
[ad_1]
Quite a lot of fashionable community threats contain information theft through abuse of community companies, which is termed information exfiltration. To trace such threats, analysts monitor information transfers out of the group’s community, significantly information transfers occurring through community companies not primarily meant for bulk switch companies. One such service is the Area Title System (DNS), which is important for a lot of different Web companies. Sadly, attackers can manipulate DNS to exfiltrate information in a covert method.
This SEI weblog publish focuses on how the DNS protocol may be abused to exfiltrate information by including bytes of knowledge onto DNS queries or making repeated queries that include information encoded into the fields of the question. The publish additionally examines the final visitors analytic we will use to determine this abuse and applies a number of instruments out there to implement the analytic. The mixture dimension of DNS packets can present a prepared indicator of DNS abuse. Nevertheless, as a result of the DNS protocol has grown from a easy handle decision mechanism to distributed database assist for community connectivity, decoding the combination dimension requires understanding of the context of queries and responses. By understanding the quantity of DNS visitors, each in isolation and in mixture, analysts could higher match outgoing queries and incoming responses.
The info used on this weblog publish is the CIC-BELL-DNS-EXF 2021 information set, as revealed together with the paper Light-weight Hybrid Detection of Knowledge Exfiltration utilizing DNS based mostly on Machine Studying by Samaneh Mahdavifar et al.
The Function of DNS
DNS helps a number of sorts of queries. These queries are described in quite a lot of Web Engineering Job Drive (IETF) Request for Remark (RFC) paperwork. These RFCs embrace the next:
- A and AAAA queries for IP handle equivalent to a site identify (e.g., “which handle corresponds to www.instance.com?” with a response like “192.0.2.27”)
- pointer document (PTR) queries for identify equivalent to an IP handle (e.g., “which identify corresponds to 192.0.2.27?” with a response of “www.instance.com”)
- identify server (NS), mail trade (MX), and service locator (SRV) queries for the identification of key servers in a given area
- begin of authority (SOA) queries for details about addresses on which the queried server could converse authoritatively
- certificates (CERT) queries for encryption certificates pertaining to the server’s lined domains
- textual content document (TXT) queries for added data (as configured by the community administrator) in a textual content format
A given DNS question packet will request data on a given area from a specific server, however the response from that server could embrace a number of useful resource information. The scale of the response will rely on what number of useful resource information are returned and the kind of every document.
As soon as analysts perceive the explanations for monitoring DNS visitors and the context wanted for decoding the monitoring outcomes, they will then decide what data is desired from the monitoring. This weblog publish assumes the analyst desires to trace exterior hosts that could be receiving exfiltrated data.
Overview of the Analytic for Figuring out Knowledge Exfiltration
The analytic lined on this weblog publish assumes that the networks of curiosity are lined by visitors sensors that produce community circulation information or at the least packet captures that may be aggregated into community circulation information. There are a selection of instruments out there to generate these circulation information. As soon as produced, the circulation information are archived in a circulation repository or acceptable database tables, relying on the evaluation device suite.
The method taken on this analytic is, first, to mixture DNS visitors related to exterior locations performing like servers and, second, to profile the visitors for these locations. Step one (affiliation) entails figuring out DNS visitors (both by service port or by precise examination of the appliance protocol), then figuring out the exterior locations concerned. The second step (profiling) examines what number of sources are speaking with every of the locations, the combination byte rely, packet rely, and different revealing data as described within the following sections.
A number of completely different instruments can be utilized for this evaluation. This weblog publish will focus on two units of SEI-developed instruments:
- The System for Web-Degree Information (SiLK) is a set of visitors evaluation instruments developed to facilitate safety evaluation of enormous networks. The SiLK device suite helps the environment friendly assortment, storage, and evaluation of community circulation information, enabling community safety analysts to quickly question massive historic visitors information units. SiLK is ideally fitted to analyzing visitors on the spine or border of a big, distributed enterprise or mid-sized ISP.
- Mothra is a set of Apache Spark libraries that assist evaluation of community circulation information in Web Protocol Circulation Data Export(IPFIX) format with deep packet inspection fields.
Every of the next sections will current an analytic for detecting exfiltration through DNS queries within the corresponding device set.
Implementing the Analytic through SiLK
Determine 1 beneath presents a collection of SiLK instructions to implement an analytic to detect exfiltration. The primary command applies a filter to regular, benign DNS visitors, isolating DNS visitors (recognized by protocol recognition as indicated by the appliance label of 53) coming from the inner community (classless inter-domain routing [CIDR] block 192.168.0.0/16) and of comparatively lengthy (70 bytes or extra) packets. The output of the filter is then summarized by vacation spot handle and transport protocol, counting bytes, circulation information, and packets for every mixture of handle and protocol. The ensuing counts are solely proven if the gathered bytes are 500 or extra. After making use of the analytic to benign DNS information, it’s utilized within the second sequence to DNS information encompassing compressed information for exfiltration.
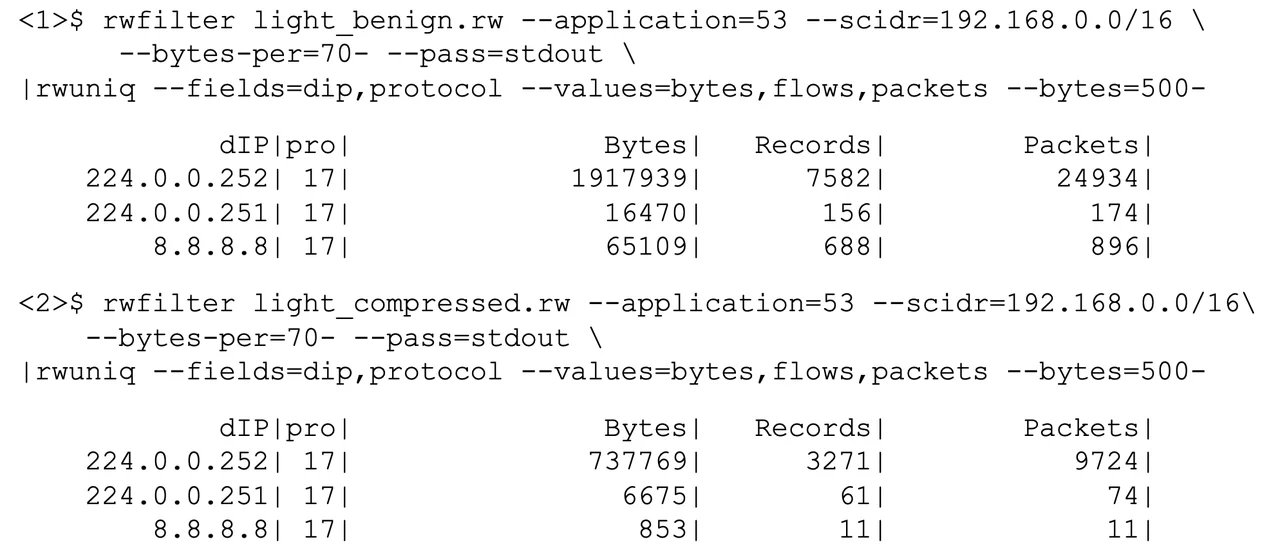
Determine 1: SiLK Analytic and Outcomes
The leads to Determine 1 present that the community talks to a main DNS server, a secondary DNS server, and a public server. Within the benign case, the info is principally directed to the first DNS server and the general public server. Within the exfiltration case, the info is principally directed to the first DNS server and the secondary DNS server. This shift of vacation spot, in isolation, is just not sufficient to make the exfiltration visitors suspicious or present a foundation for shifting past suspicion into investigation. Within the benign case, there’s a notable fraction of the visitors directed to the general public DNS server at 8.8.8.8. Within the visitors labeled as abusive, this fraction is lessened, and the fraction to a non-public DNS server (the exfiltration goal) at 224.0.0.252 is elevated. Sadly, given the restricted nature of SiLK circulation information, safety analysts have a tough time exfiltrating further visitors. To go additional, extra DNS-specific fields are required. These fields are offered by deep packet inspection (DPI) information in expanded circulation information in IPFIX format. Whereas SiLK can not course of IPFIX circulation information, different instruments reminiscent of Mothra and databases can.
Implementing the Analytic through Mothra
The code pattern beneath exhibits the analytic applied in Spark utilizing the Mothra libraries. These libraries permit definition and loading of knowledge frames with community circulation document information in both SiLK or IPFIX format. An information body is a assortment of knowledge organized into named columns. Knowledge frames may be manipulated by Spark features to isolate flows of curiosity and to summarize these flows. Defining the info frames entails figuring out the columns and the info to populate the columns. Within the code pattern, the info frames are outlined by the spark.learn.area perform and populated by information from both the captured benign visitors or the captured exfiltration visitors through Mothra’s ipfix perform. Collectively, these features set up the information information body.
The consequence information body is constructed from the information information body through a collection of filtering and summarization features. The preliminary filter restricts it to visitors labeled as DNS visitors, adopted by one other filter that ensures the information include DNS useful resource document queries or responses. The choose perform that follows isolates particular document options for summarization: time, visitors supply and vacation spot, byte and packet volumes, DNS names, DNS flags, and DNS useful resource document varieties. The groupBy perform generates the summarization for every distinctive DNS identify and useful resource document sort mixture. The agg perform specifies that the summarization include the rely of circulation information, the counts of supply and vacation spot IP addresses, and the totals for bytes and packets. The filter perform (after the summarization) restricts output to simply these displaying a bytes-per-packet ratio of greater than 70 with fewer than three entries within the DNS Title checklist. This final filter excludes summarizations of visitors that’s massive solely because of the size of the response checklist quite than to the size of particular person queries.
This filtering and summarization course of creates a profile of enormous DNS requests and responses (separated by DNS flag values). The usage of DNS names as a grouping worth permits the analytic to tell apart repeated queries to comparable domains. The counts of supply and vacation spot IP addresses permit the analyst to tell apart repeated visitors to some areas as an alternative of uncommon visitors to a number of areas or from a number of sources.
val data_dir = ".../path/to/information"
import org.cert.netsa.mothra.datasources._
import org.cert.netsa.mothra.datasources.ipfix.IPFIXFields
import org.apache.spark.sql.features._
// In dnsIDBenign.sc:
val data_file = s"$data_dir/light_benign.ipfix"
// In dnsIDAbuse.sc:
// val data_file =
// s"$data_dir/light_compressed.ipfix"
val information = {
spark.learn.fields(
IPFIXFields.default, IPFIXFields.dpi.dns
).ipfix(data_file)
}
val consequence = {
information
.filter(($"silkAppLabel" === 53) &&
(dimension($"dnsRecordList")>0))
.choose(
$"startTime",
$"sourceIPAddress",
$"destinationIPAddress",
$"octetCount",
$"packetCount",
$"dnsRecordList.dnsRRType" as "dnsRRType",
$"dnsRecordList.dnsQueryResponse" as "dnsQR",
$"dnsRecordList.dnsResponseCode" as "dnsResponse",
$"dnsRecordList.dnsName" as "dnsName")
.groupBy($"dnsName",$"dnsRRType")
.agg(rely($"*") as "flows",
countDistinct($"sourceIPAddress") as "#sIP",
countDistinct($"destinationIPAddress") as "#dIP",
sum($"octetCount") as "bytes",
sum($"packetCount") as "packets")
// .filter($"packets" > 20)
.filter($"bytes"/$"packets" > 70)
.filter(dimension($"dnsName") < 3)
.orderBy($"bytes".desc)
}
consequence.present(20,false)The code pattern beneath exhibits the output of dnsIDExfil.sc on benign and on compressed information, the info units used within the previous SiLK dialogue. The presence of multicast (224/8 and 239/8 CIDR blocks) and RFC1918 non-public addresses (192.168/16 CIDR blocks) is because of this information coming from a man-made assortment surroundings as an alternative of dwell Web visitors seize.
Contrasting the benign output in opposition to the abuse output, we see a smaller variety of lookup addresses being queried within the abuse outcomes and a a lot faster drop-off within the variety of queries per host. Within the benign outcomes, there are six DNSNames which are queried repeatedly; within the abuse outcomes, there are two. The entire queries proven are PTR (reverse. RRType=12) queries, and all are going to the identical server. Within the high-volume DNSName queries, the utmost common packet size is barely bigger for the abuse information than for the benign information (81 vs. 78). Taken collectively, these variations present a slow-and-steady launch of further information as a part of the DNS information switch, which displays the file switch happening.
dnsIDBenign.sc output:
+-------------------------------------+---------+-----+----+----+------+-------+
|dnsName |dnsRRType|flows|#sIP|#dIP|bytes |packets|
+-------------------------------------+---------+-----+----+----+------+-------+
|[252.0.0.224.in-addr.arpa.] |[12] |2835 |1 |1 |416539|5901 |
|[150.20.168.192.in-addr.arpa.] |[12] |982 |1 |1 |242585|3125 |
|[200.20.168.192.in-addr.arpa.] |[12] |895 |1 |1 |134756|1836 |
|[15.20.168.192.in-addr.arpa.] |[12] |901 |1 |1 |133490|1844 |
|[100.20.168.192.in-addr.arpa.] |[12] |757 |1 |1 |112173|1533 |
|[2.20.168.192.in-addr.arpa.] |[12] |635 |1 |1 |91734 |1288 |
|[3.20.168.192.in-addr.arpa.] |[12] |315 |1 |1 |45438 |640 |
|[_ipps._tcp.local., _ipp._tcp.local.]|[12, 12] |122 |32 |1 |13161 |136 |
|[250.255.255.239.in-addr.arpa.] |[12] |74 |1 |1 |11328 |152 |
|[101.20.168.192.in-addr.arpa.] |[12] |31 |1 |1 |4666 |64 |
+-------------------------------------+---------+-----+----+----+------+-------+
solely displaying prime 10 rows
dnsIDAbuse.sc output:
+-------------------------------------+---------+-----+----+----+------+-------+
|dnsName |dnsRRType|flows|#sIP|#dIP|bytes |packets|
+-------------------------------------+---------+-----+----+----+------+-------+
|[252.0.0.224.in-addr.arpa.] |[12] |1260 |1 |1 |191398|2696 |
|[2.20.168.192.in-addr.arpa.] |[12] |255 |1 |1 |130725|1615 |
|[150.20.168.192.in-addr.arpa.] |[12] |416 |1 |1 |63606 |866 |
|[200.20.168.192.in-addr.arpa.] |[12] |388 |1 |1 |57686 |788 |
|[15.20.168.192.in-addr.arpa.] |[12] |379 |1 |1 |56492 |781 |
|[100.20.168.192.in-addr.arpa.] |[12] |340 |1 |1 |50738 |694 |
|[3.20.168.192.in-addr.arpa.] |[12] |125 |1 |1 |17750 |250 |
|[250.255.255.239.in-addr.arpa.] |[12] |32 |1 |1 |4736 |64 |
|[_ipps._tcp.local., _ipp._tcp.local.]|[12, 12] |46 |30 |1 |4467 |51 |
|[_ipp._tcp.local., _ipps._tcp.local.]|[12, 12] |13 |9 |1 |1782 |19 |
+-------------------------------------+---------+-----+----+----+------+-------+
solely displaying prime 10 rowsUnderstanding Knowledge Exfiltration
Whichever type of tooling is used, analysts typically want an understanding of the info transfers from their community. Repetitive queries for DNS decision needs to be quite uncommon—caching ought to eradicate many of those repetitions. As repetitive queries for decision are recognized, a number of teams of hosts could also be discovered:
- Hosts that generate repetitive queries not indicative of exfiltration of knowledge are more likely to exist, characterised by very constant question dimension, periodic timing, and the usage of anticipated identify servers.
- Hosts that generate repetitive queries with uncommon identify servers or timing could require additional investigation.
- Hosts that generate repetitive queries with uncommon identify servers or question sizes needs to be examined rigorously to determine potential exfiltration.
The affect of those hosts on community safety will range relying on the vary and criticality of property these hosts entry, however among the visitors could demand speedy response.
What May a Safety Analyst Wish to Know
This publish is a part of a collection addressing a easy query: What would possibly a safety analyst wish to know in the beginning of every shift concerning the community? In every publish we are going to focus on one reply to this query and software of quite a lot of instruments which will implement that reply. Our aim is to offer some key observations that assist analysts monitor and defend their networks, specializing in helpful ongoing measures, quite than these particular to at least one occasion, incident, or concern.
We is not going to give attention to signature-based detection, since there are a selection of sources for such together with intrusion detection methods (IDS)/intrusion prevention methods (IPS) and antivirus merchandise. The instruments utilized in these articles will primarily be a part of the CERT/NetSA Evaluation Suite, however we are going to embrace different instruments if useful. Earlier posts examined instruments for monitoring software program updates and proxy bypass.
Our method can be to spotlight a given analytic, focus on the motivation behind the analytic, and supply the appliance as a labored instance. The labored instance, by intention, is illustrative quite than exhaustive. The choice of what analytics to deploy, and the way, is left to the reader.
If there are particular behaviors that you simply wish to counsel, please ship them by e mail to netsa-help@cert.org with “SOC Analytics Thought” within the topic line.
[ad_2]