[ad_1]
Risk actors are exploiting poorly secured Microsoft SQL (MS SQL) servers to ship Cobalt Strike and a ransomware pressure known as FreeWorld.
Cybersecurity agency Securonix, which has dubbed the marketing campaign DB#JAMMER, mentioned it stands out for the best way the toolset and infrastructure is employed.
“A few of these instruments embrace enumeration software program, RAT payloads, exploitation and credential stealing software program, and eventually ransomware payloads,” safety researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned in a technical breakdown of the exercise.
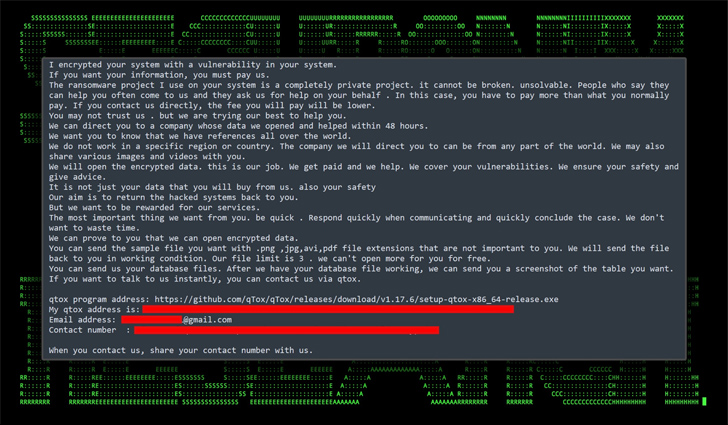
“The ransomware payload of alternative seems to be a more recent variant of Mimic ransomware known as FreeWorld.”
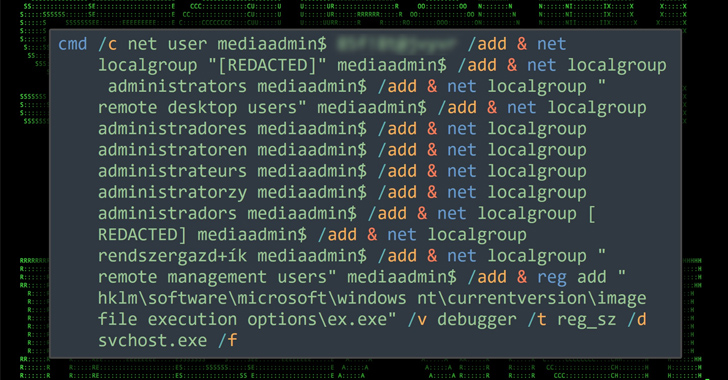
Preliminary entry to the sufferer host is achieved by brute-forcing the MS SQL server, utilizing it to enumerate the database and leveraging the xp_cmdshell configuration possibility to run shell instructions and conduct reconnaissance.

The following stage entails taking steps to impair system firewall and set up persistence by connecting to a distant SMB share to switch information to and from the sufferer system in addition to set up malicious instruments resembling Cobalt Strike.
This, in flip, paves the best way for the distribution of AnyDesk software program to in the end push FreeWorld ransomware, however not earlier than finishing up a lateral motion step. The unknown attackers are additionally mentioned to have unsuccessfully tried to ascertain RDP persistence by way of Ngrok.
“The assault initially succeeded on account of a brute drive assault towards a MS SQL server,” the researchers mentioned. “It is necessary to emphasise the significance of sturdy passwords, particularly on publicly uncovered companies.”
The disclosure comes because the operators of the Rhysida ransomware have claimed 41 victims, with greater than half of them situated in Europe.
Rhysida is among the nascent ransomware strains that emerged in Could 2023, adopting the more and more standard tactic of encrypting and exfiltrating delicate information from organizations and threatening to leak the data if the victims refuse to pay.
It additionally follows the discharge of a free decryptor for a ransomware known as Key Group owing to a number of cryptographic errors in this system. The Python script, nonetheless, solely works on samples compiled after August 3, 2023.
“Key Group ransomware makes use of a base64 encoded static key N0dQM0I1JCM= to encrypt victims’ information,” Dutch cybersecurity firm EclecticIQ mentioned in a report launched Thursday.
“The risk actor tried to extend the randomness of the encrypted information through the use of a cryptographic method known as salting. The salt was static and used for each encryption course of which poses a big flaw within the encryption routine.”
Detect, Reply, Defend: ITDR and SSPM for Full SaaS Safety
Uncover how Identification Risk Detection & Response (ITDR) identifies and mitigates threats with the assistance of SSPM. Discover ways to safe your company SaaS purposes and shield your information, even after a breach.
2023 has witnessed a report surge in ransomware assaults following a lull in 2022, at the same time as the proportion of incidents that resulted within the sufferer paying have fallen to a report low of 34%, based on statistics shared by Coveware in July 2023.
The common ransom quantity paid, however, has hit $740,144, up 126% from Q1 2023.
The fluctuations in monetization charges have been accompanied by ransomware risk actors persevering with to evolve their extortion tradecraft, together with sharing particulars of its assault methods to indicate why its victims aren’t eligible for a cyber insurance coverage payout.
“Snatch claims they may launch particulars of how assaults towards non-paying victims succeeded within the hope that insurers will determine that the incidents shouldn’t be lined by insurance coverage ransomware,” Emsisoft safety researcher Brett Callow mentioned in a publish shared on X (previously Twitter) final month.
[ad_2]