRL) is utilized to suppress domain-specific options, serving to the mannequin be taught constant keystroke representations throughout domains.
Assault outcomes
The researchers experimented with WiKI-Eve utilizing a laptop computer and WireShark but in addition identified {that a} smartphone may also be used as an attacking machine, though it is likely to be extra restricted within the variety of supported WiFi protocols.
The captured knowledge was analyzed utilizing Matlab and Python, and the segmentation parameters had been set to values proven to provide the perfect outcomes.
Twenty individuals related to the identical WiFi entry level used completely different telephone fashions. They typed numerous passwords utilizing a mixture of energetic background apps and ranging typing speeds whereas measurements had been taken from six completely different areas.
The experiments confirmed that WiKI-Eve’s keystroke classification accuracy stays secure at 88.9% when sparse restoration algorithm and area adaptation are used.
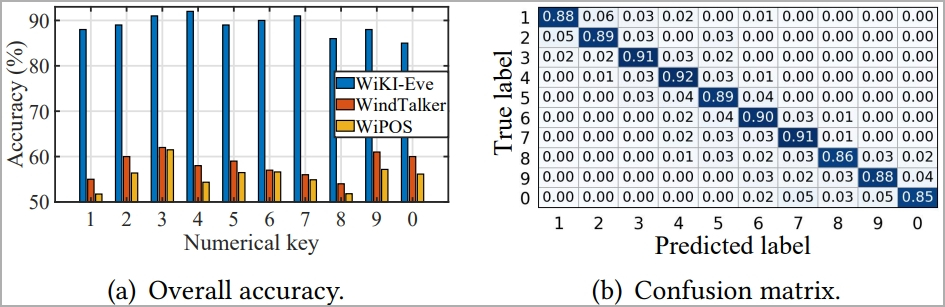
For six-digit numerical passwords, WiKI-Eve may infer them with an 85% success charge in underneath 100 makes an attempt, remaining constantly above 75% in all examined environments.
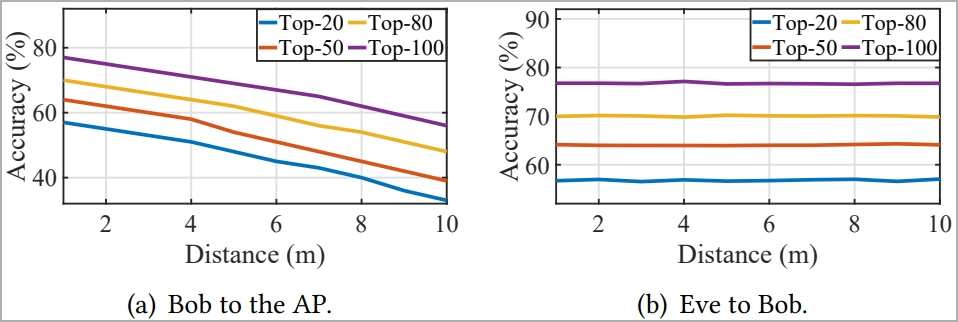
Nonetheless, the gap between the attacker and the entry level is essential to this efficiency. Rising that distance from 1m to 10m resulted in a 23% profitable guess charge drop.
The researchers additionally experimented with retrieving person passwords for WeChat Pay, emulating a practical assault state of affairs, and located that WiKI-Eve deduced the passwords accurately at a charge of 65.8%.
The mannequin constantly predicted the right password inside its prime 5 guesses in over 50% of the 50 checks performed. This implies an attacker has a 50% likelihood of gaining entry earlier than hitting the safety threshold of 5 incorrect password makes an attempt, after which the app locks.
In conclusion, the paper exhibits that adversaries can deduce secrets and techniques with out hacking entry factors and by merely utilizing community visitors monitoring instruments and machine studying frameworks.
This requires heightened safety in WiFi entry factors and smartphone apps, like probably keyboard randomization, encryption of information visitors, sign obfuscation, CSI scrambling, WiFi channel scrambling, and extra.
[ad_2]