
[ad_1]
In right now’s quickly evolving IT panorama, Cloud Service Suppliers want to make sure that their prospects have entry to the newest and most superior networking and safety features. VMware Cloud Director (VCD) permits prospects to construct safe non-public clouds, dramatically growing knowledge middle effectivity and enterprise agility.
Mixed with VMware NSX (beforehand NSX-T Knowledge Heart or NSX-T), VMware’s software-defined networking platform, the result’s a robust resolution for service suppliers and enterprises to help the rising variety of distributed purposes being run on heterogenous endpoints, VMs, containers, and naked steel throughout DC, Cloud, and Edge.
Why ought to we migrate VMware Cloud Director to VMware NSX (NSX-T)?
As per the present newest model (10.4.2), VCD nonetheless helps two choices for community virtualization: NSX Knowledge Heart for vSphere (NSX-V) and VMware NSX (formally often called NSX-T Knowledge Heart or NSX-T). Nonetheless, NSX-V reached its Finish of Normal Assist (EoGS) is January 16, 2022, and technical steerage on January 16, 2023. Subsequently organizations should take proactive steps to mitigate safety dangers, preserve compliance, and proceed to leverage the advantages of community virtualization.
The migration course of might be advanced and needs to be deliberate and executed fastidiously to attenuate disruption and guarantee a profitable transition. Lately, VMware has launched model 1.4.2 of the VMware NSX Migration for VMware Cloud Director instrument, enhancing the help of VCD networking options and permitting V2T migrations with minimal downtime.
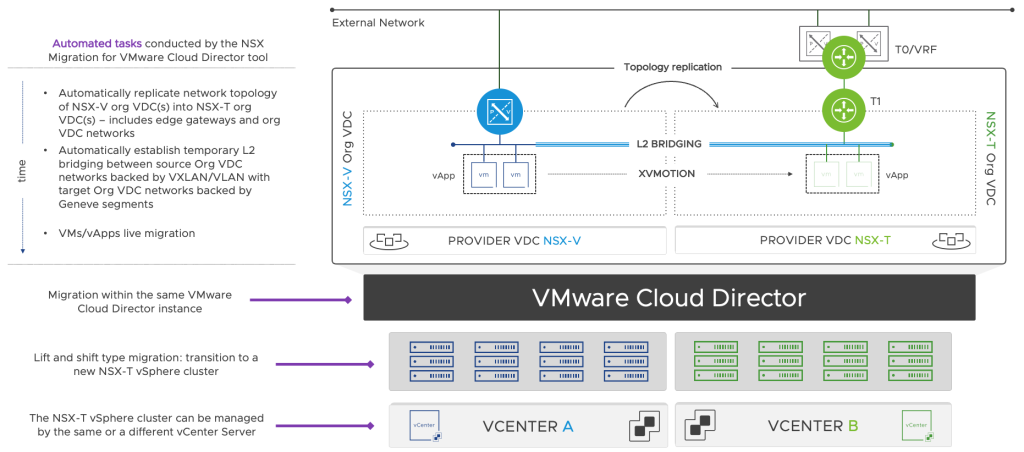
VCD V2T Options and Migration Matrix
To assist Cloud Service Suppliers plan for a clean transition, this quick weblog gives info on the present VCD NSX Options Assist Matrix and people that may be auto-migrated utilizing the newest NSX Migration for VCD instrument (1.4.2).
| Function | NSX Knowledge Heart for vSphere (NSX-V) | VMware NSX (NSX-T) | NSX Migration for VCD instrument |
|---|---|---|---|
| Overlay community backing | VXLAN | GENEVE | Sure |
| Distributed Routing | Sure | Sure | Sure |
| Non-Distributed Routing | Sure | Sure (10.3.2) | Sure |
| Exterior Community | Port teams; Logical Switches (digital wires) | Port teams; NSX Segments; Connection to exterior networks from Edge GW (10.4.1) | Sure |
| Supplier Gateway | Not Relevant (N/A) | T0/VRF for Edge GW egress | Sure |
| Routed Community with NAT | Sure | Sure | Sure |
| Routed Community no NAT | Sure | Commercial of routed community requires devoted Supplier GW or IP Areas. | Sure |
| Remoted Community | Sure | Sure | Sure |
| Direct Community | Sure | Sure | Sure |
| Imported Community | Unsupported | Sure | N/A |
| Shared Community | Sure | With Knowledge Heart Teams for non-directly linked Org VDC networks | Sure |
| IPv6 Community | Sure | Sure | Sure |
| Twin Stack (IPv4/IPv6 on similar vNIC) | Sure | Sure | Sure |
| Org VDC Edge GW | ESG | Tier-1 Gateway | Sure |
| IP tackle sub-allocation | Supplier managed | Supplier managed or self-service with IP Areas | Sure |
| Edge Firewall | Sure | Sure | Sure |
| NAT (NAT44) | Sure | Sure | Sure |
| NAT64 | Sure | Unsupported | N/A |
| DHCP | Sure | Sure | Sure |
| DHCPv6 | Unsupported | Sure | N/A |
| DNS Forwarding | Sure | Sure | Sure |
| BGP IPv4 | Sure | The Supplier GW should be non-public to a company or devoted to Tenant’s Edge GW. | Sure |
| BGP IPv6 | Unsupported | Sure | N/A |
| OSPF | Sure | Unsupported | N/A |
| VRF Lite | Unsupported | Sure | Sure |
| Static Routes | Sure | Static routes solely on Tier-1 GW, however not on Tier-0/VRF (10.4) | Sure |
| Coverage-Primarily based IPsec VPN | Sure | Sure | Sure |
| Route-Primarily based IPsec VPN | Sure | Unsupported | N/A |
| L2 VPN | Sure | Sure (10.3) | NSX-T L2VPN isn’t backwards appropriate with NSX-V L2VPN. The configuration of all L2VPN endpoints should be migrated manually. |
| SSL VPN | Sure | Unsupported by NSX-T. SSL VPN alternate options might be deployed, and the configuration migrated manually. Please verify the VMware Cloud Director Distant Entry VPN Integration Information. | N/A |
| Load Balancing | Sure | Requires NSX Superior Loadbalancer (Avi) | Sure |
| IPv6 Load Balancing | Sure | Requires NSX Superior Loadbalancer (Avi) (10.4) | Sure |
| Edge logging and CLI | Sure | NSX-T Edge node is shared. CLI isn’t out there. Centralized logging with potential filtering. No tenant-dedicated logging. | N/A |
| Edge HA | Sure (Non-obligatory Energetic/Standby) | Sure | Sure |
| vApp Edge (routing, NAT, firewall) | Sure | Sure (10.3) Routed vApps can’t be linked to VLAN-backed Org VDC community |
Sure |
| vApp Edge Fencing | Sure | Unsupported | N/A |
| Distributed Firewall (L3/L4 and L7) | Sure | Requires VCD Knowledge Heart Group | Sure |
| Distributed Firewall (L2) | Sure | Unsupported | N/A |
| Cross VDC Networking (similar VCD) | Sure | Requires VCD Knowledge Heart Group; single egress solely | Unsupported |
| Cross VDC Community (completely different VCDs) | Sure | Unsupported | N/A |
| Edge placement | Sure (through API) | Edge Cluster granularity and through failure domains in NSX-T | Sure |
| Edge gateway fee limiting | Sure (exterior community granularity) | On the Edge GW stage (10.3.2). NSX-T Gateway Ingress/Egress QoC Profiles |
Sure |
| Exterior community metering | Sure | Sure with Aria Operations | N/A |
| Section Profile | Unsupported | Sure | N/A |
Are you interested by studying extra about NSX Migration for VCD instrument and course of? Do you might want to carry out a VCD NSX migration? Beneath are some reference assets that will help you all through the transition.
Docs and Blogs
Webinar Sequence
- Shut the Technical NSX V to NSX T Expertise Hole
- Half 1 Sequence: Modernize Your NSX Surroundings (3 Episodes, Degree 100-300) Watch now on-demand
- Half 2 Sequence: Migrating Complicated NSX-v Architectures (4 Episodes Degree 300-400). Register for July 11-19 Sequence AMER/EMEA or APJ
Demos:
Conclusion
Whereas VMware NSX Knowledge Heart for vSphere (6.4.x) continues to perform previous its EoGS date, bug fixes and safety patches for the particular model are discontinued. This could expose the infrastructure to vulnerabilities, making it essential for organizations to plan and execute an NSX-V to NSX-T transition for VMware Cloud Director environments.
As well as, migrating to NSX-T will preserve a robust integration to your VMware Cloud Director platform whereas enabling larger enterprise agility, cloud scalability, and community efficiency by supporting fashionable distributed apps with a whole networking and safety stack.
Use the vcd-v2t-assist channel within the VMware Cloud Supplier Slack workspace for additional questions or to supply your V2T migration expertise and suggestions. Moreover, the next FAQ solutions widespread questions in regards to the VMware NSX Migration for VMware Cloud Director.
[ad_2]