[ad_1]
Image a cybersecurity panorama the place defenses are impenetrable, and threats are nothing greater than mere disturbances deflected by a powerful protect. Sadly, this picture of fortitude stays a pipe dream regardless of its comforting nature. Within the safety world, preparedness isn’t just a luxurious however a necessity. On this context, Mike Tyson’s well-known adage, “Everybody has a plan till they get punched within the face,” lends itself to our enviornment – cyber defenses should be battle-tested to face an opportunity.
Tyson’s phrases seize the paradox of readiness in cybersecurity: too usually, untested cyber defenses can create a false sense of safety, resulting in dire penalties when actual threats land a blow. That is the place Breach and Assault Simulation (BAS), a proactive software in any group’s cybersecurity arsenal, comes into play.
When Cybersecurity Meets the Punch – The Assumption Downside
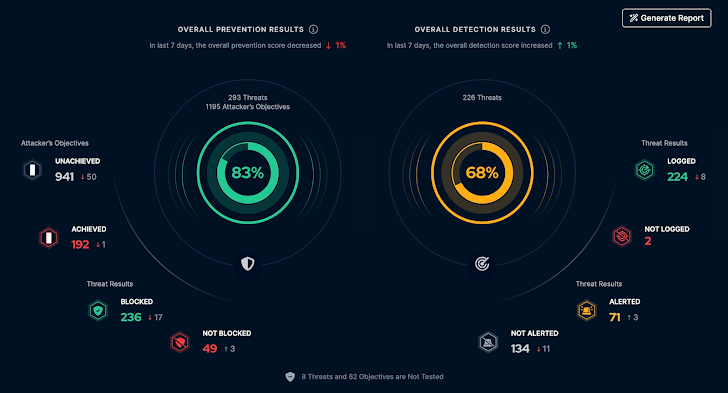
Assumptions are the hidden icebergs in cybersecurity’s huge ocean. Though we would consider our safety controls are foolproof, the statistics paint one other image. In keeping with the Blue Report 2023 by Picus, solely 59% of assaults are prevented, simply 37% detected, and a scant 16% triggered alerts. This knowledge reveals an alarming fact: cybersecurity measures usually fall brief in real-world eventualities. Oftentimes, this shortcoming is because of complexities in configuration and a scarcity of expert professionals, which may result in underperforming and misconfigured defenses. On the similar time, conventional testing strategies like penetration checks and pink crew workout routines cannot absolutely gauge the effectiveness of a corporation’s safety. This may contribute to the usually harmful assumption that safety controls are efficient with out repeatedly stress-testing them in real-world eventualities.
This chasm between perceived and precise safety confirms the rising want for safety validation by way of Breach and Assault Simulation (BAS) – a way of confronting these fallacies by rigorously validating defenses earlier than assaults catch organizations off guard. In the end, BAS tightens the veil of cybersecurity throughout each potential breach.
Shifting the Mindset from Plan to Observe
Cultivating a proactive cybersecurity tradition is akin to shadowboxing, placing concept into movement. Cyber threats morph as swiftly as clouds in a stormy sky, and simulations should be as dynamic because the threats they mimic. This cultural shift begins on the prime, with management championing the embrace of steady safety validation by way of BAS. Solely then can cybersecurity groups embed this practice-centric philosophy, sparring with simulations regularly and with intent.
The Mechanics of BAS
BAS is a actuality examine in your cybersecurity posture. At its core, BAS is the systematic, managed simulation of cyberattacks throughout your manufacturing community. Every simulation is designed to imitate the conduct of precise attackers, cultivating preparedness for adversary ways, strategies, and procedures (TTPs). In keeping with the Pink Report 2023, risk actors use a median of 11 completely different TTPs throughout an assault.
For instance, an APT assault situation begins with preliminary breach strategies, akin to exploiting software program vulnerabilities or phishing emails with malicious attachments. Then, it strikes deeper, making an attempt lateral actions throughout the community, escalating privileges the place attainable, and making an attempt to exfiltrate simulated delicate knowledge. On this situation, the target is to duplicate a whole assault lifecycle with constancy, all whereas analyzing how your safety controls reply at every step.
What’s extra, BAS is not only a one-off train. It is an ongoing course of that adapts because the risk panorama evolves. As new malware variants, TTPs, exploit strategies, APT campaigns, and different rising threats come to mild, they’re included into the BAS software’s risk intelligence library. This ensures that your group can defend itself in opposition to the potential threats of right now and tomorrow.
Following every simulation, BAS instruments present complete analytics and insightful studies. These include essential particulars on how the intrusion was (or wasn’t) detected or prevented, the time it took for the safety controls to reply, and the effectiveness of the response.
Armed with this knowledge, cybersecurity professionals can higher prioritize their response methods, specializing in probably the most urgent gaps of their organizational protection first. They’ll additionally fine-tune present safety controls with easy-to-apply prevention signatures and detection guidelines that may enhance their means to detect, stop, or react to cyber threats.
Integrating the BAS Punch into Your Cyber Technique
Think about that BAS is a constant pulse reinforcing your safety measures. Successfully incorporating BAS into your group’s defenses begins with essential evaluation to find out the way it enhances your cybersecurity structure.
Step 1: Tailor BAS to Your Wants
Customizing BAS in your group begins with understanding the threats you are almost certainly to face – as a result of a financial institution’s main cybersecurity issues differ from a hospital’s. Select simulations that replicate probably the most related threats to your trade and technical infrastructure. Trendy BAS instruments can generate custom-made simulation playbooks with cyber threats almost certainly to have an effect on your group.
Step 2: Create a Simulation Schedule
Consistency is vital. Run BAS simulations recurrently, not simply as a one-time occasion however as an integral a part of your cybersecurity technique. Set up a cadence – whether or not day by day, weekly, month-to-month, or in real-time following vital IT or risk panorama modifications – to stay a step forward of adversaries who repeatedly refine their ways.
Step 3: Apply the Insights
The true worth of BAS lies within the actionable insights derived from simulation outcomes. Superior BAS platforms present sensible suggestions, akin to prevention signatures and detection guidelines that may be straight included into safety controls – together with IPS, NGFW, WAF, EDR, SIEM, SOAR, and different safety options – to strengthen your safety posture instantly.
Step 4: Measure and Refine
Outline quantitative success metrics to guage the affect of BAS in your group’s cybersecurity. This may embrace the ratio of blocked/logged/alerted assaults to all assaults, the variety of addressed defensive gaps, or enhancements in detection and response instances. Repeatedly refine your BAS course of primarily based on these efficiency indicators to make sure your defenses get sharper with every iteration.
Able to Fortify Your Cyber Defenses with the Pioneer of BAS Expertise?
As we unpack the parallels between a boxer’s protection and a corporation’s safety posture, one mantra echoes true: surviving the primary punch is about resilience by way of relentless observe. Right here, we have now demonstrated the essential function BAS performs in cultivating a proactive method to the unpredictability of cyber threats.
Picus Safety pioneered Breach and Assault Simulation (BAS) know-how in 2013 and has helped organizations enhance their cyber resilience ever since. With Picus Safety Validation Platform, your group can count on unparalleled visibility into its safety posture, so you possibly can hone your defenses in opposition to even probably the most subtle cyberattacks.
With Picus, you are not simply reacting; you are proactively countering cyber threats earlier than they affect your operations. Organizations should throw the primary punch, difficult and strengthening their defenses for when the true combat begins. So, gear up; it is time to put your cyber defenses to the take a look at. Go to us at picussecurity.com to e-book a demo or discover our sources.
Observe: This text was written by Dr. Suleyman Ozarslan, co-founder and VP of Picus Labs at Picus Safety, the place simulating cyber threats and empowering defenses are our passions.
[ad_2]