[ad_1]
An ongoing marketing campaign focusing on ministries of international affairs of NATO-aligned international locations factors to the involvement of Russian menace actors.
The phishing assaults characteristic PDF paperwork with diplomatic lures, a few of that are disguised as coming from Germany, to ship a variant of a malware known as Duke, which has been attributed to APT29 (aka BlueBravo, Cloaked Ursa, Cozy Bear, Iron Hemlock, Midnight Blizzard, and The Dukes).
“The menace actor used Zulip – an open-source chat software – for command-and-control, to evade and conceal its actions behind official internet site visitors,” Dutch cybersecurity firm EclecticIQ mentioned in an evaluation final week.
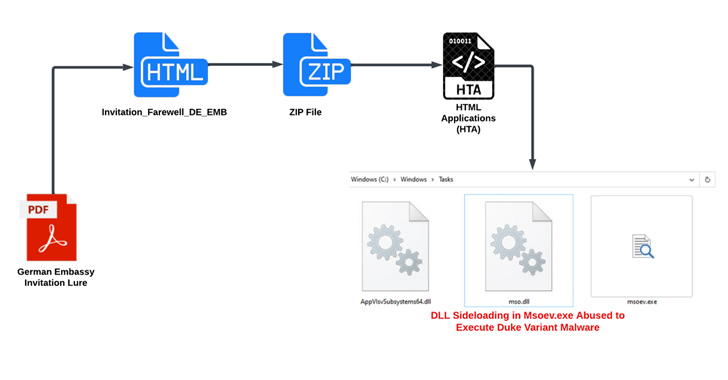
The an infection sequence is as follows: The PDF attachment, named “Farewell to Ambassador of Germany,” comes embedded with JavaScript code that initiates a multi-stage course of to drop the malware.
APT29’s use of invitation themes has been beforehand reported by Lab52, which documented an assault that impersonates the Norwegian embassy to ship a DLL payload that is able to contacting a distant server to fetch extra payloads.

Using the area “bahamas.gov[.]bs” in each the intrusion units additional solidifies this hyperlink.
Ought to a possible goal succumb to the phishing lure by opening the PDF file, a malicious HTML dropper known as Invitation_Farewell_DE_EMB is launched to execute JavaScript that drops a ZIP archive file, which, in flip, packs in an HTML Utility (HTA) file designed to deploy the Duke malware.
Command-and-control is facilitated by making use of Zulip’s API to ship sufferer particulars to an actor-controlled chat room (toyy.zulipchat[.]com) in addition to to remotely commandeer the compromised hosts.
EclecticIQ mentioned it recognized a second PDF file, seemingly utilized by APT29 for reconnaissance or for testing functions.
“It didn’t comprise a payload, however notified the actor if a sufferer opened the e-mail attachment by receiving a notification by means of a compromised area edenparkweddings[.]com,” the researchers mentioned.
It is price noting that the abuse of Zulip is par for the course with the state-sponsored group, which has a monitor document of leveraging a wide selection of official web companies comparable to Google Drive, Microsoft OneDrive, Dropbox, Notion, Firebase, and Trello for C2.
APT29’s major targets are governments and authorities subcontractors, political organizations, analysis companies, and demanding industries within the U.S. and Europe. However in an fascinating twist, an unknown adversary has been noticed using its techniques to breach Chinese language-speaking customers with Cobalt Strike.
The event comes because the Laptop Emergency Response Staff of Ukraine (CERT-UA) warned of a brand new set of phishing assaults towards state organizations of Ukraine utilizing a Go-based open-source post-exploitation toolkit known as Merlin. The exercise is being tracked below the moniker UAC-0154.

The war-torn nation has additionally confronted sustained cyber assaults from Sandworm, an elite hacking unit affiliated to Russian navy intelligence, primarily meant to disrupt vital operations and collect intelligence to achieve a strategic benefit.
In response to a current report from the Safety Service of Ukraine (SBU), the menace actor is alleged to have unsuccessfully tried to achieve unauthorized entry to Android tablets possessed by Ukrainian navy personnel for planning and performing fight missions.
“The seize of gadgets on the battlefield, their detailed examination, and the usage of accessible entry, and software program grew to become the first vector for the preliminary entry and malware distribution,” the safety company mentioned.
Among the malware strains embrace NETD to make sure persistence, DROPBEAR to ascertain distant entry, STL to collect knowledge from the Starlink satellite tv for pc system, DEBLIND to exfiltrate knowledge, the Mirai botnet malware. Additionally used within the assaults is a TOR hidden service to entry the system on the native community through the Web.
[ad_2]