
[ad_1]
One of the costly points of any cybercriminal operation is the effort and time it takes to always create giant numbers of latest throwaway e-mail accounts. Now a brand new service presents to assist dramatically minimize prices related to large-scale spam and account creation campaigns, by paying individuals to promote their e-mail account credentials and letting prospects quickly lease entry to an enormous pool of established accounts at main suppliers.

The service in query — kopeechka[.]retailer — is probably greatest described as a type of unidirectional e-mail confirmation-as-a-service that guarantees to “save your money and time for efficiently registering a number of accounts.”
“Are you engaged on giant volumes and are prices always rising?” Kopeechka’s web site asks. “Our service will remedy all of your issues.”
As a buyer of this service, you don’t get full entry to the e-mail inboxes you might be renting. Fairly, you configure your botnet or spam machine to make an automatic utility programming interface (API) name to the Kopeechka service, which responds with a working e-mail tackle at an e-mail supplier of your selecting.
When you’ve entered the provided e-mail tackle into the brand new account registration web page at some web site or service, you inform Kopeechka which service or web site you’re anticipating an account affirmation hyperlink from, and they’ll then ahead any new messages matching that description to your Kopeechka account panel.
Guaranteeing that prospects can not management inboxes rented by means of the service implies that Kopeechka can lease the identical e-mail tackle to a number of prospects (a minimum of till that e-mail tackle has been used to register accounts at a lot of the main on-line providers).
Kopeechka additionally has a number of affiliate packages, together with one which pays app builders for embedding Kopeechka’s API of their software program. Nonetheless, much more attention-grabbing is their program for rewarding individuals who select to promote Kopeechka usernames and passwords for working e-mail addresses.
Kopeechka means “penny” in Russian, which is beneficiant verbiage (and coinage) for a service that fees a tiny fraction of a penny for entry to account affirmation hyperlinks. Their pricing fluctuates barely primarily based on which e-mail supplier you select, however a type on the service’s homepage says a single affirmation message from apple.com to outlook.com prices .07 rubles, which is presently equal to about $0.00087 {dollars}.
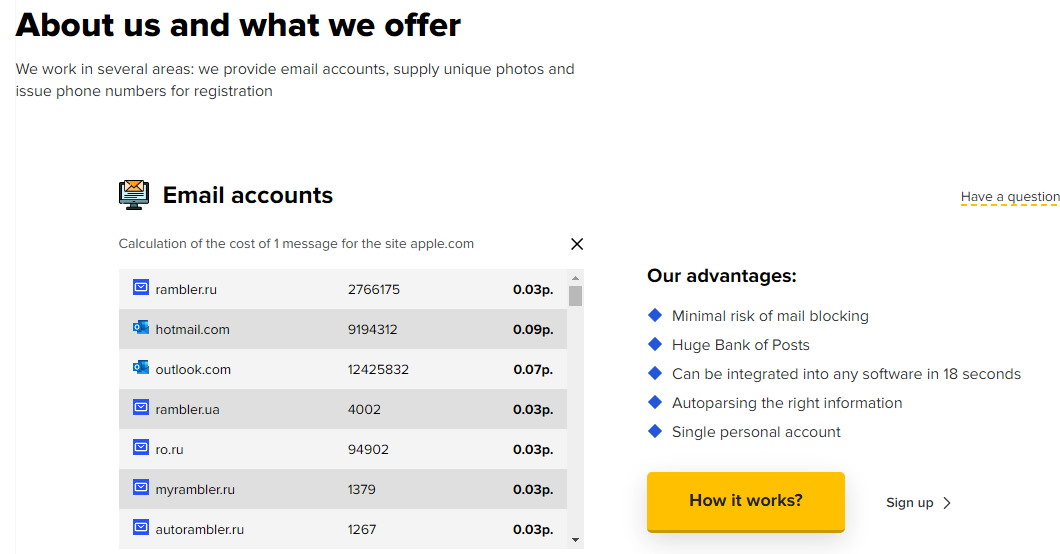
The pricing for Kopeechka works out to a few fraction of a penny per affirmation message.
“Emails may be uploaded to us on the market, and you’ll obtain a share of purchases %,” the service explains. “You add 1 mailbox of a sure area, focus on share with our technical assist (it depends upon the liquidity of the area and the variety of downloaded emails).”
We don’t should look very far for examples of Kopeechka in motion. In Could, KrebsOnSecurity interviewed a Russian spammer named “Quotpw“ who was mass-registering accounts on the social media community Mastodon so as to conduct a sequence of big spam campaigns promoting rip-off cryptocurrency funding platforms.
A lot of the fodder for that story got here from Renaud Chaput, a contract programmer engaged on modernizing and scaling the Mastodon challenge infrastructure — together with joinmastodon.org, mastodon.on-line, and mastodon.social. Chaput instructed KrebsOnSecurity that his group was compelled to quickly halt all new registrations for these communities final month after the variety of new registrations from Quotpw’s spam marketing campaign began to overwhelm their programs.
“We out of the blue went from like three registrations per minute to 900 a minute,” Chaput mentioned. “There was nothing within the Mastodon software program to detect that exercise, and the protocol shouldn’t be designed to deal with this.”
After that story ran, Chaput mentioned he found that the pc code powering Quotpw’s spam botnet (which has since been launched as open supply) contained an API name to Kopeechka’s service.
“It permits them to pool many bot-created or compromised emails at numerous suppliers and supply them to cyber criminals,” Chaput mentioned of Kopeechka. “That is what they used to create 1000’s of legitimate Hotmail (and different) addresses when spamming on Mastodon. If you happen to take a look at the code, it’s very well achieved with a pleasant API that forwards you the affirmation hyperlink that you could then pretend click on along with your botnet.”
It’s uncertain anybody will make critical cash promoting e-mail accounts to Kopeechka, until after all that particular person already occurs to run a botnet and has entry to ridiculous numbers of e-mail credentials. And in that sense, this service is genius: It basically presents scammers a brand new solution to wring additional earnings from sources which are already plentiful for them.
One remaining observe about Quotpw and the spam botnet that ravaged Chaput’s Mastodon servers final month: Pattern Micro simply printed a report saying Quotpw was spamming to earn cash for a Russian-language associates program referred to as “Impulse Staff,” which pays individuals to advertise cryptocurrency scams.
The crypto rip-off associates program “Venture Impulse,” promoting in 2021.
Web sites below the banner of the Impulse Rip-off Crypto Venture are all basically “superior price” scams that inform individuals they’ve earned a cryptocurrency funding credit score. Upon registering on the web site, guests are instructed they should make a minimal deposit on the service to gather the award. Nonetheless, those that make the preliminary funding by no means hear from the location once more, and their cash is gone.
Curiously, Pattern Micro says the scammers behind the Impulse Staff additionally seem like working a pretend repute service referred to as Rip-off-Doc[.]com, a web site that mimics the reputable Scamdoc.com for measuring the trustworthiness and authenticity of assorted websites. Pattern notes that the phony repute web site routinely gave excessive belief rankings to quite a lot of cryptocurrency rip-off and on line casino web sites.
“We are able to solely suppose that both the identical cybercriminals run operations involving each or that a number of totally different cybercriminals share the scam-doc[.]com web site,” the Pattern researchers wrote.
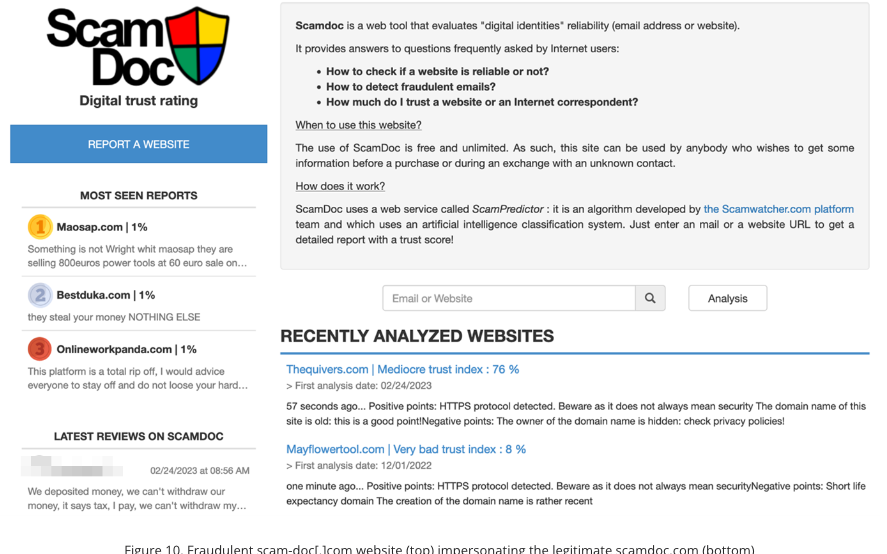
The ScamDoc pretend repute web sites, which have been apparently used to assist make pretend crypto funding platforms look extra reliable. Picture: Pattern Micro.
In line with the FBI, monetary losses from cryptocurrency funding scams dwarfed losses for all different forms of cybercrime in 2022, rising from $907 million in 2021 to $2.57 billion final yr.
[ad_2]