
[ad_1]
The latest Gcore Radar report and its aftermath have highlighted a dramatic improve in DDoS assaults throughout a number of industries. Originally of 2023, the common power of assaults reached 800 Gbps, however now, even a peak as excessive as 1.5+ Tbps is unsurprising. To try to break via Gcore’s defenses, perpetrators made two makes an attempt with two completely different methods. Learn on to find what occurred and find out how the safety supplier stopped the attackers of their tracks with out affecting finish customers’ experiences.
A Highly effective DDoS Assaults
In November 2023, one in every of Gcore’s prospects from the gaming business was focused by two large DDoS assaults, peaking at 1.1 and 1.6 Tbps respectively. The attackers deployed numerous methods in an unsuccessful try and compromise Gcore’s protecting mechanisms.
Assault #1: 1.1 Tbps UDP-based DDoS
Within the first cyber assault, the attackers despatched a barrage of UDP site visitors to a goal server, peaking at 1.1 Tbps. Two strategies had been employed:
- Through the use of random UDP supply ports, they hoped to evade typical filtering mechanisms.
- The attackers hid their real id by forging supply IP addresses.
This was a basic flood (or volumetric) assault, whereby the attackers hoped to devour all accessible bandwidth of or to an information heart or community, overwhelming the goal servers with site visitors and making them unavailable to reliable customers.
The graph under reveals buyer’s site visitors throughout the assault. The height of 1.1 Tbps reveals an aggressive however short-lived try and flood the community with information. The inexperienced line (“whole.common.enter”) reveals all inbound site visitors. The opposite coloured strains on the graph symbolize the community’s responses, together with measures to filter and drop malicious site visitors, because the system manages the deluge of information.
 |
| The assault comprised a brief however intense peak of 1.1 Tbps round 22:55 |
Assault #2: 1.6 Tbps TCP-based DDoS
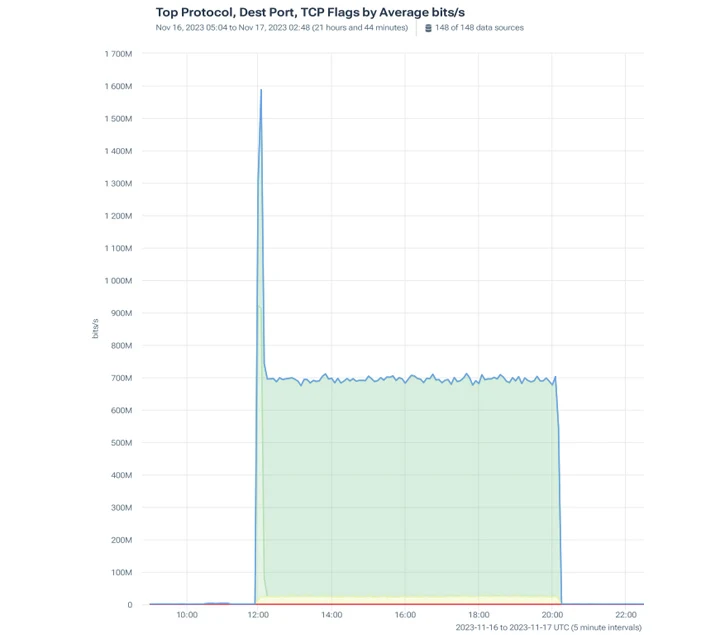 |
| The assault’s constant site visitors quantity was 700 Mbps and on the onset peaked at 1600 Mbps |
This time, the attackers tried to take advantage of TCP protocol with a mixture of SYN flood, PSH, and ACK site visitors.
In a SYN flood assault, a number of SYN packets are delivered to the goal server with out ACK packets. This implies the server generates a half-open connection for every SYN packet. If profitable, the server will in the end run out of sources and cease accepting connections.
The PSH, ACK part of the assault quickly sends information to the goal system. The ACK flag alerts that the server acquired the earlier packet. This pushes the system to deal with information promptly, losing sources. A SYN flood assault utilizing PSH, ACK packets is tougher to defend in opposition to than a SYN flood, for the reason that PSH flag causes the server to course of the packet contents instantly, consuming extra sources.
As earlier than, the objective was to overload the shopper’s servers and make their companies inaccessible to approved customers. This SYN flood had a peak quantity of 685.77 Mbps and the PSH, ACK had a magnitude of 906.73 Mbps.
Gcore’s Defensive Methods
Gcore’s DDoS Safety successfully neutralized each assaults whereas preserving common service for the shopper’s finish customers. The overall method of keeping off DDoS safety threats contains a number of methods, akin to Gcore’s front-line defenses:
- Dynamic site visitors shaping: Dynamically adjusted site visitors charges successfully mitigate the influence of the assault whereas guaranteeing the continuity of vital companies. To be able to prioritize real site visitors whereas slowing dangerous transmissions, adaptive thresholds and charge restrictions are used.
- Anomaly detection and quarantine: Fashions primarily based on machine studying analyze habits to determine anomalies. When an anomaly happens, automated quarantine mechanisms redirect inaccurate site visitors to remoted segments for extra evaluation.
- Common expression filters: To dam malicious payloads with out disrupting reliable site visitors, common expression-based filter guidelines are carried out. Their steady fine-tuning ensures optimum safety with out false positives.
- Collaborative risk intelligence: Gcore actively engages within the change of risk intelligence with business friends. Collective insights and real-time risk feeds information Gcore’s safety methods, permitting a speedy response to growing assault vectors.
By using these methods, Gcore was capable of successfully mitigate the influence of DDoS assaults and shield their buyer’s platform from disruption, negating potential reputational and monetary losses.
Conclusion
DDoS assaults of 1.5+ Tbps quantity pose an rising hazard throughout industries, with attackers utilizing imaginative methods to try to bypass safety companies. Over the course of 2023, Gcore has registered will increase in each common and most assault volumes, and these two related assaults display that pattern.
Within the assaults coated within the article, Gcore was capable of stop any harm via a mixture of dynamic site visitors shaping, anomaly detection, common expression filters, and collaborative risk intelligence. Discover DDoS Safety choices to safe your community in opposition to ever-evolving DDoS threats.
[ad_2]
