[ad_1]
A brand new evaluation of the delicate business spy ware referred to as Predator has revealed that its skill to persist between reboots is obtainable as an “add-on characteristic” and that it is determined by the licensing choices opted by a buyer.
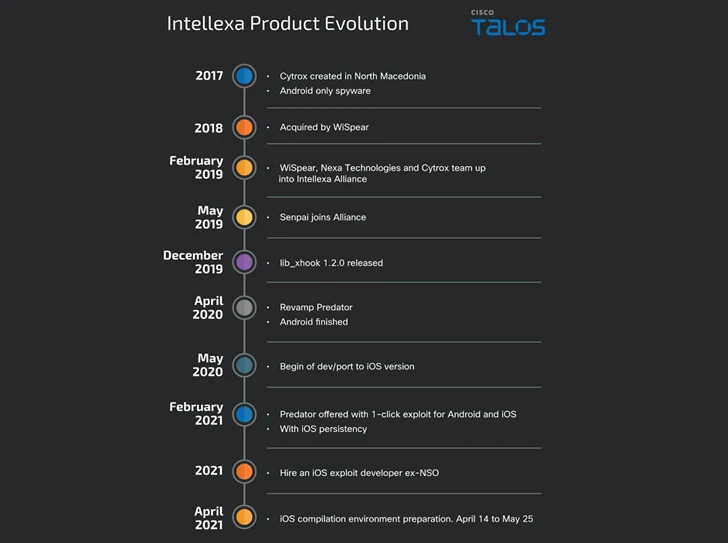
“In 2021, Predator spy ware could not survive a reboot on the contaminated Android system (it had it on iOS),” Cisco Talos researchers Mike Gentile, Asheer Malhotra, and Vitor Ventura mentioned in a report shared with The Hacker Information. “Nevertheless, by April 2022, that functionality was being provided to their clients.”
Predator is the product of a consortium referred to as the Intellexa Alliance, which incorporates Cytrox (subsequently acquired by WiSpear), Nexa Applied sciences, and Senpai Applied sciences. Each Cytrox and Intellexa have been added to the Entity Record by the U.S. in July 2023 for “trafficking in cyber exploits used to achieve entry to info techniques.”
The newest findings come greater than six months after the cybersecurity vendor detailed the internal workings of Predator and its harmonious equation with one other loader element referred to as Alien.
“Alien is essential to Predator’s profitable functioning, together with the extra elements loaded by Predator on demand,” Malhotra instructed The Hacker Information on the time. “The connection between Alien and Predator is extraordinarily symbiotic, requiring them to repeatedly work in tandem to spy on victims.”
Beat AI-Powered Threats with Zero Belief – Webinar for Safety Professionals
Conventional safety measures will not lower it in right now’s world. It is time for Zero Belief Safety. Safe your knowledge like by no means earlier than.
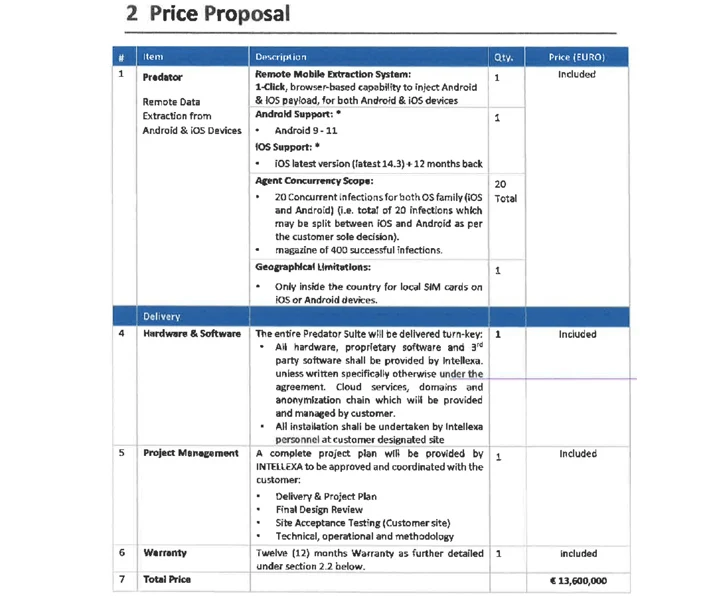
Predator, which may goal each Android and iOS, has been described as a “distant cellular extraction system” that is offered on a licensing mannequin that run into tens of millions of {dollars} primarily based on the exploit used for preliminary entry and the variety of concurrent infections, placing them out of attain of script kiddies and novice criminals.
Adware reminiscent of Predator and Pegasus, which is developed by NSO Group, usually depend on zero-day exploit chains in Android, iOS, and net browsers as covert intrusion vectors. As Apple and Google proceed to plug the safety gaps, these exploit chains could also be rendered ineffective, forcing them to return to the drafting board.
Nevertheless, it is value noting that the businesses behind mercenary surveillance instruments may also procure both full or partial exploit chains from exploit brokers and vogue them into an operational exploit that may be employed to successfully breach goal units.
One other key facet of Intellexa’s enterprise mannequin is that offloads the work of establishing the assault infrastructure to the purchasers themselves, leaving it with room for believable deniability ought to the campaigns come to mild (because it inevitably does).
“The supply of Intellexa’s supporting {hardware} is completed at a terminal or airport,” the researchers mentioned.
“This supply technique is called Value Insurance coverage and Freight (CIF), which is a part of the transport trade’s jargon (‘Incoterms’). This mechanism permits Intellexa to say that they haven’t any visibility of the place the techniques are deployed and ultimately positioned.”
On prime of that, Intellexa possesses “first-hand information” of whether or not their clients are performing surveillance operations exterior their very own borders owing to the truth that the operations are intrinsically related to the license, which, by default, is restricted to a single cellphone nation code prefix.
This geographic limitation, nonetheless, will be loosened for a further charge.
Cisco Talos famous that whereas public publicity of private-sector offensive actors and their campaigns have been profitable at attribution efforts, it has had little influence on their skill to conduct and develop their enterprise the world over, even when it could have an effect on their clients, reminiscent of governments.
“It might enhance the prices by making them purchase or create new exploit chains however these distributors seem to have seamlessly acquired new exploit chains, enabling them to stay in enterprise by leaping from one set of exploits to a different as a method of preliminary entry,” the researchers mentioned.
“What is required is the general public disclosure of technical analyses of the cellular spy ware and tangible samples enabling public scrutiny of the malware. Such public disclosures is not going to solely allow better analyses and drive detection efforts but in addition impose improvement prices on distributors to always evolve their implants.”
[ad_2]