
[ad_1]

Hackers are using a brand new trick of utilizing zero-point fonts in emails to make malicious emails seem as safely scanned by safety instruments in Microsoft Outlook.
Though the ZeroFont phishing approach has been used prior to now, that is the primary time it has been documented as used on this method.
In a brand new report by ISC Sans analyst Jan Kopriva, the researcher warns that this trick might make an enormous distinction within the effectiveness of phishing operations, and customers ought to pay attention to its existence and use within the wild.
ZeroFont assaults
The ZeroFont assault technique, first documented by Avanan in 2018, is a phishing approach that exploits flaws in how AI and pure language processing (NLP) methods in e-mail safety platforms analyze textual content.
It entails inserting hidden phrases or characters in emails by setting the font dimension to zero, rendering the textual content invisible to human targets, but holding it readable by NLP algorithms.
This assault goals to evade safety filters by inserting invisible benign phrases that blend with suspicious seen content material, skewing AI’s interpretation of the content material and the results of safety checks.
In its 2018 report, Avanan warned that ZeroFont bypassed Microsoft’s Workplace 365 Superior Menace Safety (ATP) even when the emails contained recognized malicious key phrases.
Hiding bogus antivirus scans
In a brand new phishing e-mail seen by Kopriva, a risk actor makes use of the ZeroFont assault to control message previews on broadly used e-mail purchasers corresponding to Microsoft Outlook.
Particularly, the e-mail in query displayed a distinct message in Outlook’s e-mail checklist than within the preview pane.
As you may see under, the e-mail itemizing pane reads “Scanned and secured by Isc®Superior Menace safety (APT): 9/22/2023T6:42 AM,” whereas the start of the e-mail within the preview/studying pane shows “Job Provide | Employment Alternative.”
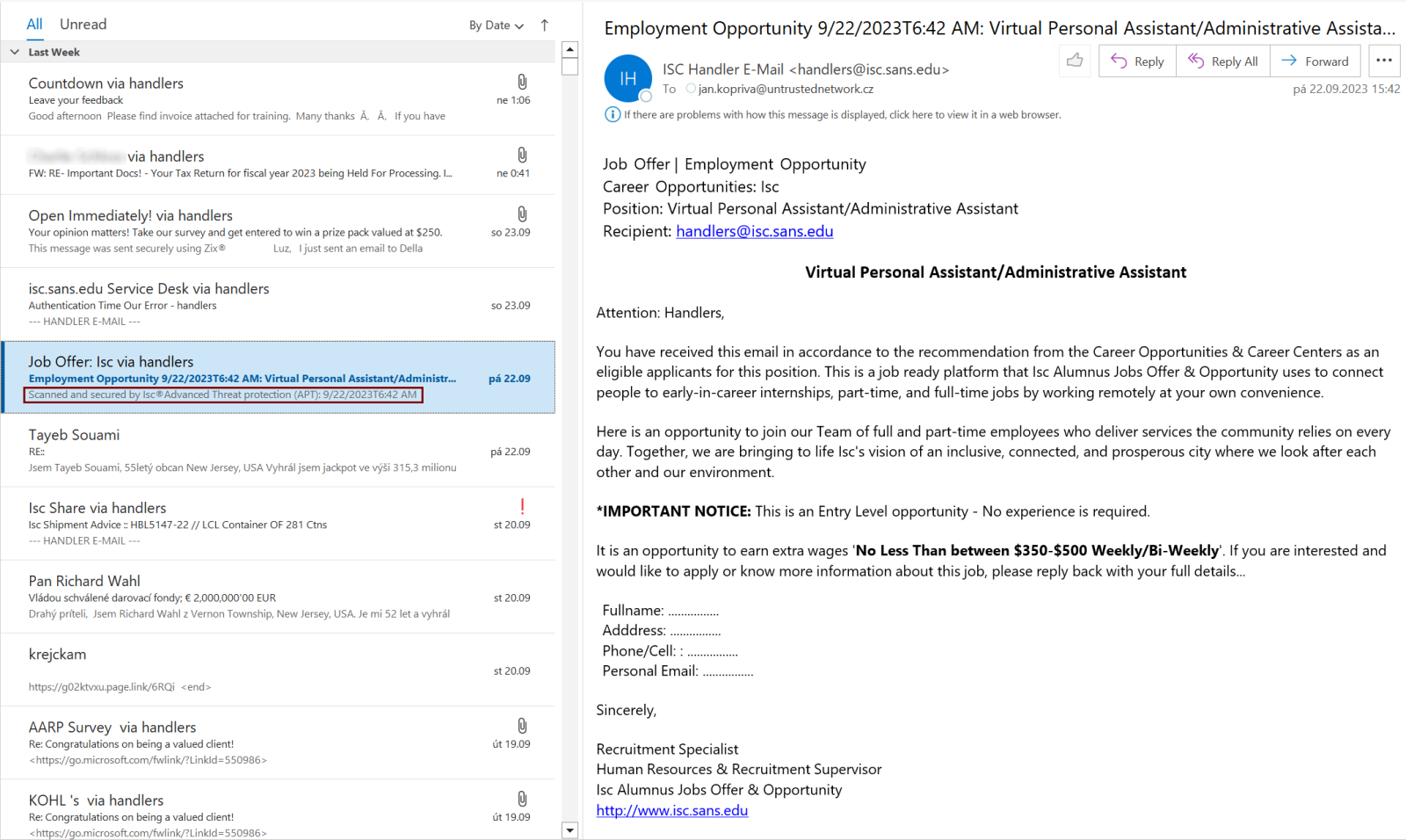
This discrepancy is achieved by leveraging ZeroFont to cover the bogus safety scan message at first of the phishing e-mail, so whereas it is not seen to the recipient, Outlook nonetheless grabs it and shows it as a preview on the e-mail itemizing pane.
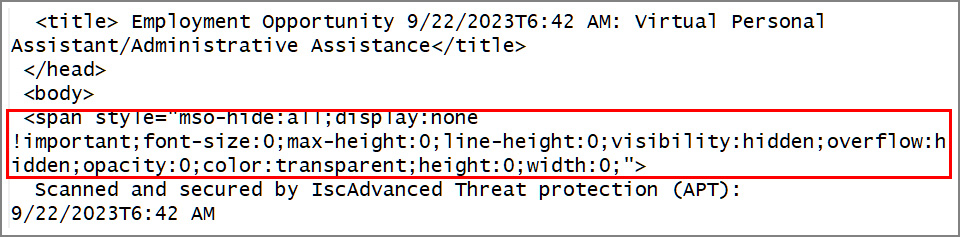
Supply: ISC Sans
The purpose is to instill a false sense of legitimacy and safety within the recipient.
By presenting a misleading safety scan message, the probability of the goal opening the message and fascinating with its content material rises.
It’s attainable that Outlook is not the one e-mail consumer that grabs the primary portion of an e-mail to preview a message with out checking if its font dimension is legitimate, so vigilance is suggested for customers of different software program, too.
[ad_2]