[ad_1]
A brand new malware pressure referred to as BundleBot has been stealthily working beneath the radar by benefiting from .NET single-file deployment strategies, enabling risk actors to seize delicate info from compromised hosts.
“BundleBot is abusing the dotnet bundle (single-file), self-contained format that leads to very low or no static detection in any respect,” Verify Level stated in a report printed this week, including it’s “generally distributed through Fb Adverts and compromised accounts resulting in web sites masquerading as common program utilities, AI instruments, and video games.”
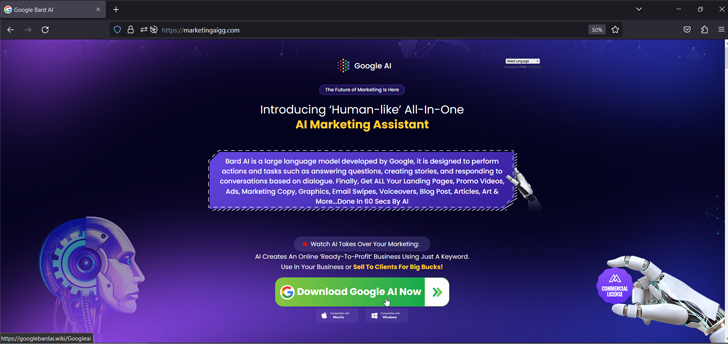
A few of these web sites intention to imitate Google Bard, the corporate’s conversational generative synthetic intelligence chatbot, attractive victims into downloading a bogus RAR archive (“Google_AI.rar”) hosted on reliable cloud storage companies corresponding to Dropbox.
The archive file, when unpacked, comprises an executable file (“GoogleAI.exe”), which is the .NET single-file, self-contained software (“GoogleAI.exe”) that, in flip, incorporates a DLL file (“GoogleAI.dll”), whose accountability is to fetch a password-protected ZIP archive from Google Drive.
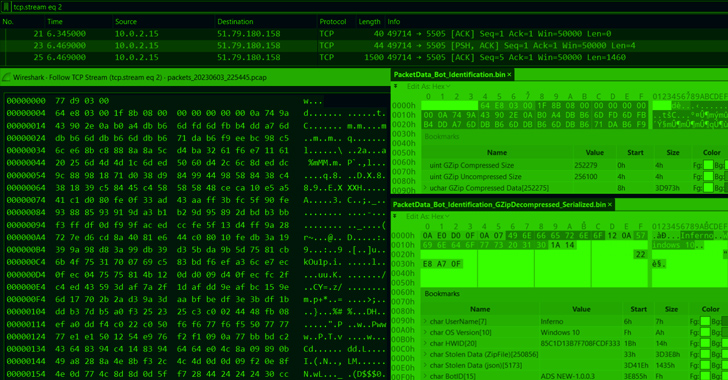
The extracted content material of the ZIP file (“ADSNEW-1.0.0.3.zip”) is one other .NET single-file, self-contained software (“RiotClientServices.exe”) that comes with the BundleBot payload (“RiotClientServices.dll”) and a command-and-control (C2) packet information serializer (“LirarySharing.dll”).
“The meeting RiotClientServices.dll is a {custom}, new stealer/bot that makes use of the library LirarySharing.dll to course of and serialize the packet information which can be being despatched to C2 as part of the bot communication,” the Israeli cybersecurity firm stated.
The binary artifacts make use of custom-made obfuscation and junk code in a bid to withstand evaluation, and include capabilities to siphon information from internet browsers, seize screenshots, seize Discord tokens, info from Telegram, and Fb account particulars.
Verify Level stated it additionally detected a second BundleBot pattern that is just about equivalent in all facets barring the usage of HTTPS to exfiltrate the knowledge to a distant server within the type of a ZIP archive.
“The delivering methodology through Fb Adverts and compromised accounts is one thing that has been abused by risk actors for some time, nonetheless combining it with one of many capabilities of the revealed malware (to steal a sufferer’s Fb account info) might function a tough self-feeding routine,” the corporate famous.
The event comes as Malwarebytes uncovered a brand new marketing campaign that employs sponsored posts and compromised verified accounts that impersonate Fb Adverts Supervisor to entice customers into downloading rogue Google Chrome extensions which can be designed to steal Fb login info.
Customers who click on on the embedded hyperlink are prompted to obtain a RAR archive file containing an MSI installer file that, for its half, launches a batch script to spawn a brand new Google Chrome window with the malicious extension loaded utilizing the “–load-extension” flag –
begin chrome.exe –load-extension=”%~dp0/nmmhkkegccagdldgiimedpiccmgmiedagg4″ “https://www.fb.com/enterprise/instruments/ads-manager”
Protect Towards Insider Threats: Grasp SaaS Safety Posture Administration
Anxious about insider threats? We have you lined! Be a part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
“That {custom} extension is cleverly disguised as Google Translate and is taken into account ‘Unpacked’ as a result of it was loaded from the native laptop, slightly than the Chrome Internet Retailer,” Jérôme Segura, director of risk intelligence at Malwarebytes, defined, noting it’s “completely targeted on Fb and grabbing vital items of data that might permit an attacker to log into accounts.”
The captured information is subsequently despatched utilizing the Google Analytics API to get round content material safety insurance policies (CSPs) to mitigate cross-site scripting (XSS) and information injection assaults.
The risk actors behind the exercise are suspected to be of Vietnamese origin, who’ve, in current months, exhibited acute curiosity in concentrating on Fb enterprise and promoting accounts. Over 800 victims worldwide have been impacted, with 310 of these situated within the U.S.
“Fraudsters have a number of time on their palms and spend years learning and understanding find out how to abuse social media and cloud platforms, the place it’s a fixed arm’s race to maintain unhealthy actors out,” Segura stated. “Do not forget that there isn’t a silver bullet and something that sounds too good to be true might very properly be a rip-off in disguise.”
[ad_2]