
[ad_1]

A beforehand unknown risk actor dubbed ‘Sandman’ targets telecommunication service suppliers within the Center East, Western Europe, and South Asia, utilizing a modular info-stealing malware named ‘LuaDream.’
This malicious exercise was found by SentinelLabs in collaboration with QGroup GmbH in August 2023, who named the risk actor and malware after the backdoor’s inner title of ‘DreamLand shopper.’
The operational model of Sandman is to maintain a low profile to evade detection whereas performing lateral motion and sustaining long-term entry to breached programs to maximise its cyberespionage operations.
A preferred goal
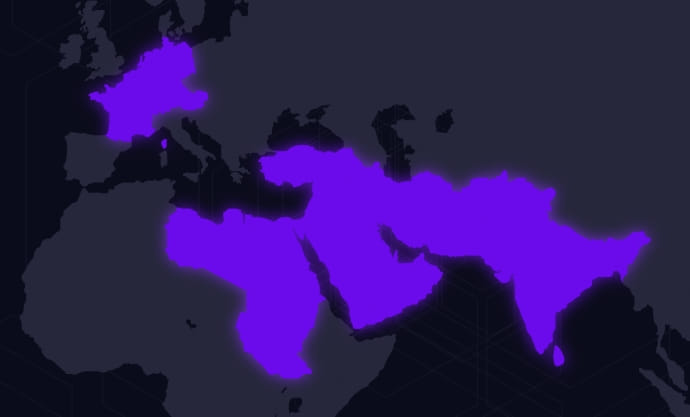
The Sandman risk actor targets telecommunication service suppliers within the Center East, Western Europe, and South Asia subcontinents.
SentinelOne says the risk actor first beneficial properties entry to a company community utilizing stolen administrative credentials.
As soon as the community is breached, Sandman has been seen utilizing “pass-the-hash” assaults to authenticate to distant servers and providers by extracting and reusing NTLM hashes saved in reminiscence.
The SentinelLabs report explains that, in a single occasion, all workstations focused by the hackers have been assigned to managerial personnel, indicating the attacker’s curiosity in privileged or confidential data.
Supply: SentinelLabs
LuaDream malware
SandMan has been seen deploying a brand new modular malware named ‘LuaDream’ in assaults utilizing DLL hijacking on focused programs. The malware will get its title from utilizing the LuaJIT just-in-time compiler for the Lua scripting language
The malware is used to gather knowledge and handle plugins that stretch its performance, that are obtained from the command and management server (C2) and executed regionally on the compromised system.
The malware’s improvement seems to be lively, with a retrieved model string indicating the discharge quantity “12.0.2.5.23.29,” and the analysts have seen indicators of logs and testing features going way back to June 2022.
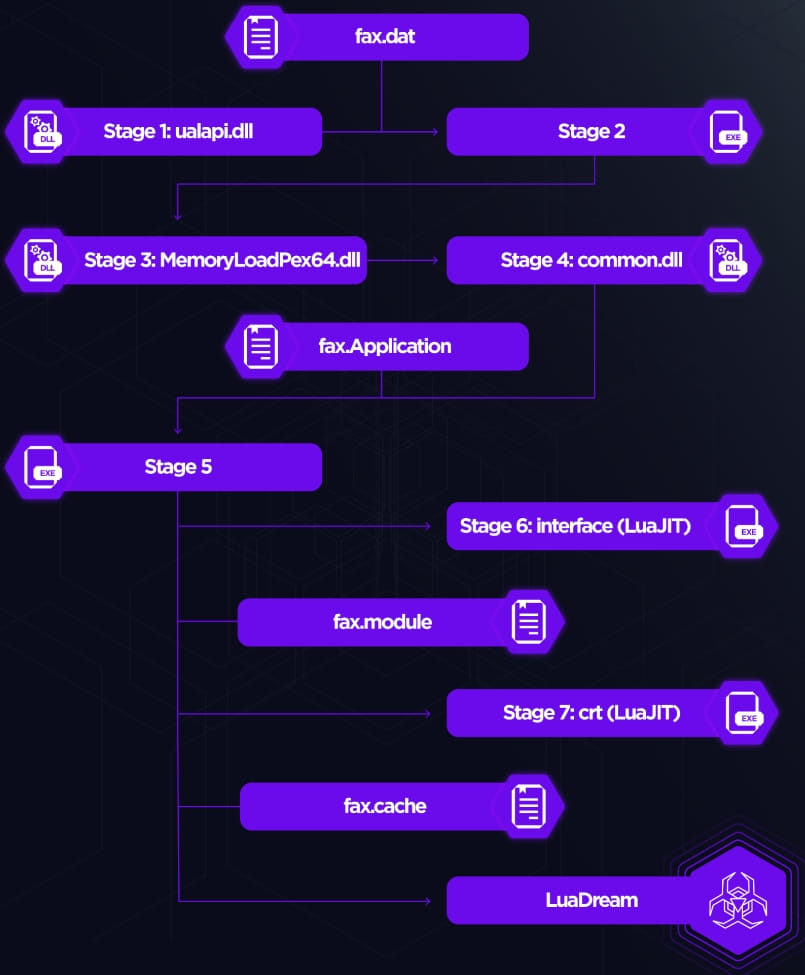
LuaDream’s staging depends on a complicated seven-step in-memory course of aiming to evade detection, initiated by both the Home windows Fax or Spooler service, which runs the malicious DLL file.
Supply: SentinelLabs
SentinelLabs stories that the timestamps within the DLL recordsdata used for order hijacking are very near the assaults, which could point out they have been custom-created for particular intrusions.
Anti-analysis measures within the staging course of embody:
- Concealing LuaDream’s threads from debuggers.
- Closing recordsdata with an invalid deal with.
- Detecting Wine-based sandbox environments.
- In-memory mapping to dodge EDR API hooks and file-based detections.
- Packing staging code with XOR-based encryption and compression.
LuaDream includes 34 parts, with 13 core and 21 assist parts, which make the most of the LuaJIT bytecode and the Home windows API via the ffi library.
Core parts deal with the malware’s main features, like system and person knowledge assortment, plugin management, and C2 communications, whereas assist parts cope with the technical elements, like offering Lua libs and Home windows API definitions.
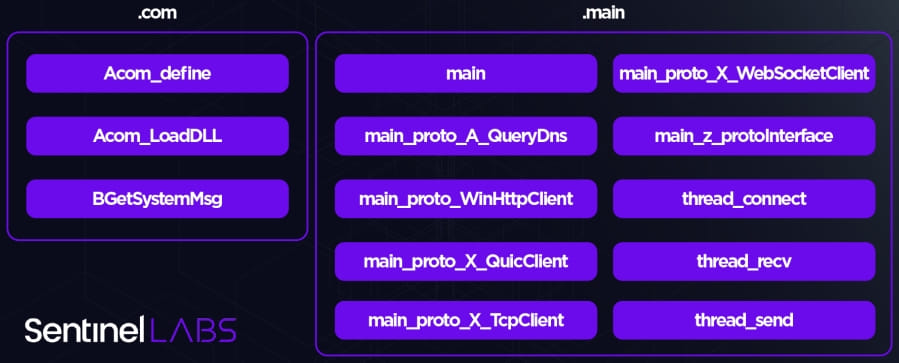
Upon initialization, LuaDream connects to a C2 server (by way of TCP, HTTPS, WebSocket, or QUIC) and sends gathered data, together with malware variations, IP/MAC addresses, OS particulars, and so forth.
Because of the attackers deploying particular plugins via LuaDream in every assault, SentinelLabs does not have an exhaustive record of all plugins out there.
Nonetheless, the report notes one module named ‘cmd,’ whose title suggests it offers the attackers command execution capabilities on the compromised system.
Whereas a few of Sandman’s {custom} malware and a part of its C2 server infrastructure have been uncovered, the risk actor’s origin stays unanswered.
Sandman joins a rising record of superior attackers focusing on telecom firms for espionage, utilizing distinctive stealthy backdoors which might be difficult to detect and cease.
Telecommunication suppliers are a frequent goal for espionage actions as a result of delicate nature of the info they handle.
Earlier this week, we reported on a brand new cluster of exercise tracked as ‘ShroudedSnooper‘ that used two novel backdoors, HTTPSnoop and PipeSnoop, towards telecommunication carriers within the Center East.
[ad_2]