
[ad_1]
As the vacation season of 2023 unfolded, it introduced not solely cheer and celebration but in addition a surge in Distributed Denial-of-Service (DDoS) assaults. This yr’s developments in DDoS assaults reveal a fancy and evolving risk panorama. From misconfigured Docker API endpoints enabling botnet supply to the emergence of NKAbuse malware exploiting blockchain know-how for DDoS assaults, the techniques and scale of those assaults have proven important sophistication and diversification.
The 2023 vacation season assault panorama in Azure
In our monitoring of the assault panorama through the vacation season, we noticed a notable shift in a few of the assault patterns in comparison with the earlier yr. This transformation underscores the relentless efforts of malicious actors to refine their risk techniques and try to avoid DDoS safety methods.
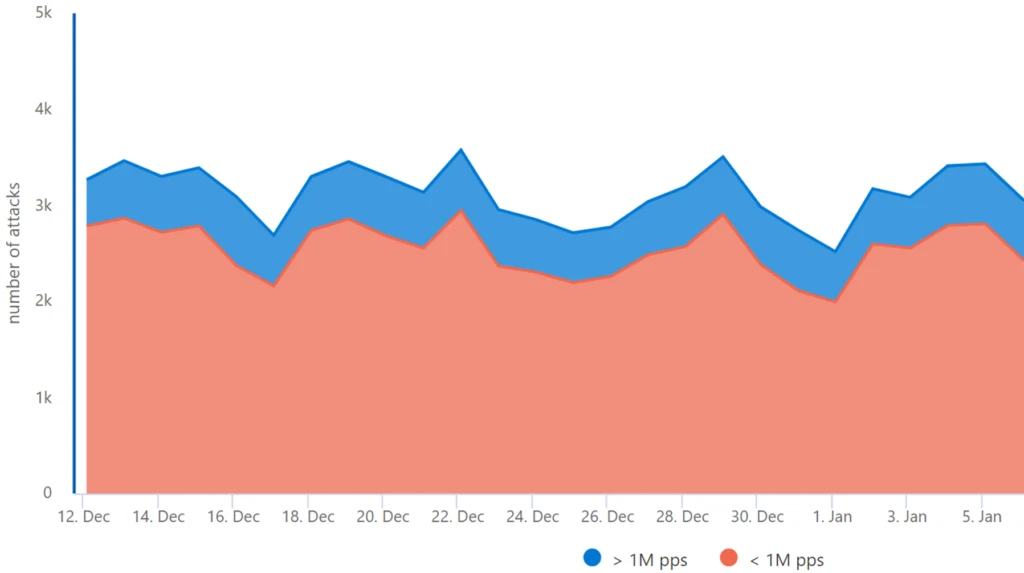
Day by day Assault Quantity: Azure’s strong safety infrastructure routinely mitigated a peak of 3,500 assaults every day. Notably, large-scale assaults, exceeding 1 million packets per second (pps), constituted 15%-20% of those incidents.*
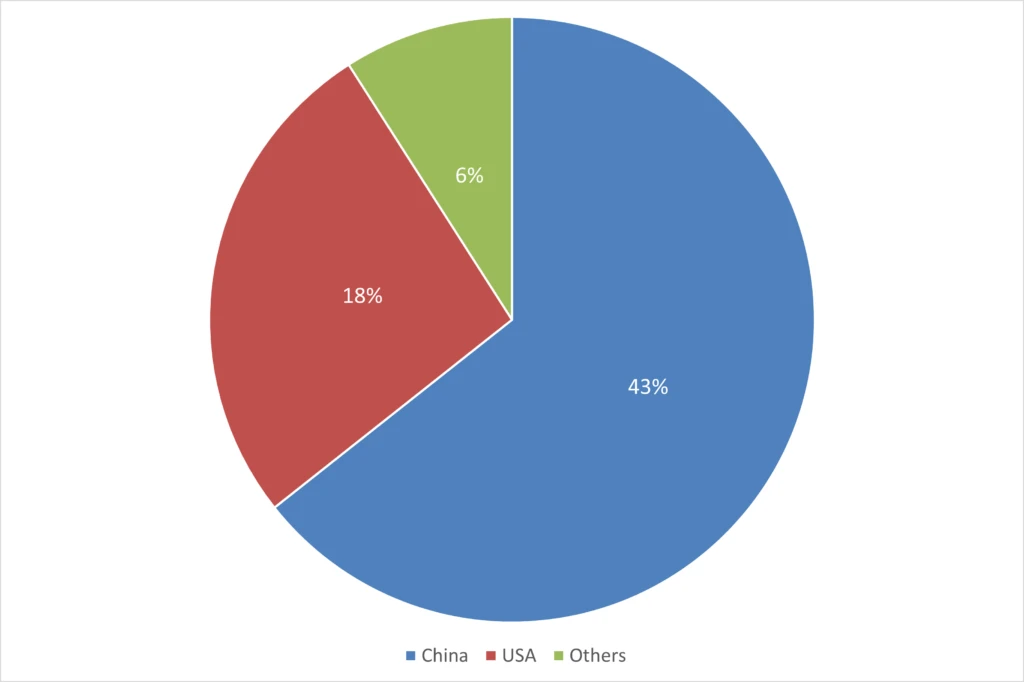
Geographical origins: A shift in assault origins was noticed, with 43% originating from China and 18% from the USA.* This marks a change from the earlier yr, the place each nations had been equally represented as regional sources.
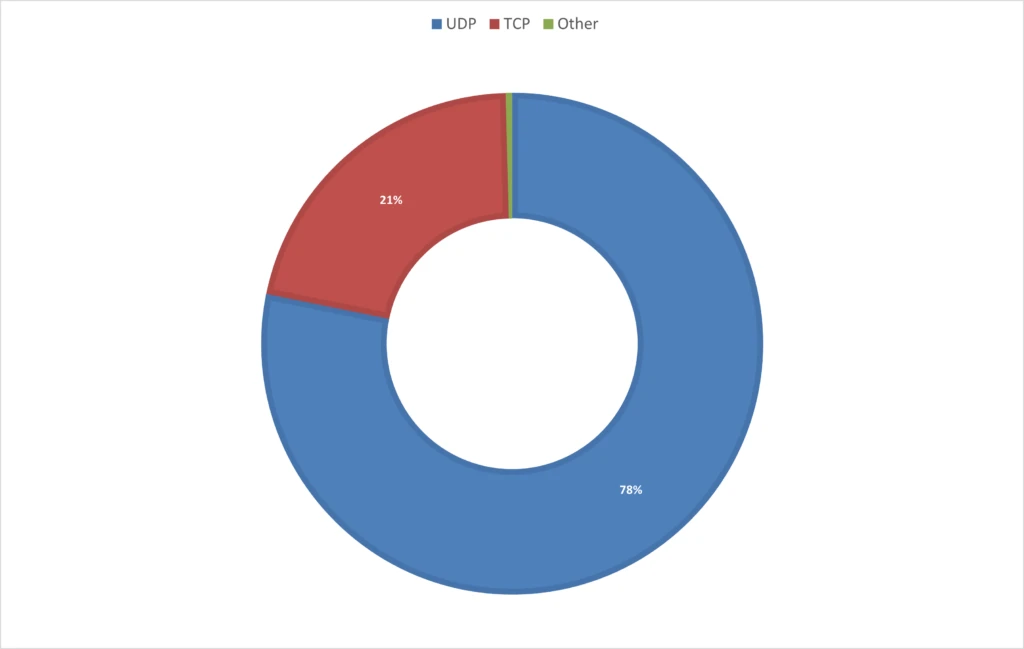
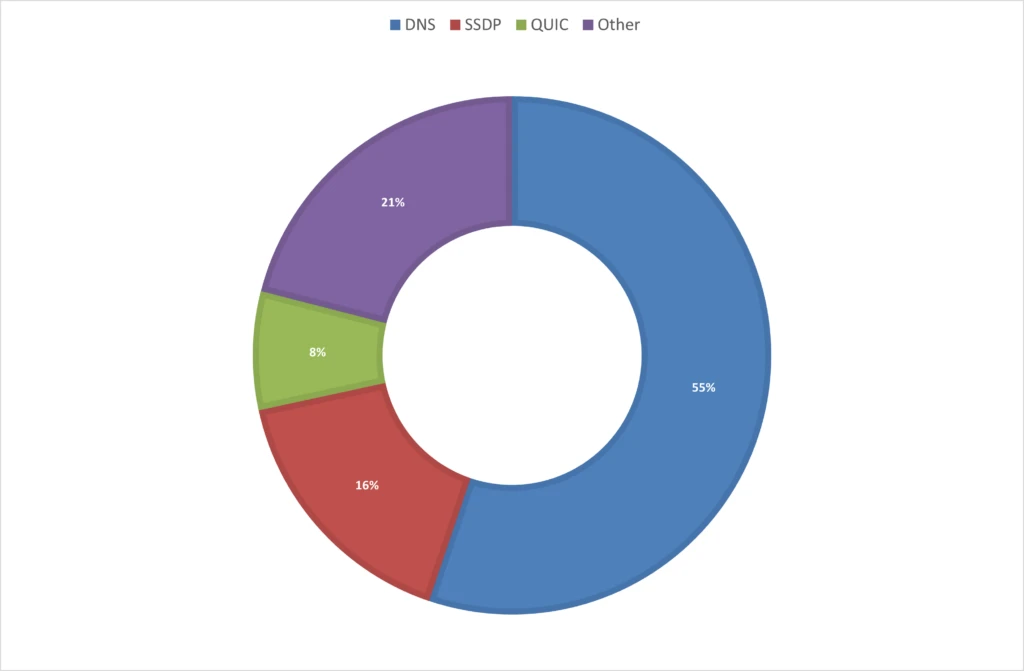
Assault protocols: The 2023 vacation season noticed a predominant use of UDP-based assaults, concentrating on gaming workloads and net purposes, accounting for 78% of the assaults. These embrace UDP mirrored/amplified assaults, which predominantly leverage area title system (DNS) and easy service discovery protocol (SSDP), in addition to fast UDP web connections (QUIC) for reflection functions. Notably, QUIC is rising as a extra widespread assault vector, both by reflection or by DDoS stressors that make the most of UDP port 443 randomly. This yr’s vacation season assault patterns distinction sharply with the earlier yr, the place TCP-based assaults dominated 65% of all assaults.*
File-breaking assault: A staggering UDP assault, peaking at 1.5 terabits per second (Tbps), focused a gaming buyer in Asia. This assault, originating from China, Japan, the USA, and Brazil, was extremely randomized, involving quite a few supply IPs and ports, but was totally mitigated by Azure’s defenses.
Botnet evolution: Prior to now yr, cybercriminals more and more leveraged cloud assets, notably digital machines, for DDoS assaults. This pattern continued to evolve through the vacation season, with attackers making an attempt to use discounted Azure subscriptions globally. From mid-November 2023 and till finish of yr, we monitored compromised account makes an attempt in 39 Azure areas, with Europe and the USA being the first targets, accounting for about 67% of those incidents.* Azure’s protection mechanisms efficiently neutralized these threats.
Contextualizing the risk
The 2023 DDoS assault developments in Azure mirror international patterns. Assaults are turning into politically motivated as we highlighted earlier final yr, fueled by geopolitical tensions.
The emergence of DDoS-for-hire companies, generally referred to as “stressers” and “booters” stay in style amongst attackers. These platforms, available on cybercriminal boards, have democratized the power to launch highly effective DDoS assaults, making them accessible to much less subtle criminals for minimal prices. Current years have seen an uptick within the availability and use of those companies, confirmed by worldwide regulation enforcement companies by operations like Operation PowerOFF, which final yr in Could focused 13 domains related to DDoS-for-hire platforms. Regardless of these efforts, stressers proceed to thrive, providing a spread of assault strategies and energy, with some able to assaults as much as 1.5 Tbps.
Cloud energy: Combating the evolving DDoS threats
The rise of botnets at scale and DDoS-for-hire companies poses a big danger to on-line companies and enterprise operations. To combat these threats, extra cloud computing energy is required to soak up the main wave of the assault till patterns might be recognized, spurious visitors diverted, and bonafide visitors preserved. When tens of hundreds of gadgets represent an assault, the cloud is our greatest protection, because of the scale wanted to mitigate the most important assaults. As well as, because of the international distribution of the cloud, nearer proximity helps to dam assaults closest to the sources.
Guaranteeing strong safety
In an period the place digital threats are consistently evolving, making certain strong safety towards DDoS assaults has by no means been extra important. Right here’s how Azure’s complete safety options are designed to safeguard your digital infrastructure.
DDoS Safety Service: With the excessive danger of DDoS assaults, it’s important to have a DDoS safety service like Azure DDoS Safety. This service offers always-on visitors monitoring, computerized assault mitigation upon detection, adaptive real-time tuning, and full visibility on DDoS assaults with real-time telemetry, monitoring, and alerts.
Multi-Layered Protection: For complete safety, arrange a multi-layered protection by deploying Azure DDoS Safety with Azure Internet Utility Firewall (WAF). Azure DDoS Safety secures the community layer (Layer 3 and 4), whereas Azure WAF safeguards the appliance layer (Layer 7). This mix offers safety towards varied kinds of DDoS assaults.
Alert Configuration: Azure DDoS Safety can determine and mitigate assaults with out consumer intervention. Configuring alerts for energetic mitigations can maintain you knowledgeable concerning the standing of protected public IP assets.

Azure DDoS Safety
Shield your Azure assets from distributed denial-of-service (DDoS) assaults.
2024: Rising towards DDoS threats
The 2023 vacation season has underscored the relentless and evolving risk of DDoS assaults within the cyber panorama. As we transition into the brand new yr, it turns into essential for organizations to reinforce and adapt their cybersecurity methods. This era needs to be a studying curve, specializing in fortifying defenses towards such DDoS assaults and staying vigilant towards new techniques. The resilience of Azure towards these subtle DDoS threats highlights the important want for strong and adaptive safety measures, not simply in defending digital property but in addition in making certain uninterrupted enterprise operations.
* Based mostly on inner knowledge
[ad_2]