
[ad_1]

Getty Pictures
Firewalls made by Zyxel are being wrangled right into a damaging botnet, which is taking management of them by exploiting a not too long ago patched vulnerability with a severity score of 9.8 out of a attainable 10.
“At this stage when you’ve got a susceptible system uncovered, assume compromise,” officers from Shadowserver, a company that displays Web threats in actual time, warned 4 days in the past. The officers mentioned the exploits are coming from a botnet that’s much like Mirai, which harnesses the collective bandwidth of hundreds of compromised Web units to knock websites offline with distributed denial-of-service assaults.
In line with knowledge from Shadowserver collected over the previous 10 days, 25 of the highest 62 Web-connected units waging “downstream assaults”—that means trying to hack different Web-connected units—had been made by Zyxel as measured by IP addresses.
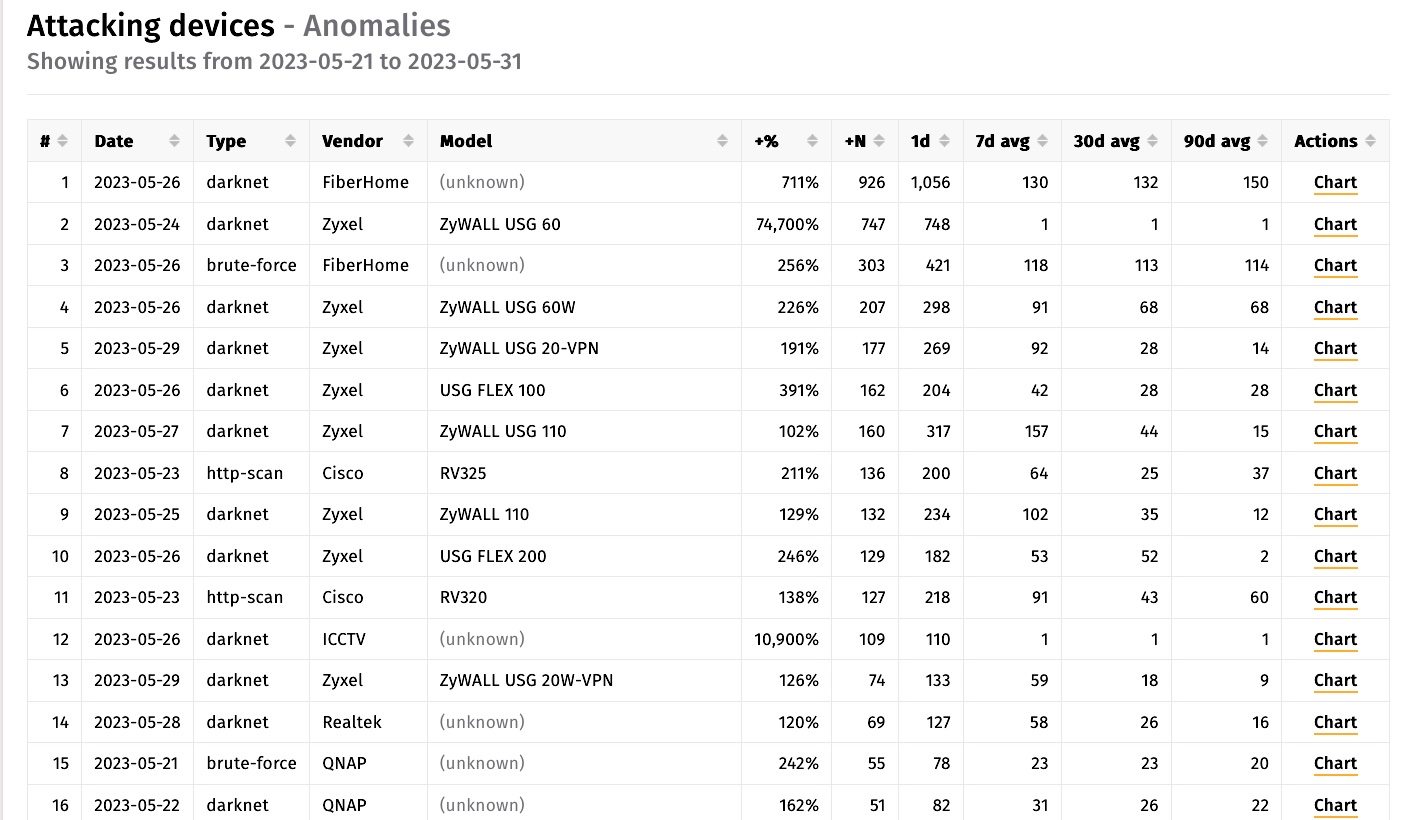
A 9.8-severity vulnerability in default configurations
The software program bug used to compromise the Zyxel units is tracked as CVE-2023-28771, an unauthenticated command injection vulnerability with a severity charge of 9.8. The flaw, which Zyxel patched on April 25, could be exploited to execute malicious code with a specifically crafted IKEv2 packet to UDP port 500 on the system.
The essential vulnerability exists in default configurations of the producer’s firewall and VPN units. They embrace Zyxel ZyWALL/USG sequence firmware variations 4.60 by means of 4.73, VPN sequence firmware variations 4.60 by means of 5.35, USG FLEX sequence firmware variations 4.60 by means of 5.35, and ATP sequence firmware variations 4.60 by means of 5.35.
| Affected sequence | Affected model | Patch availability |
|---|---|---|
| ATP | ZLD V4.60 to V5.35 | ZLD V5.36 |
| USG FLEX | ZLD V4.60 to V5.35 | ZLD V5.36 |
| VPN | ZLD V4.60 to V5.35 | ZLD V5.36 |
| ZyWALL/USG | ZLD V4.60 to V4.73 | ZLD V4.73 Patch 1 |
On Wednesday, the Cybersecurity and Infrastructure Safety Company positioned CVE-2023-28771 on its listing of recognized exploited vulnerabilities. The company has given federal companies till June 21 to repair any susceptible units of their networks.
Safety researcher Kevin Beaumont has additionally been warning of widespread exploitation of the vulnerability since final week.
“This #Zyxel vuln is being mass exploited now by Mirai botnet,” he wrote on Mastodon. “A fuck ton of SMB VPN packing containers are owned.”
Measurements from the Shodan search engine present virtually 43,000 situations of Zyxel units uncovered to the Web.
“This quantity solely contains units that expose their net interfaces on the WAN, which isn’t a default setting,” Rapid7 mentioned, utilizing the abbreviation for vast space community, the a part of an organization’s community that may be accessed over the Web. “For the reason that vulnerability is within the VPN service, which is enabled by default on the WAN, we count on the precise variety of uncovered and susceptible units to be a lot increased.”
A VPN—quick for digital non-public community—would not have to be configured on a tool for it to be susceptible, Rapid7 mentioned. Zyxel units have lengthy been a favourite for hacking as a result of they reside on the fringe of a community, the place defenses are usually decrease. As soon as contaminated, attackers use the units as a launch pad for compromising different units on the Web or as a toe-hold that can be utilized to unfold to different components of the community they belong to.
Whereas a lot of the focus is on CVE-2023-28771, Rapid7 warned of two different vulnerabilities—CVE-2023-33009 and CVE-2023-33010 — that Zyxel patched final week. Each vulnerabilities additionally carry a 9.8 severity score.
With infections from CVE-2023-28771 nonetheless occurring 5 weeks after Zyxel fastened it, it’s clear many system homeowners aren’t putting in safety updates in a well timed method. If the poor patching hygiene carries over to the extra not too long ago fastened vulnerabilities, there seemingly can be extra Zyxel compromises occurring quickly.
[ad_2]