[ad_1]
A brand new info malware pressure referred to as Statc Stealer has been discovered infecting gadgets operating Microsoft Home windows to siphon delicate private and cost info.
“Statc Stealer reveals a broad vary of stealing capabilities, making it a major menace,” Zscaler ThreatLabz researchers Shivam Sharma and Amandeep Kumar mentioned in a technical report printed this week.
“It will possibly steal delicate info from varied net browsers, together with login information, cookies, net information, and preferences. Moreover, it targets cryptocurrency wallets, credentials, passwords, and even information from messaging apps like Telegram.”
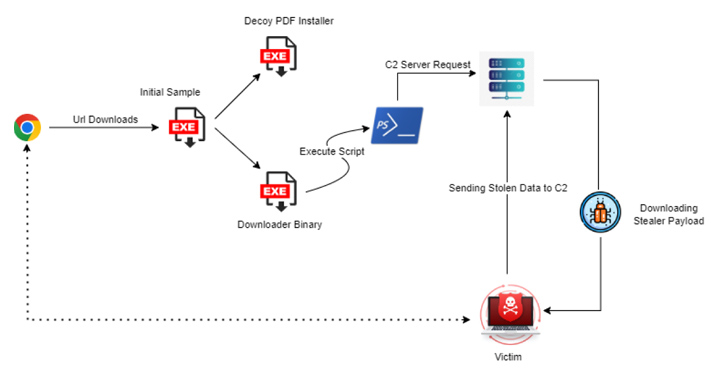
Written in C++, the malicious stealer finds its means into sufferer methods when potential victims are tricked into clicking on seemingly innocuous advertisements, with the stealer imitating an MP4 video file format on net browsers like Google Chrome.

The primary-stage payload, whereas dropping and executing a decoy PDF installer, additionally stealthily deploys a downloader binary that proceeds to retrieve the stealer malware from a distant server through a PowerShell script.
The stealer options refined checks to inhibit sandbox detection and reverse engineering evaluation, and establishes connections with a command-and-control (C&C) server to exfiltrate the harvested information utilizing HTTPS.
One of many anti-analysis features a comparability of the file names to examine for any discrepancies and halt its execution, if discovered. Focused net browsers embrace Google Chrome, Microsoft Edge, Mozilla Firefox, Courageous, Opera, and Yandex Browser.
“The importance of Statc Stealer’s exfiltration method lies in its potential to steal delicate browser information and ship it securely to its C&C server,” the researchers mentioned. “This enables the malware to reap beneficial info, akin to login credentials and private particulars, for malicious functions like id theft and monetary fraud.”
The findings come as eSentire printed an evaluation of an up to date model of Raccoon Stealer, which had its model 2.1 launched earlier this February.

The authors of Raccoon Stealer quickly halted work on the malware final yr following the arrest of Mark Sokolovsky in March 2022, who was uncovered as one of many main builders after he made the deadly mistake of linking a Gmail account he used to enroll in a cybercrime discussion board underneath the alias Photix to an Apple iCloud account, thus revealing his real-world id.
“The up to date model consists of options akin to Sign Messenger information assortment, cleansing from Defender detection (possible altering the code, obfuscation to keep away from detections), and auto brute-forcing for crypto wallets,” eSentire famous final week.
[ad_2]